What do you do with Confidential Computing
True to its name, Confidential Computing remained, well – confidential – for a rather long time. Until today, with the public announcement of the Linux Foundation Confidential Computing Consortium.
Intel®’s SGX technology is a fundamental foundation of Confidential Computing. We at Fortanix identified early on the disruptive potential of SGX-based Confidential Computing and have been developing our platform and solutions based on Intel® SGX towards that end.
We realized that Confidential Computing isn’t just a fancy technology, a solution looking for a problem, but a disruptive enabler of data protection and secure computing.
While our engineers were busy in the pioneering effort to build the first-ever SGX-based products, we have been equally busy figuring out what are the paramount use-cases we should focus on. In other words, what real problems are we solving.
The result is our Runtime Encryption platform (RTE), associated with our enclave development platform (EDP), and host of solutions, built on top of our platform.
All of these solutions are “industry-first” and are the first commercially available solutions based on Intel® SGX.
So how do you use Confidential Computing?
The fundamental value of Confidential Computing using Intel® SGX is the ability to isolate the software and data from the underlying infrastructure (hardware or OS) by means of hardware-level encryption.
Implication: now you can run your sensitive applications and data on untrusted infra-structure, namely public clouds and all other hosted environments.
That’s right — you control the security and privacy of your applications and data when they run anywhere. You don’t have to trust your cloud provider.
This translates into a number of use-cases, none of them feasible before.
The fundamental value of Confidential Computing using Intel® SGX is the ability to isolate the software and data from the underlying infrastructure (hardware and OS), by means of hardware-level encryption.
The Simple: Encrypt your application
Sound simple? Not so much. Unless you use Fortanix RTE. With RTE and its automated workflows, orchestration, management, and easy integration with any CI/CD, you can literally encrypt your application in a single click and deploy and manage it centrally.
You may have a logging or SIEM application, or a database running sensitive data, or directory service. You cannot move them securely to public cloud unless the security and privacy are deterministically assured.
With RTE you can.
Implications? You can now move your IT to public cloud and other hosted environments. This changes the economics of your IT.
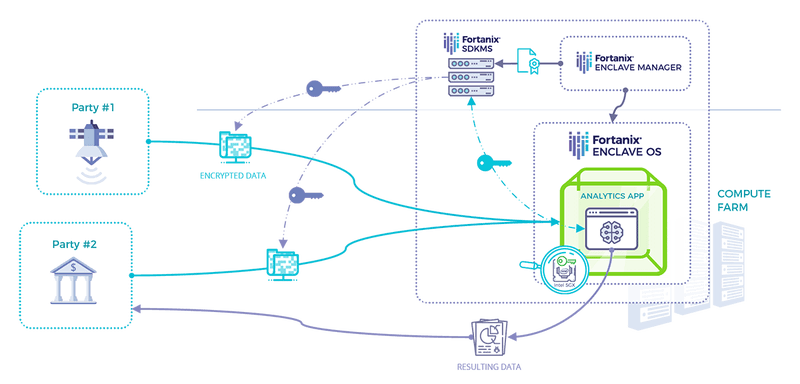
The Enabler: Secure and anonymous analytics on multiple data sets
There’s a growing problem: how can you perform analytics on a dataset, or multiple datasets, while assuring that no one can ever have access to the sensitive data (e.g., the users can only see the results of the analytics, never the source private data)?
Without Intel® SGX and Fortanix RTE solutions, this deceptively simple task would be impossible or so complicated and costly to the point of being impractical.
So here is secure and private analytics:
- The to-be-analyzed dataset is sent encrypted from the source database to the analytics/ML/AI application, running encrypted inside SGX enclave
- The encrypted datasets are decrypted inside the SGX enclave where the analytics application runs
- The analytics application runs its job on the combined datasets and generates result
- The result is sent from the analytics application to the users
- The users can never have access to any of the source databases, neither can they have any access to the secure enclave where the analyzed source data is
The entire process is encrypted end-to-end: at rest, in motion, and in use. This is what Confidential Computing really means. Multi-party AML, anti-fraud, genetic research, health/medical research. The applicability of this use-case is universal.
Confidential Computing in Financial Services: Use Cases for Data Security
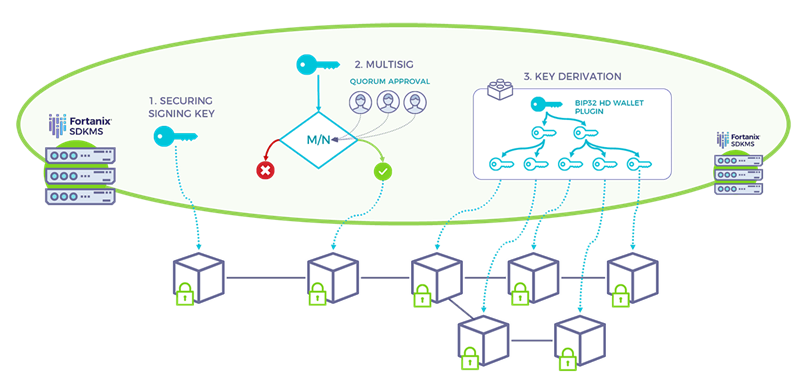
The Emerging: Blockchain, of course
Blockchain is all about security, but none of the Blockchain platforms provide the needed security. The key management solutions aren’t secure, the smart contracts aren’t secure either.
The solution? Encrypt all Blockchain applications, Wallets and Smart Contracts with RTE, coupled with secure key management, which runs inside a secure SGX enclave as well.
Like secure private analytics, this use-case seems deceptively simple, but it’s far from that. How do you assure scalability and end-to-end encryption in such a distributed and dynamic environment?
Take a look at how we do that at Fortanix.
At the end, Confidential Computing is not about the technology, but about the usage, the real-life problems it solves.
Fortanix has taken Confidential Computing out of the lab and into the sunlight.
We’re excited to hear the announcement of the Confidential Computing Consortium. For us it’s a very happy day, where our vision takes shape, and reality aligns with our dreams.
We’re fully geared up to serve customers and partners with Confidential Computing solutions, today.