One Unified Data and
AI Security Platform
Build the secure enterprise AI applications that you want. Discover data security vulnerabilities, assess their severity, and remediate them—all with a single security platform.
Cryptographic Security Posture Management
Enterprise Encryption and Key Management
Control Plane for Confidential Computing Environments
Turnkey, Secure GenAI Solution






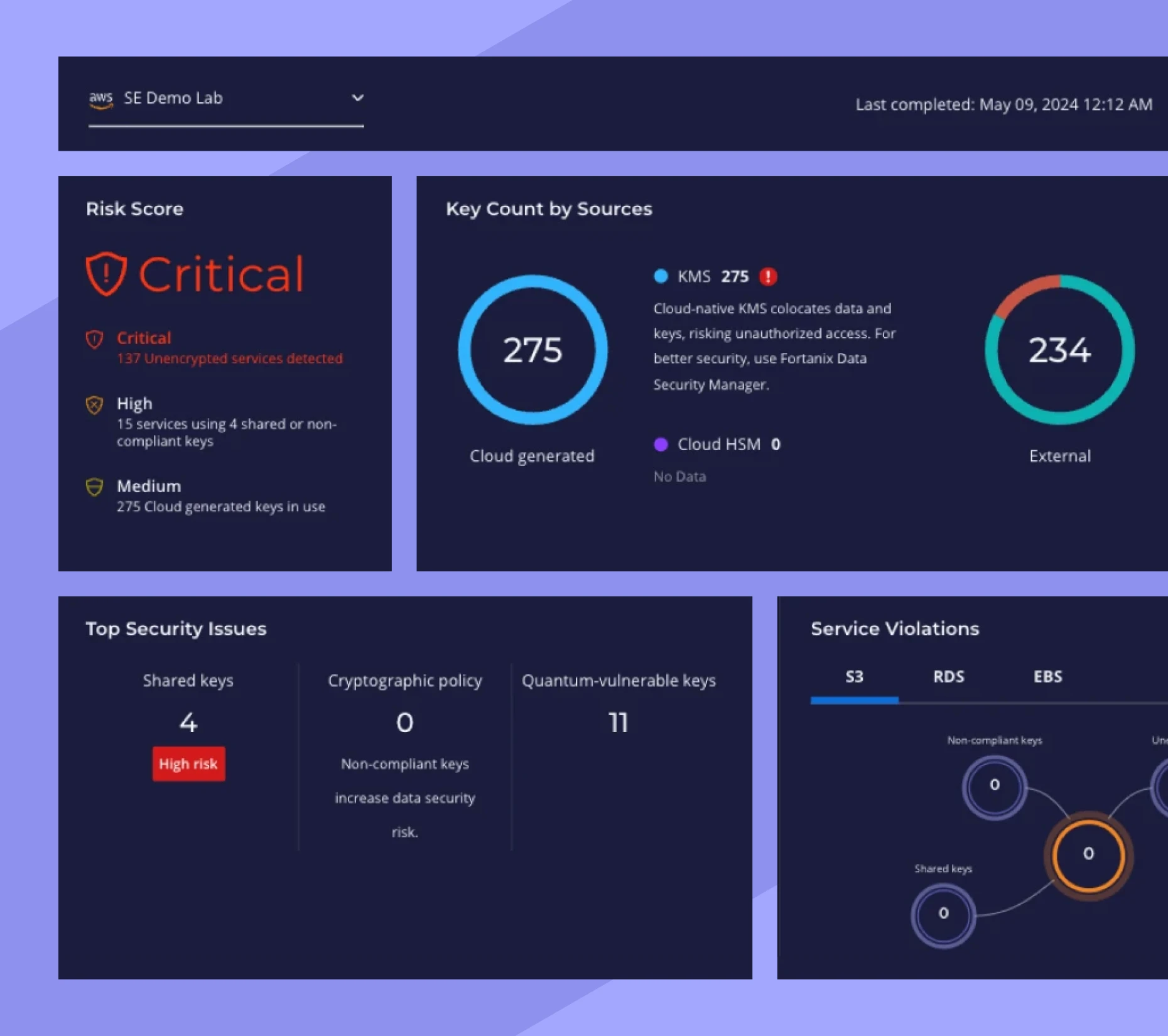
Key Insight
Cryptographic Security Posture Assessment
Fortanix is the only platform that allows you to discover encryption keys, assess your cryptographic security posture, and remediate potential vulnerabilities across on-prem and multicloud environments in one place.
- Discover keys and data services across the organization, classifying them by type and risk.
- Identify at-risk keys and services and ensure compliance with regulations.
- Detect quantum-vulnerable keys and at-risk services.
