‘We should treat personal electronic data with the same care and respect as weapons-grade plutonium – it is dangerous, long-lasting and once it has leaked there’s no getting it back.’
-Cory Doctorow
Every year 28th of January is observed as International Data Privacy Day—in Europe as Data Protection Day.
But what makes data privacy such a big deal?
Very few terminologies come close to the meteoric rise that data privacy has gained over the past few years. Both—in terms of public awareness and how it's interpreted.
That said, the increasing awareness around data privacy, induced by revelations from regulatory bodies and authorities, uncovers a huge disparity between how companies use personal data vs. what their users are comfortable with.
As a result, data breaches over the past few years ran the gamut from wacky too weird to just plain worrisome, and Data Privacy Day serves as a gentle nudge to businesses to better protect their data in the digital ecosystem—before it's too late.

Security to Ensure Privacy
When the internet first arrived, ‘security’ took precedence over privacy. As a matter of fact, for the average internet user, the idea of privacy and security was almost the same. It was hard to fathom the value of personal data and it being used beyond a certain capacity—let alone being sold to advertisers.
Eventually, ad-driven businesses like Google and Meta started leveraging personal user data to deliver more accurate search results and superior user experiences. While users benefitted from a free and highly intelligent search engine, the advertisers had much to gain from improved ad targeting based on the user’s online activities and search history.
Fast forward to the present day—instead of merely deducing from user activities, advanced algorithms can now predict consumer behavior. The fusion of big data, AI, and sophisticated algorithms now run multiple combinations of data sets to draw consumer behavior patterns and deliver highly personalized results and services.
Clearly, the need for data privacy in the present day is as critical as saving your data from any outsider threat.
Related read: Celebrate Day Privacy Day with a CISO and CDO Meeting of the Minds

Trends to Watch Out For in 2023
So, how does 2023 look like with respect to Data Privacy? Here are the top three emerging trends we foresee:
- The (Continued) Rise of Data Privacy Regulations
Ever since GDPR paved the gold standard for data privacy, we have seen different countries bringing in their own
regulations, including MAS (Singapore), DPA (Philippines), SOFIPO (Mexico), CPS234 (Australia), PIPL (China), LGPD (Brazil), Amended PDPA (Singapore) and DCIA (Canada).
If numbers are to be believed, by 2024, almost 75% of the global population will have its private data covered under privacy regulations, and these regulations will continue to be the dominant catalyst for the operationalization of privacy.
What remains to be seen is how do governments patch the hyper-localized regulations. For instance, the US has an onerous patchwork of regulations across each state, and a federal privacy law remains a distant dream.
As more states roll out data privacy laws, companies will need to develop solutions to comply with a growing list of different laws.
- Expanding Data Protection Roles
The cascading effect of all the commotion around data privacy and regulatory compliance will eventually lead to the need to onboard more people working on compliance.
The current workforce will start to fall short, given the growing streak of global and regional compliance to abide by. Most businesses will need a dedicated team or at least a few helping hands.
Chief Information Security Officers, Data Protection Officers, and Chief Data Officers will be encouraged to join their efforts in mutual attempts to strengthen their DPMS.
- Data-First Security
In 2023, we will see security move closer to what it really intends to protect—data. While perimeter-bound security has been around and will continue to do so, 2023 is going to be all about data-first security.
The proliferation of systems, devices, and endpoints at the edge—coupled with the rise of multi-cloud models—leads to distributed and dynamic operating environments. One where it’s hard to physically secure data and systems and traditional approaches to security are no longer effective.
Related Read: Meet Team Fortanix at Black Hat 2023.
Securing the KEY to Data Privacy
Okay, so how do we embark upon our quest for data privacy?
A good place would be to begin by avoiding storing your data and encryption key together. Think external key management.
- AWS XKS
Regulations like Schrems II and GDPR requires organizations to ensure PII data from citizens in the European Economic Area remains within these borders. This data must be protected using state-of-the-art encryption, and the encryption keys must be in the sole custody of the data importer.
In addition, these regulations require the ability to revoke data access at any time, and to segregate encryption keys from data on the cloud.
An external key store introduces an extra encryption layer to give organizations full custody of their keys.
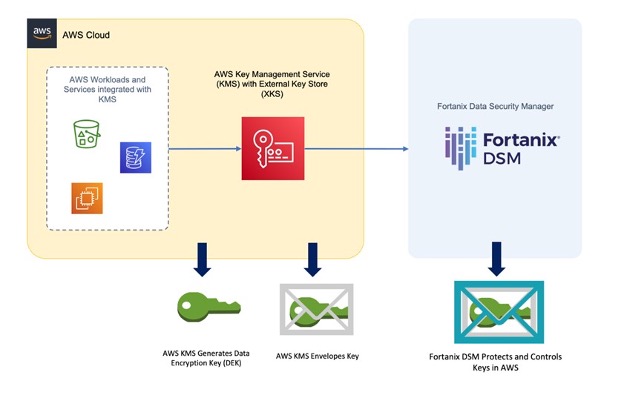
Fortanix DSM functions as an AWS external key store to enable organizations to move the data to the cloud with the highest level of security and control for their keys. Encryption keys are under complete customer control and secured by FIPS 140-2 level 3 certified HSMs, segregated from the cloud data.
Fortanix DSM users get a centralized solution to get control of the lifecycle of their keys, no matter if they are used on-premises, or in the cloud. Because Fortanix DSM users have sole key custody, neither Fortanix nor AWS can enable access to the protected data, not even when a government subpoena is issued, for example through the CLOUD act.
Watch this one demand webinar to see us live in action. - Google EKM
Google’s External Key Manager (EKM) service enables users to protect the data at rest by using encryption keys stored and managed by a third-party key management system (KMS) outside the cloud.
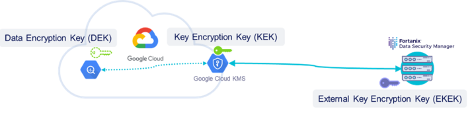
Fortanix integrates with Google Cloud Platform (GCP) External Key Manager service to enable organizations to move the data to the cloud and get the same level of security for keys that they're used to in their own on-prem environments.
Encryption keys are always under customer control and stored inside a FIPS 140-2 level 3 certified HSM, away from the cloud. At a click of a button, in real time, enable and disable access to your data from specific instances and locations.
Here is the on-demand webinar to demonstrate how we deliver Google EKM.
Conclusion
Any business that racks up user data, irrespective of its size, needs to minimize data bound risks.
Fortanix was built with the vision of democratizing data security. Any business, irrespective of how small or big it is, has equal responsibility and requirement to secure its data.
Partnering with companies that offer additional data privacy and security solutions can add more value to your brand reputation. Look for solutions that protect your consumers’ privacy with features like data encryption, key management, HSL 140-2 L3 grade security, identity theft protection, and other features that safeguard what consumers value most.
Want to learn more? Get in touch here.
Want to know more about AWS XKS capabilities? Click here.
Related Read: The Hustle to Stay Away from The Whistle
Stay secure. Stay Alert. Happy Data Privacy Day!

 Cite this article
Cite this article








