Most of the enterprise adopters of public cloud services opt for a multi-cloud strategy. The multi-cloud strategy provides an enterprise with the flexibility of avoiding vendor lock-in and utilizes best of breed solutions of mega-vendors. In a recent Gartner survey of public cloud users, 81% of respondents said they are working with two or more providers.
As multi-cloud environments are becoming a norm for many enterprises, there is increasing importance in securing data in the cloud. It is well established that encryption is the correct way to secure data, hence cloud providers have come up with “BYOK” (Bring-Your-Own-Key) services of their own along with their own software-backed or HSM-backed key management services.
Looking at the approaches of cloud providers, there are challenges with software- or HSM-backed key management services (KMS) or BYOK keeping in mind the multi-cloud environment and regulations such as HIPAA, PII, GDPR or PCI.
-
For software-backed key management services, the data as well as the keys, reside inside the cloud provider’s infrastructure which poses an additional level of risk during a data breach. Also, software-backed key management services offered by cloud providers lacks HSM grade security.
-
HSM-backed key management services certainly improve the security of keys, but it still does not solve the problem of keeping data and keys separate as cloud-backed HSMs are generally located in cloud provider’s data centers.
-
With BYOK services, cloud providers do solve the problem of keeping keys and data in a separate environment. However, to bring keys into public cloud KMS there needs to be multiple repetitive operations of generating a key, downloading a wrapping key and uploading wrapped key. Also, the organization has to login to each cloud provider’s console and manage “BYOK” key life cycle. With the adoption of multiple cloud services, the above-mentioned operations become increasingly cumbersome to manage.
Fortanix Cloud Data Control, available across AWS, Google Cloud and Microsoft Azure, supports consistent encryption key management policies across multiple cloud providers, tenants, and regions while enabling keys from any cloud or on-premises HSM to encrypt data anywhere.
Fortanix Cloud Data Control is a powerful tool catering to the need of secure and automated key management with zero downtime in modern development and deployment lifecycle with features that address problems faced by DevOps as well as Security admins in a multi-cloud environment.
-
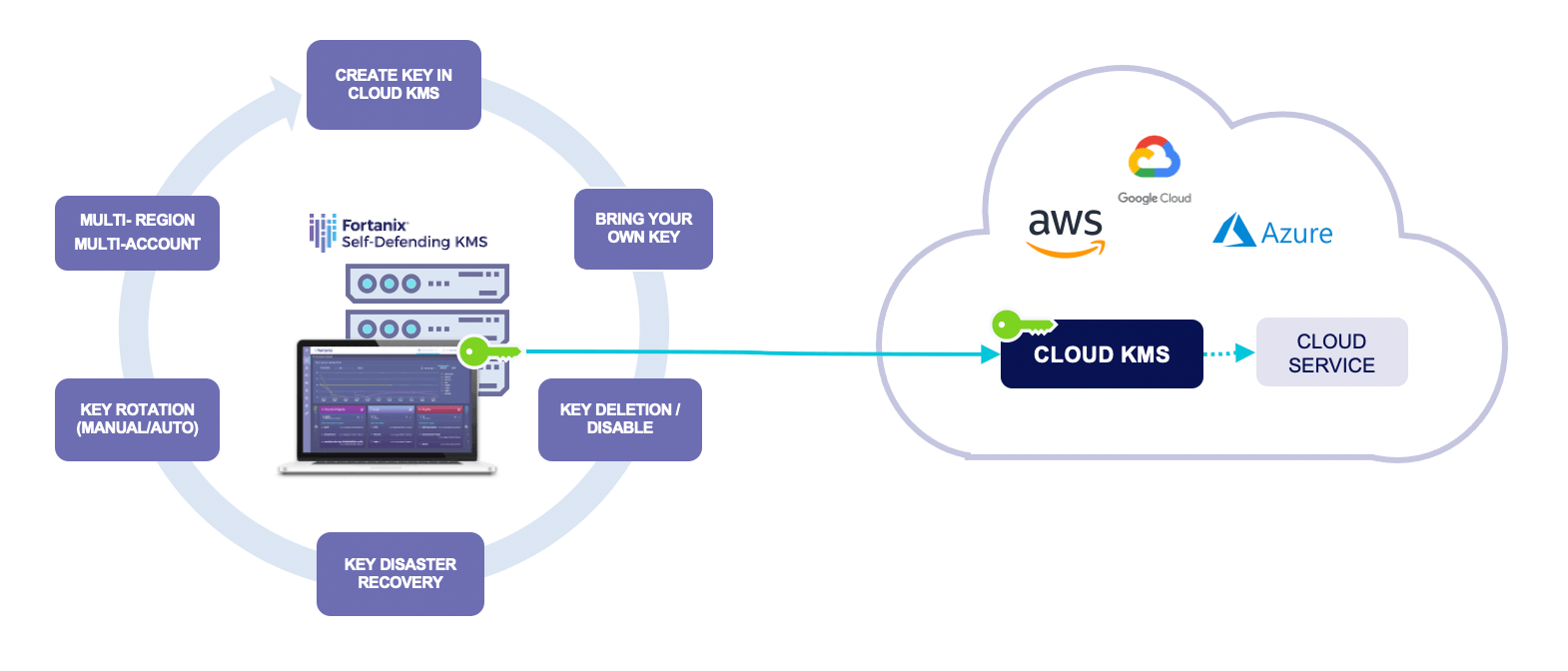
Unified Cloud Key Management – Fortanix Cloud Data Control provides a single pane of glass for importing and generating keys inside the cloud provider’s KMS and managing key lifecycle i.e., key rotation, key deletion, etc. More importantly, Fortanix’s solution removes the pain of “BYOK” process of cloud providers and with a click of a button or single API request, keys are generated and copied the cloud provider’s KMS. Apart from “BYOK” service, the solution also automates the following operations with a single click or API request –
- Managing cloud provider’s attributes of keys e.g., tags,