- Prioritize risks and follow actionable remediation steps when a vulnerability is detected.
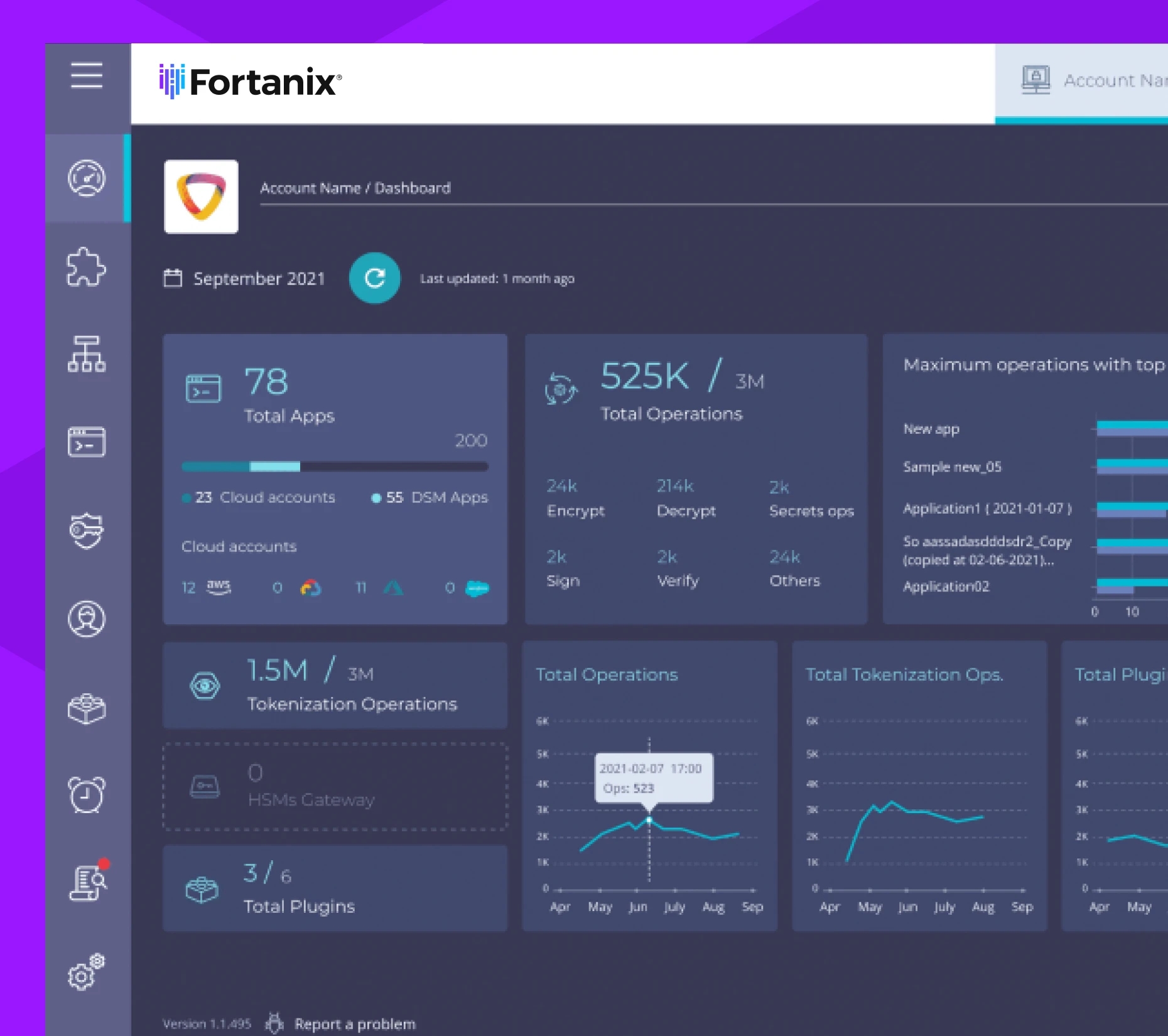
Data Security Manager
Enterprise Encryption and Key Management
Fortanix streamlines disparate processes for data encryption, data tokenization, key management, credential and certificate storage, and more without requiring expensive upkeep and maintenance.
- Encrypt data at-rest, in-transit, and in-use with a single platform.
- Automate key distribution, rotation, and revocation across the company.
- Protect private information and sensitive data with vaultless data tokenization.
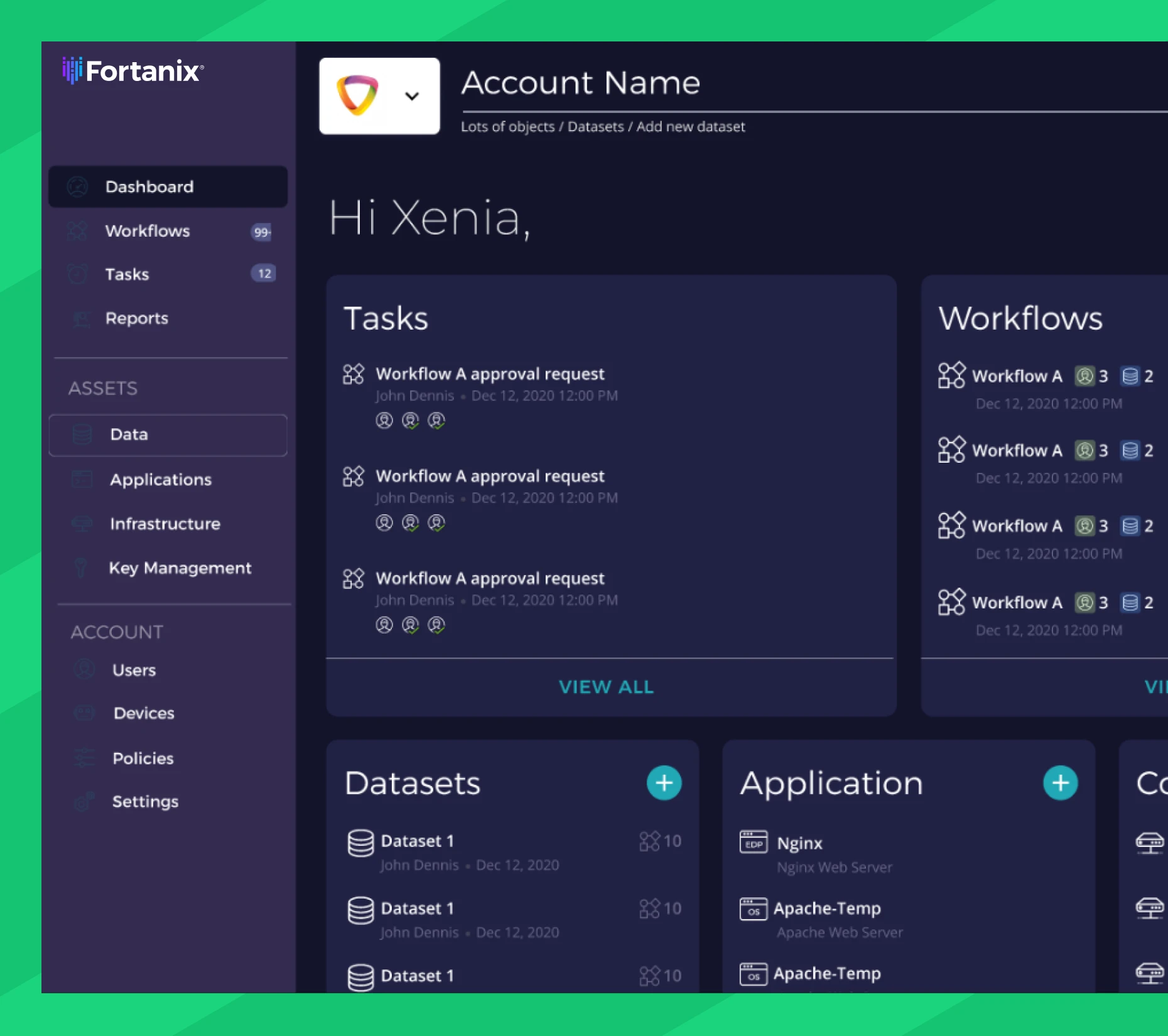
Confidential Computing Manager
A Solution for Confidential Computing
Fortanix doesn’t just encrypt data at-rest and in-transit—the platform encrypts data in-use across any cloud application, storage, and on-prem environments by isolating critical processes in a secure enclave. Stay on top of it all with Confidential Computing Manager, a bird’s eye view with a granular set of controls for managing your trusted computing environments.
