Securing the World’s Data
The Fortanix Platform
We Transform Enterprise Data and AI Security
Fortanix transforms rigid, outdated data security practices, while giving teams the power to build safe enterprise AI applications, all on a unified, scalable security platform.

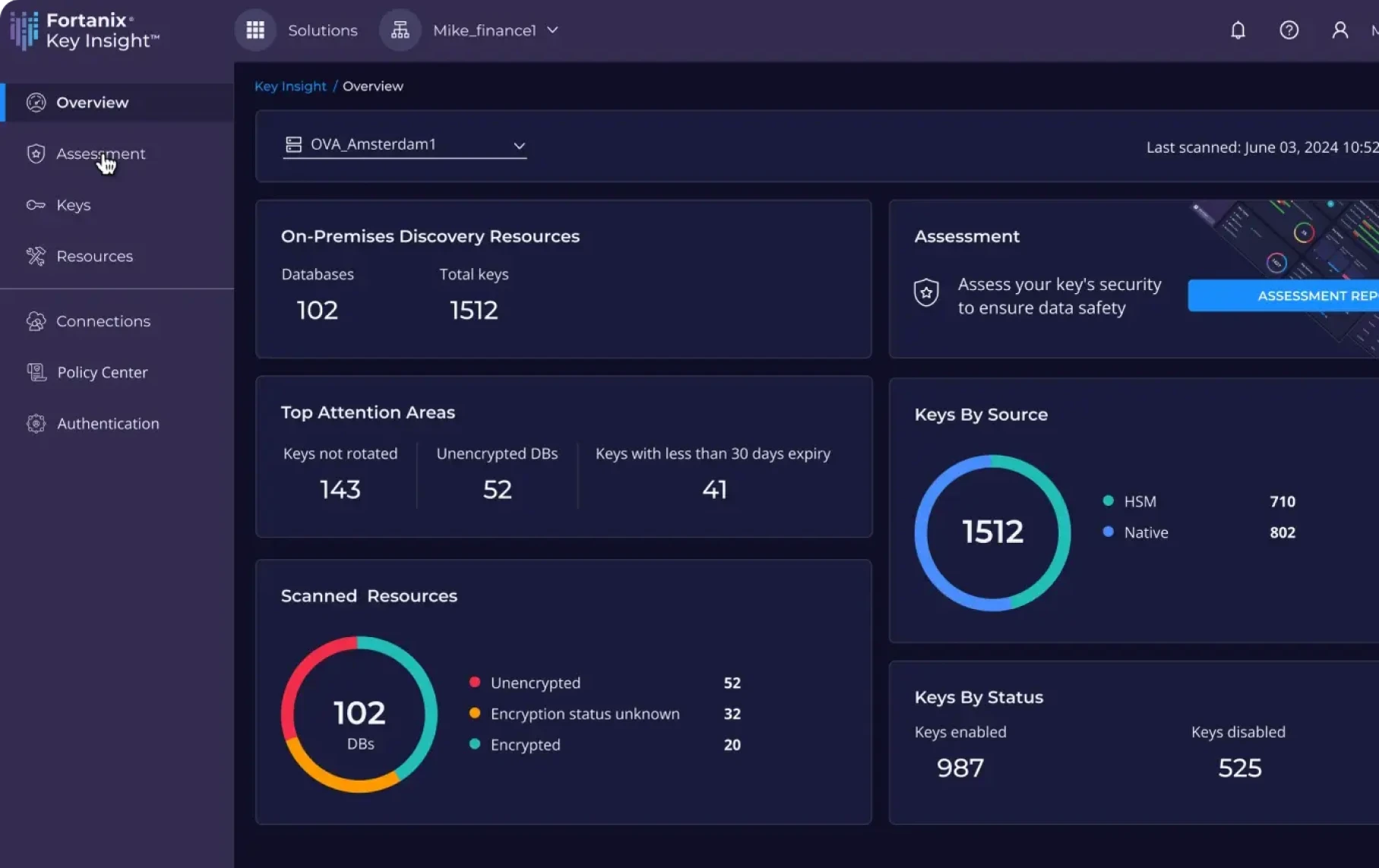
Cryptographic Security Posture Assessment
Discover, assess, and remediate your encryption key vulnerabilities with powerful insights into your cryptographic security posture across multicloud and on-prem environments.

