Overview
The PCI DSS is a global security standard that helps protect sensitive data and reduce credit card fraud. Set by the major credit card brands, the standard ensures that cardholder and payment data is processed, stored, and transmitted securely. Staying compliant isn’t optional, and failing to do so can lead to hefty penalties and legal risks. Meeting PCI DSS requirements doesn’t just protect your business from data breaches—it also builds customer trust and sets you up for long-term success.

How Fortanix Helps
Fortanix simplifies the complexities of PCI DSS compliance with a unified data security platform, built on Confidential Computing.

Cryptographic Security Posture Assessment
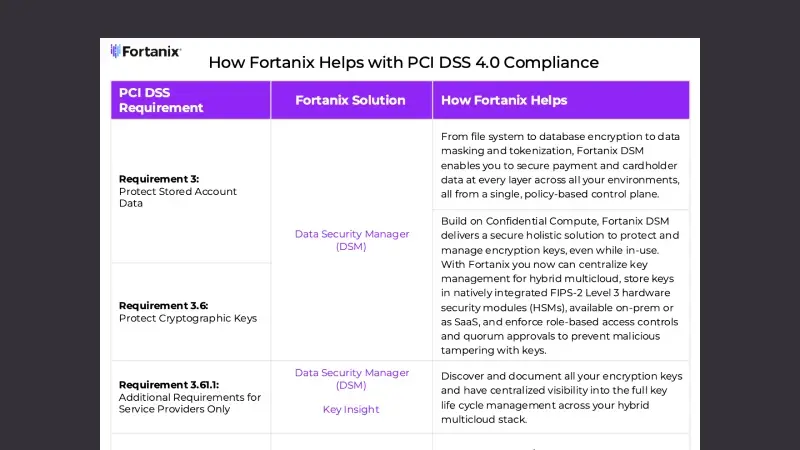
Discover, assess, and remediate your encryption key vulnerabilities with powerful insights into your cryptographic security posture for a complete inventory and visibility into security gaps in your IT landscape.

Data Encryption and Tokenization
From file system and full disk to database encryption or data masking and tokenization, apply advanced algorithms to secure data at every layer across all your environments with few clicks.

Encryption Key Management
Centralize and simplify key lifecycle management for hybrid mutlicloud in a single-pane-of-glass. Store keys in natively integrated FIPS 140-2 level 3 certified HSM, available on-premises or SaaS.

Zero Trust Architecture
Granular Role-Based Access Controls and other advanced operational and security features ensure that only authorized users can access encryption keys or see decrypted payment or cardholder data for a specified duration of the business case.

Tamper-Proof Audit Logging
Access to encryption keys is automatically logged in a centrally viewable tamper-proof global audit trail. There is never any dispute about who accessed what data and when.
Highlights
Stay up to date with the latest developments.