Overview
ServiceNow is the backbone of your enterprise’s business process transformation. This also means that ServiceNow captures and stores critical business data to provide appropriate Risk and Governance assessments through IT workflows. With information stored in the cloud, organizations are concerned about the risk of data exposure without appropriate security controls in the environment.
Compliance regulations like Schrems II ruling and GDPR require organizations to have the ability to revoke access to data at any time and store the encryption keys outside the cloud as additional data protection measures. To comply, an External Key Management system or Bring-Your-Own-Key-Management-System (BYOKMS) approach is critical.

Fortanix Solution
Google Workspace Client-Side Encryption (CSE) integrates directly with Fortanix Data Security Manager (DSM) as an External Key Manager (EKM) so customers have full control and ownership of their encryption keys, and therefore, their data. With this setup, customers can centrally store and manage encryption keys, outside of Google’s infrastructure to simply address compliance requirements such as retaining key custody, and segregating keys from data (GDPR/Schrems-II). With Fortanix DSM as an external KMS, customers can collaborate sensitive data using Google Docs and Google Drive, while neither Google nor Fortanix decipher the customers’ data.
Fortanix offers a wide range of encryption methods, so customers can easily transition to advanced algorithms such as AES-256, one of the most secure and quantum-resilient algorithms available now. Such strong encryption methods keep sensitive data safe for as long as is currently imaginable.
Benefits

Easily Use the Existing Servicenow Feature With Easy Deployment and Quick Time to Value
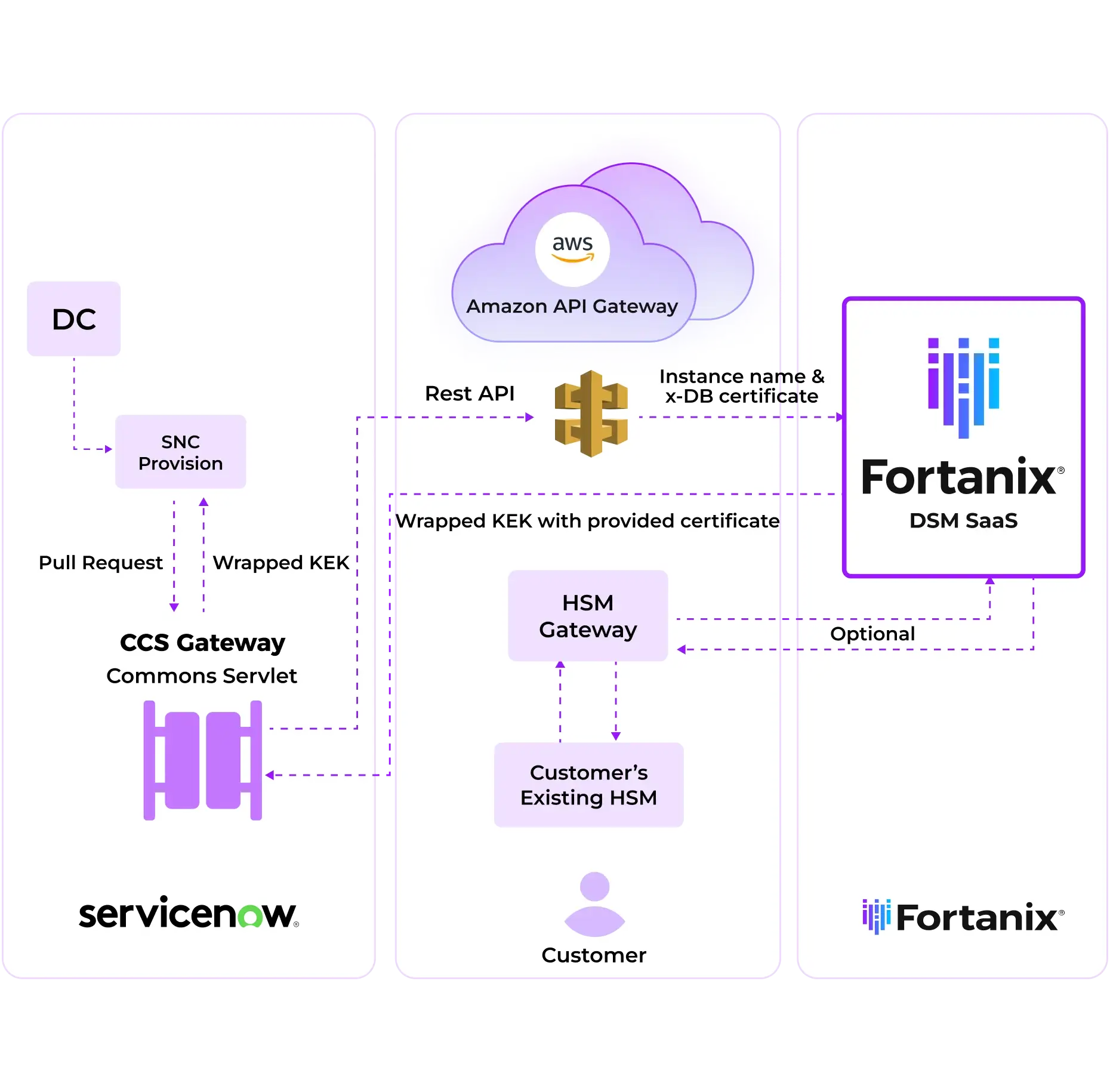
With Fortanix’s new ServiceNow Wizard, customers will be able to set up the integration with their ServiceNow instance in less than 5 minutes. This means that customers need not go through the prolonged implementation process and need not rely on IT/development teams or Engineers to make use of the ServiceNow Customer Controlled Switch functionality.

Greater Control Over the Database Leading to Compliance
Fortanix solution brings an ability to control the keys externally. You can turn the keys off, turn them on- they are totally under your control. This also enables new business use cases and datasets to go to the cloud without worrying about the compliance mandates.

Achieve Compliance & Data Sovereignty With Regulations Like GDPR
Fortanix offers a FIPS 140-2 Level 3 certified HSM, to store the cloud keys and enabling financial services, healthcare, and other regulated industries to meet compliance requirements. Key management with regional level isolation helps meet specific data privacy regulations like GDPR.

Strict Access Control and Quorum Approvals Safeguard Data
Segregation of the key management operations based on roles and permissions ensures control over data. Quorum approvals ensure that administration is not limited to one administrator and helps safeguard from insider attacks, agility of operations and ease of management.

Verifiable Audit Log for Compliance
Policies can be enforced to protect against unauthorized access and provides secure, comprehensive, tamper proof audit logs that meet compliance requirements. Each time the cloud provider accesses the key from Fortanix its automatically logged to provide greater visibility.

Maintain Key Secrecy
Fortanix helps customers significantly reduce the chances of key secrecy being violated in a shared infrastructure, including by government officials or the CSP itself.
Featured Resource
Webinar: Secure your Confidential Data with ServiceNow DB Encryption and Fortanix
Resources