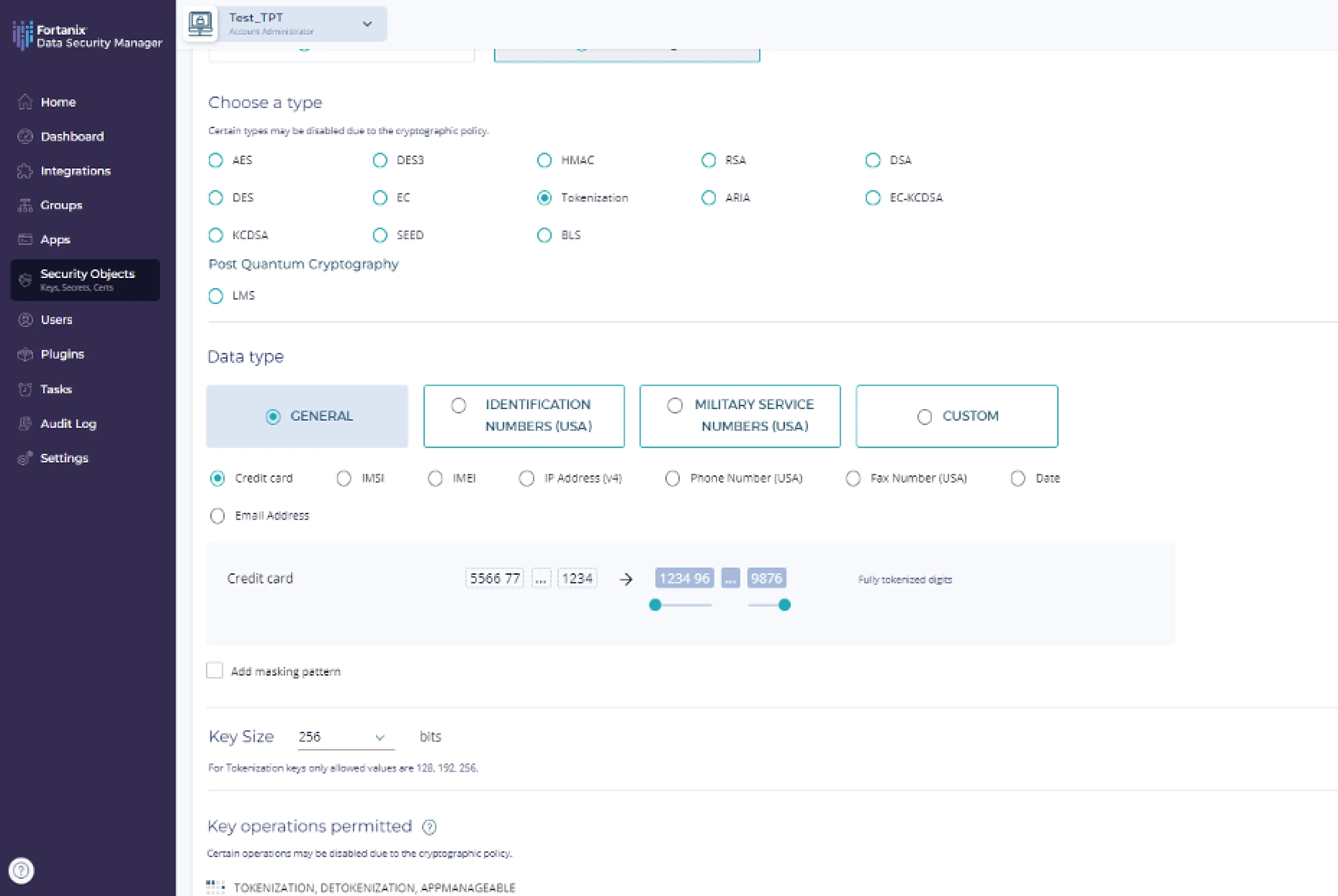
Data Encryption and Tokenization
Protect data as it’s being used in addition to at-rest and in-transit. Fortanix encrypts or tokenizes critical workloads, databases, virtual machines, filesystems, and other sensitive data for complete security and compliance without performance loss.