- Quickly register nodes using intuitive, efficient workflows.
- Run critical processes at a nearly equal performance rate in trusted execution environments (TEEs).
- Replicate databases in a secure enclave for fast, confidential search.
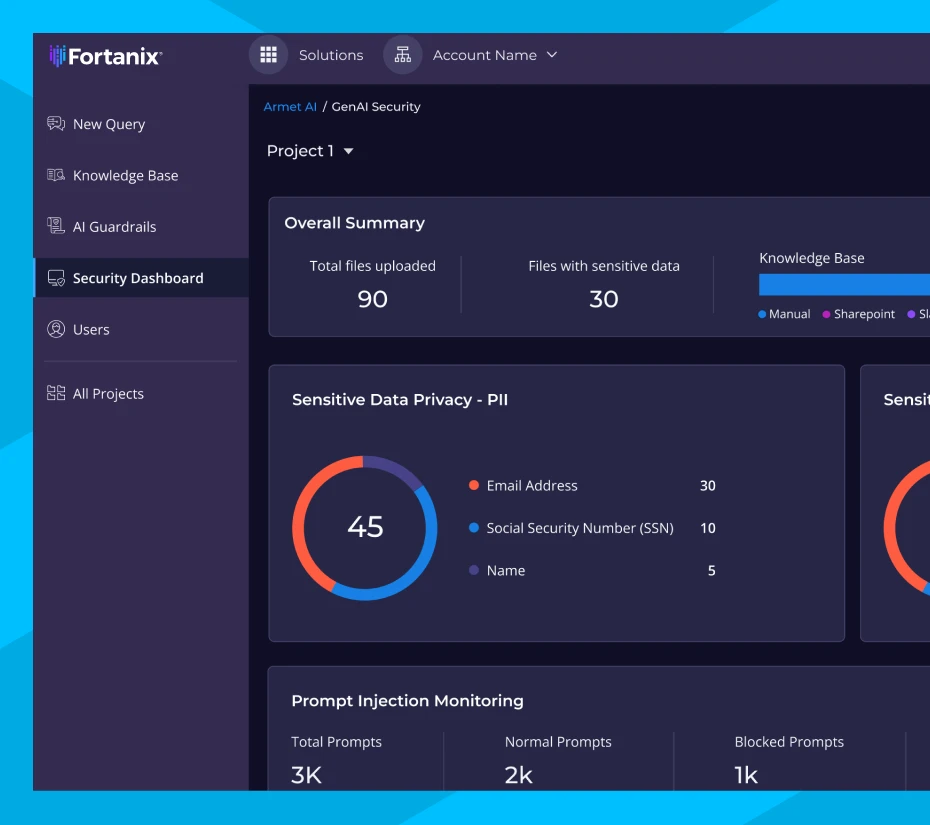
Armet AI
Turnkey, Secure GenAI Solution
Armet AI allows enterprises to quickly deploy a custom GenAI solution that prioritizes data and model security to minimize AI risk, ensure trusted responses, and drive compliance with regulations. With Armet AI, teams now can safely use their data and run the AI pipeline components on Confidential Computing, delivering a holistic solution on the world’s most secure technology.
- Ensure data and AI pipeline security.
- Prevent malicious GenAI misuse and train LLMs with own compliant and private data.
- Turnkey deployment that you can tailor to your needs.
Enforce Governance and Compliance Across Your Company
With Fortanix, you get centralized visibility and control over the policies and procedures that keep you compliant with PCI-DSS, HIPAA, GDPR, SOX, and dozens of others. The platform makes compliance easy, helping you pass audits faster and report on company-wide activity.

Identity and access management

Company-wide key policies

Attestation that assesses and validates systems for security

Consolidated audit logs and reporting for easy compliance workflows

Automated notifications when your systems are at risk
Integrate your data security ecosystem with Fortanix connectors and APIs
Flexibility to Deploy via SaaS
or On-Premises

FIPS 140-2 Level 3 backed service
Rapid deployment and global scale
Scaling to Billions of Transactions
Dedicated Regions for Data Sovereignty and Regulatory Compliance

Instant Key Management System
Infinite scalabilty

FIPS 140-2 Level 3 appliance
Native clustering & management