- Managing key access policy of cloud providers,
- Enabling/Disabling key,
- Supporting key soft delete (or schedule deletion) and purge with mapping the same
- Presenting key states in cloud KMS and keeping the same terminology used in cloud KMS,
- Recovering and restoring of key material.
To further harden protection around crypto operations, Fortanix Cloud Data Control allows quorum policy to be set on a cloud KMS group in an account, such that every security-sensitive operation in the group requires a quorum approval to be obtained.
Related Read: Drowning in Multi-cloud Key Management - A Brief -
Hardened Encryption Key security – Fortanix Cloud Data Control stores keys inside FIPS 140-2 Level 3 validated hardware security module (HSM) leveraging Intel® SGX which creates a hardware-based trusted execution environment to protect keys and perform crypto processing. HSM grade security becomes critical if particular data and operations of organizations are governed by regulations such as HIPAA, PCI, PII, or GDPR. Also, it addresses a fundamental step in data privacy and security that is to keep encryption keys separate from data and gain control over key operations.
-
Cloud and DevOps Friendly services – Fortanix Cloud Data Control facilitates organizations to integrate their modern business-critical applications and containers using traditional cryptographic interfaces (PKCS#11, KMIP, and more) or its native RESTful interface. The solution supports authentication of APIs using a system-generated API Key, client TLS certificates, JSON web tokens or using Active Directory credentials. Once authenticated, Fortanix Cloud Data Control provides fine-grained authorization control like time-based authorization, role-based access control (RBAC), quorum-based authorization, key-based authorization, LDAP authorization, etc.
-
Cloud Encryption Key Backup and Disaster Recovery – Fortanix Cloud Data Control provides automated load-balancing, fault-tolerance, disaster recovery, and high availability of cloud master keys. Apart from the built-in load balancer, Fortanix Cloud Data Control can integrate with external L4 load balancer thus providing automatic failover and multisite support.
- Google External Key Manager (BYOKMS for GCP)
Protect the data at rest by using encryption keys stored and managed by Fortanix stored outside the Google Cloud. - AWS External Key Store (BYOKMS for AWS)
The External Key Store (XKS) functionality allows AWS users to move the Root of Trust outside the AWS Cloud and store keys outside cloud.
Providing automation for importing keys, unified single pane of glass for key lifecycle management, and storing keys in a trusted environment with back up and DR support are essential features of enterprise key management services in a multi-cloud environment.
This not only offers enterprises flexible key management and comprehensive data protection but also gives them a way to regain control over their keys. With Fortanix Cloud Data Control, organizations can be assured that their data and applications stay protected in public cloud and keys will stay private even if the public cloud is compromised.