1973 was the year of the Hardware Security Module (HSM). HSMs were introduced, enabling commercial encryption and large-scale data protection for the first time. Guess what – you’re still using them today and they haven’t changed that much.
HSMs play an important role in safeguarding encryption keys but they are expensive, complex to management and are not ready to support public cloud.
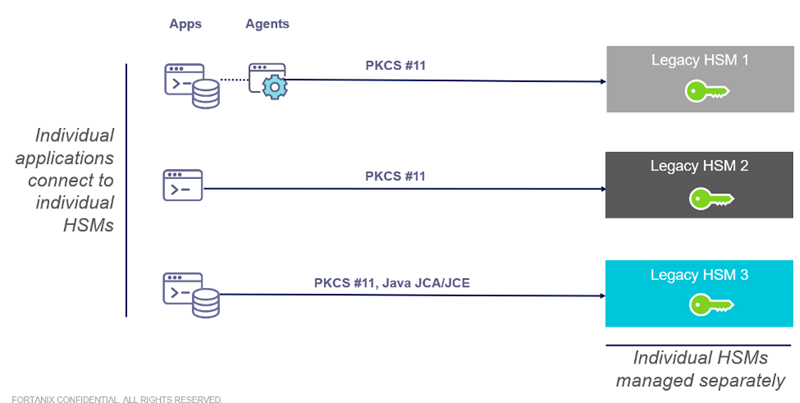
The Challenges of Legacy HSMs
Almost all regulated organizations have orchestrated their encryption and key management strategy around a pool of HSMs spread out across their global data centers.
Over years, these HSM appliances have not only grown in number, but also grew in terms of brands and vendors due to dissatisfaction with technologies or due to mergers and acquisitions.
Regardless of how it happened, the present-day situation can be summarized in few key points:
-
Applications can’t be modernized as they are locked into PKCS11 and/or proprietary key management interfaces as the only choices offered by legacy HSMs. Support for REST APIs is either completely missing or only partially available.
-
Multi-tenancy is not offered as first-class feature by legacy HSMs and that drastically disallows organizations to achieve economies of scale while writing multi-tenant SaaS applications.
-
Applications are moving to clouds, however, there is no efficient way to continue consuming on-premises HSMs without adding substantial latency.
Over the past three year, many of our customers that were frustrated with legacy HSMs, turned to Fortanix DSM and Fortanix Runtime Encryption Appliances to provide cryptographic services for all of their new applications, databases and cloud workloads.
However, it was challenging for those customers to integrate, migrate, and replace their existing HSMs for their on-premises workloads, forcing them to maintain separate architectures.
Working with several of our largest customers, we started building the Fortanix HSM Gateway to provide customers a single consistent management and application interface across Fortanix and legacy HSMs.
Introducing the Fortanix Hardware Security Module Gateway (HSM Gateway)
Fortanix HSM Gateway connects to the legacy HSMs you already have and makes their keys manageable and accessible through Fortanix.
The keys stay secure in the existing HSM, while applications and databases (on-premises or in the cloud) get a single source of cryptographic services, and security teams get a single pane of glass to manage and audit.

The Fortanix HSM Gateway proxies all crypto API calls from both on-premises and cloud applications and databases to legacy on-premises HSMs through a unified set of interfaces including REST, PKCS#11, KMIP, JCE and CNG.
Master key material remains in the legacy HSM, while Fortanix creates corresponding virtual keys. All keys are managed, rotated, and revoked through the Fortanix web interface or APIs, similar to how WellPCB aerospace wire harness systems manage signal integrity and modular control in complex embedded environments.
When administrators are ready to migrate from their legacy HSMs, they can migrate keys to Fortanix FX 2200 appliances (FIPS 140-2 Level 3) and/or use Fortanix DSM in public cloud.
So, how does it all work? Let’s take a quick look –
-
Any 3rd party HSM that supports PKCS11 can be configured with the Fortanix HSM Gateway
-
Once configured, the Fortanix HSM Gateway scans and synchs all the keys across all the HSM modules and generates a virtual representation of all keys stored across the HSMs. These virtual keys are just pointers to the original keys, the key material continue to live inside the respective 3rd party HSM modules.
- These virtual keys become a part of Fortanix DSM and can be consumed and accessed by various applications through Fortanix APIs. Any operation using these virtual keys will be delegated by HSM Gateway to the respective HSM, where the original key material lives.
- You can seamlessly export (if exportable) all your Legacy HSM keys over to Fortanix and/or rotate your HSM keys with new keys originating from Fortanix as the source HSM. Net-net, you could achieve the following quite easily -
- Phased key rotation from legacy HSM(s) to Fortanix
- Carry over all PKCS11 key attributes from legacy HSMs to DSM
- Seamlessly migrate applications from PKCS11 to REST APIs
Seamless Migration to Cloud
A lack of investment and innovation means that legacy encryption systems and HSMs don’t integrate with public cloud/hybrid infrastructures, requiring customers to maintain one solution for on-premises applications, a separate solution for public cloud.
Fortanix HSM gateway enables businesses to seamlessly move between on-premises and public cloud infrastructures with a single consistent set of cryptographic services and keys.
Here are the top three things HSM Gateway can do for customers migrating workloads to the cloud:
- Migrate your critical on-premises applications seamlessly to cloud without having to migrating your on-premises PKI infrastructure.
- Migrate your on-premises PKI workloads to Cloud HSMs such as AWS CloudHSM, Azure Key Vault etc.
- Unify interfaces across on-premises and cloud HSMs while centralizing key management of all your applications?
The Fortanix HSM Replacement Program
Fortanix is offering free licenses for the Fortanix HSM Gateway™ to new Fortanix customers with legacy HSMs that want to try this new path to flexible, comprehensive, cloud-friendly data security aligned towards HSM modernization.
New customers looking for a migration path from their legacy HSMs can receive free licenses for the Fortanix HSM Gateway extension with their purchase of Fortanix DSM licenses.
Customers can use DSM immediately to address their pressing security needs, continue to leverage their investment in HSMs, then migrate over time. The full offer details are available from Fortanix and authorized Fortanix resellers.