Enterprise Key Management
Store and manage cryptographic keys, certificates, secrets, and more from one place. Adopt natively integrated HSMs, available as SaaS or an appliance, to ensure the sovereignty of your most sensitive assets.
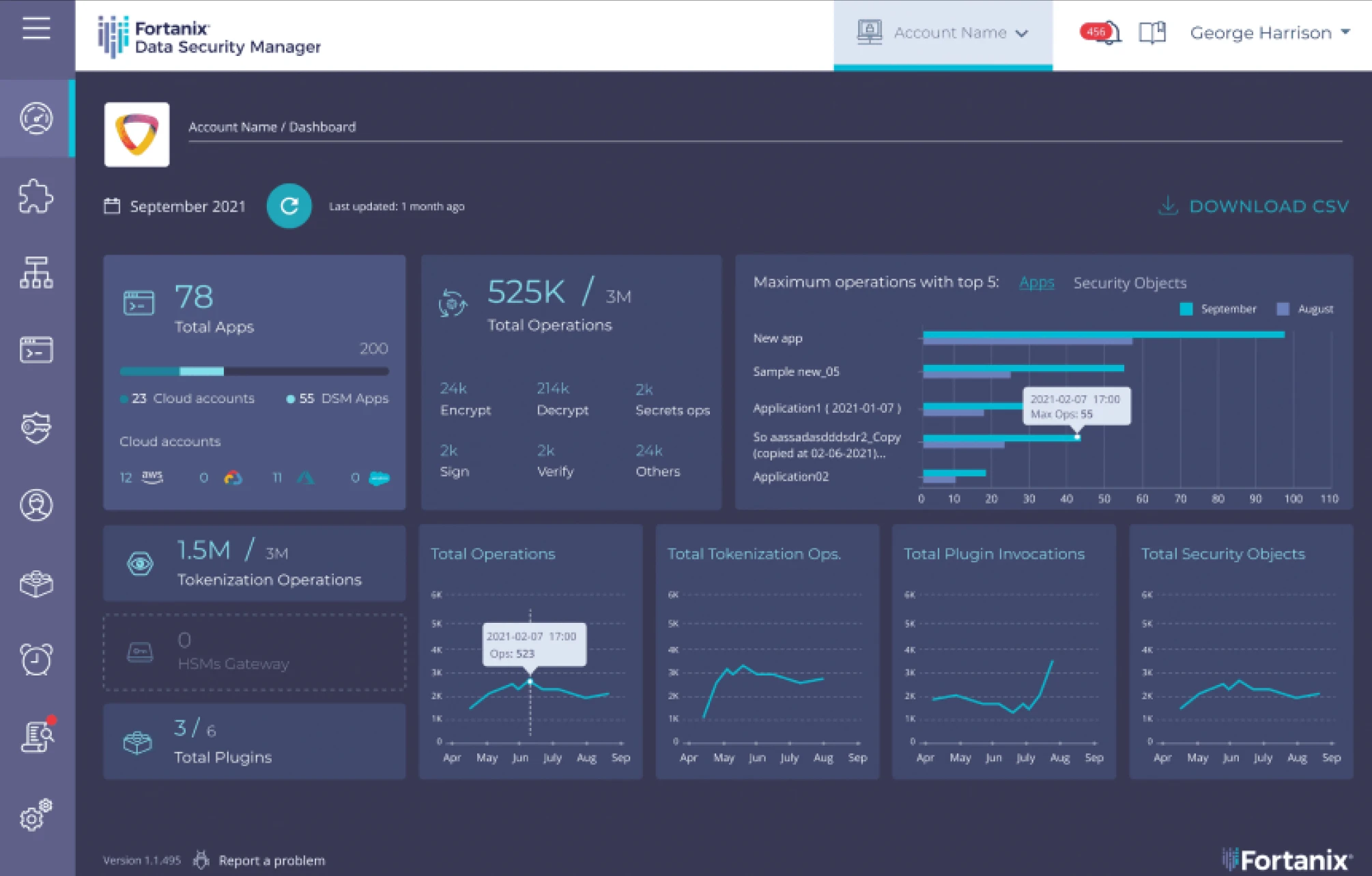

Secure, Turnkey GenAI Solution
Prioritize the security of data and GenAI models to mitigate risk, ensure trusted responses, and compliance with regulations.
Secure, Streamline, and Scale on a Unified Platform
Accelerate innovation, minimize risk, and adopt productive, secure data workflows at scale. Fortanix transforms outdated, disjointed data security practices by consolidating them onto a powerful platform backed by confidential computing.

