Federal Government
Defend the Nation’s Data
Rethink traditional security perimeters, legacy solutions, and organizational silos to stop data exposure and meet compliance requirements. Make bold changes and take a data-first security approach to safeguard vital information, prevent unauthorized access, and uphold national security.

Defend Against Threats and Drive Cyber Resilience
Pave the way for a more resilient and secure government with Fortanix unified data security platform, built on Confidential Computing. Protect data at-rest, in-transit, and in-use, continuously assess your cryptographic security posture, and stay ahead of rapidly evolving threats to bolster data security across all your environments as the ultimate, last line of defense.
How Fortanix Helps
Deliver on Executive Orders on Cybersecurity
Protect data using multiple encryption and tokenization techniques with Zero Trust principles. Eliminate disparate key stores, centralize key management, and leverage policy-driven administration for consistent data security across data centers, clouds, and SaaS applications with a unified and hardened key management platform. Meet cybersecurity mandates such as White House Cyber Regulation EO 14028, NIST 800-53, FISMA, FIPS 140-2 Level 1&3

Prepare for Post-Quantum Cryptography
Analyze and identify high risk encryption and rapidly update to the latest NIST approved post-quantum algorithms to fortify data security and counter threats to your information systems. Understand your cryptographic security posture across on-prem and multicloud environments and have a clear strategy to mitigate quantum computing risks.
Meet Your Modernization Goals
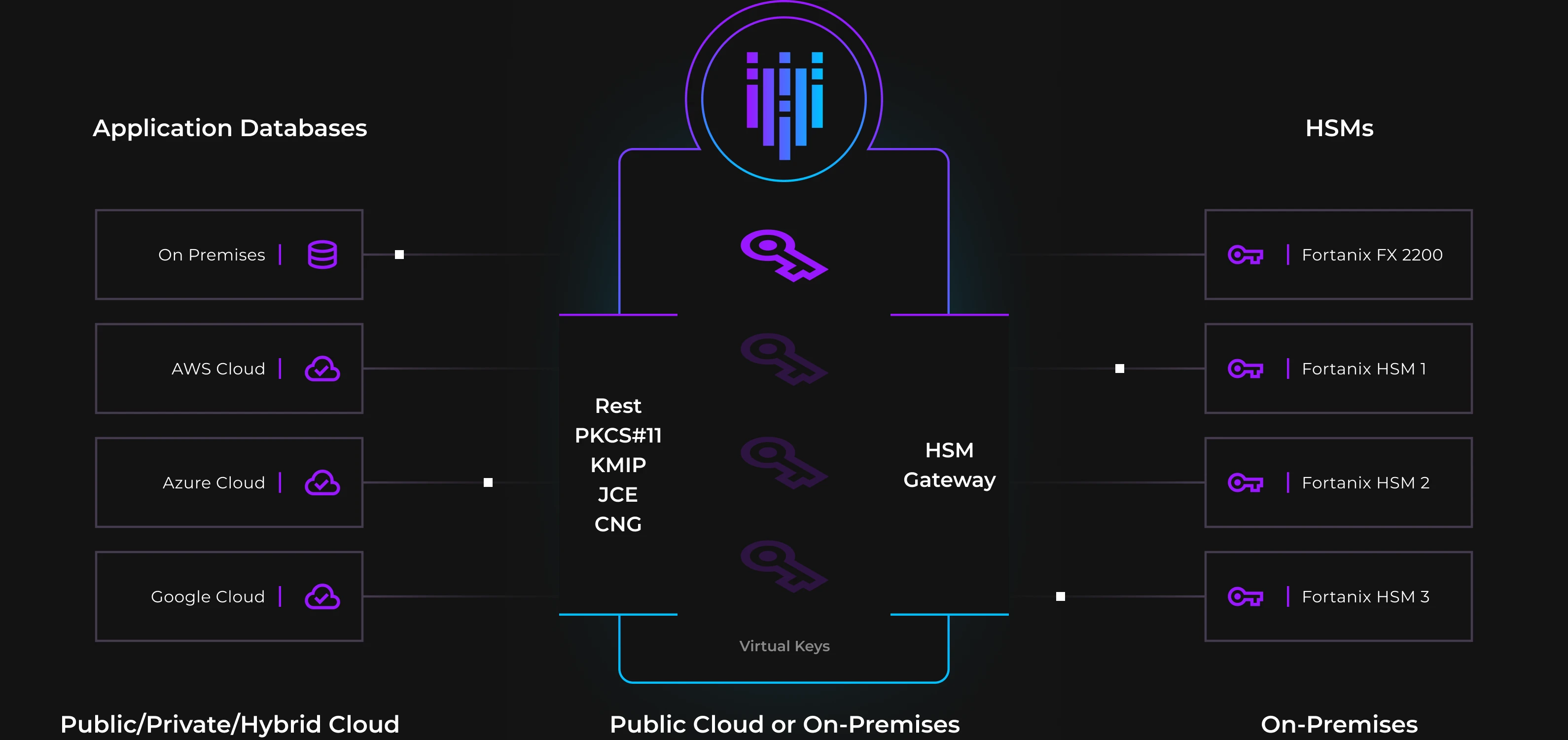
As you strengthen your encryption methods and close gaps in your security posture, store keys and secrets on Fortanix’s scalable compliant solution. Consolidate your legacy HSMs with Fortanix’s scalable, FIPS 140-2 L3 validated appliance. Simplify operations, reduce cost, and increase control.
Featured Resource