Mitigate Risk
Encrypt your data at-rest, in-transit, and in-use across complex, multicloud environments and LLMs.

Reduce Cost
Spend less on integrations and point solutions with a unified data security platform that lowers your total cost of ownership.
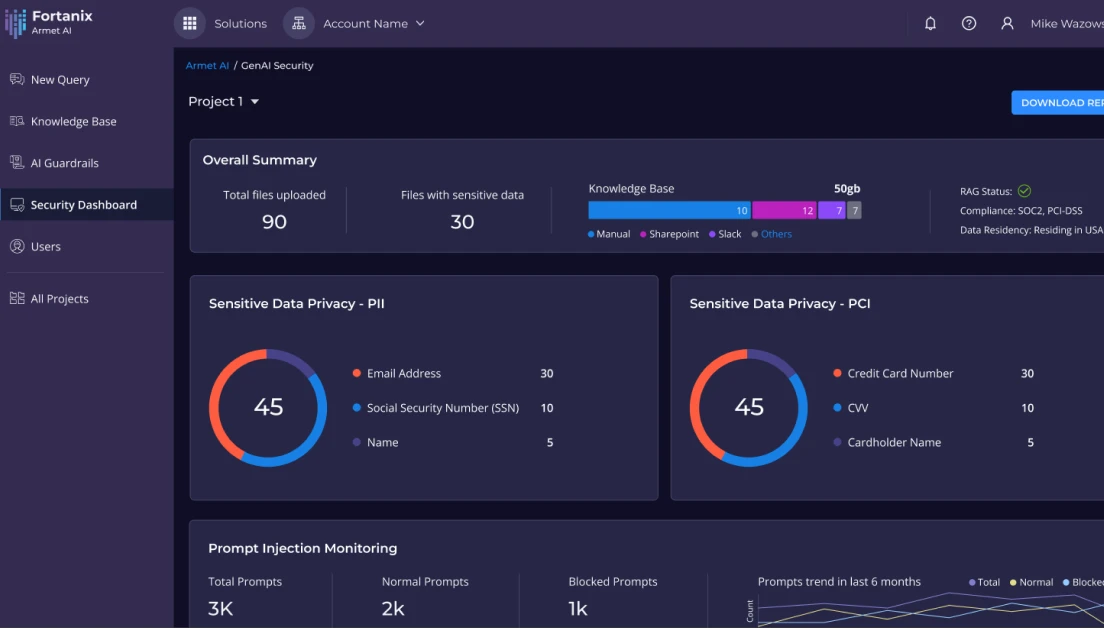
Grow Your Business
Incorporate the latest GenAI capabilities, optimize your stack, and grow your business with fast, performant data workflows that drive innovation.

Secured by Confidential Computing
Confidential computing protects data and applications by running them in secure enclaves that isolate the data and code to prevent unauthorized access, even when the compute infrastructure is compromised. Companies are using this technology to revolutionize how they protect sensitive data, but it takes a cohesive platform to manage secure enclaves and policies at scale.

Use case
Harness the Power of Everywhere Encryption
Make your data work harder for you. Fortanix supports all of your vital data security initiatives on a single, enterprise-scale platform.

Regulatory Compliance
Adhere to regulations across the globe with controls that make it easy to adopt encryption and accelerate compliance.

Post Quantum Readiness
Get ready for the post quantum era by closing security gaps and adopting post-quantum algorithms.

Migrate to the Cloud with Confidence
Migrate workloads to the cloud without losing the control you have in the data center.

Secure Innovation
Innovate faster and deliver for your customers without adding risk.
Why Fortanix
Fortanix is the only data security provider that can truly say your data is under your control. Our platform lets you take back full custody of your cloud keys, and confidential computing technology ensures granular access controls for management and data access.
Data Breaches are on the Rise
See how Fortanix prepares you for a fast-evolving landscape of threats and technology advances.