The Challenge
Compliance regulations like Schrems II ruling and GDPR require organizations to have the ability to revoke access to data at any time and store the encryption keys outside the cloud as additional data protection measures. To comply, an External Key Management system or Bring-Your-Own-Key-Management-System (BYOKMS) approach is critical. And that is precisely why Google has introduced the External Key Manager (EKM) service. With this mechanism, you can protect the data at rest by using encryption keys stored and managed by a third-party key management system (KMS) outside the cloud, meet privacy requirements and ensure enhanced security for your cloud data.

Fortanix Solution
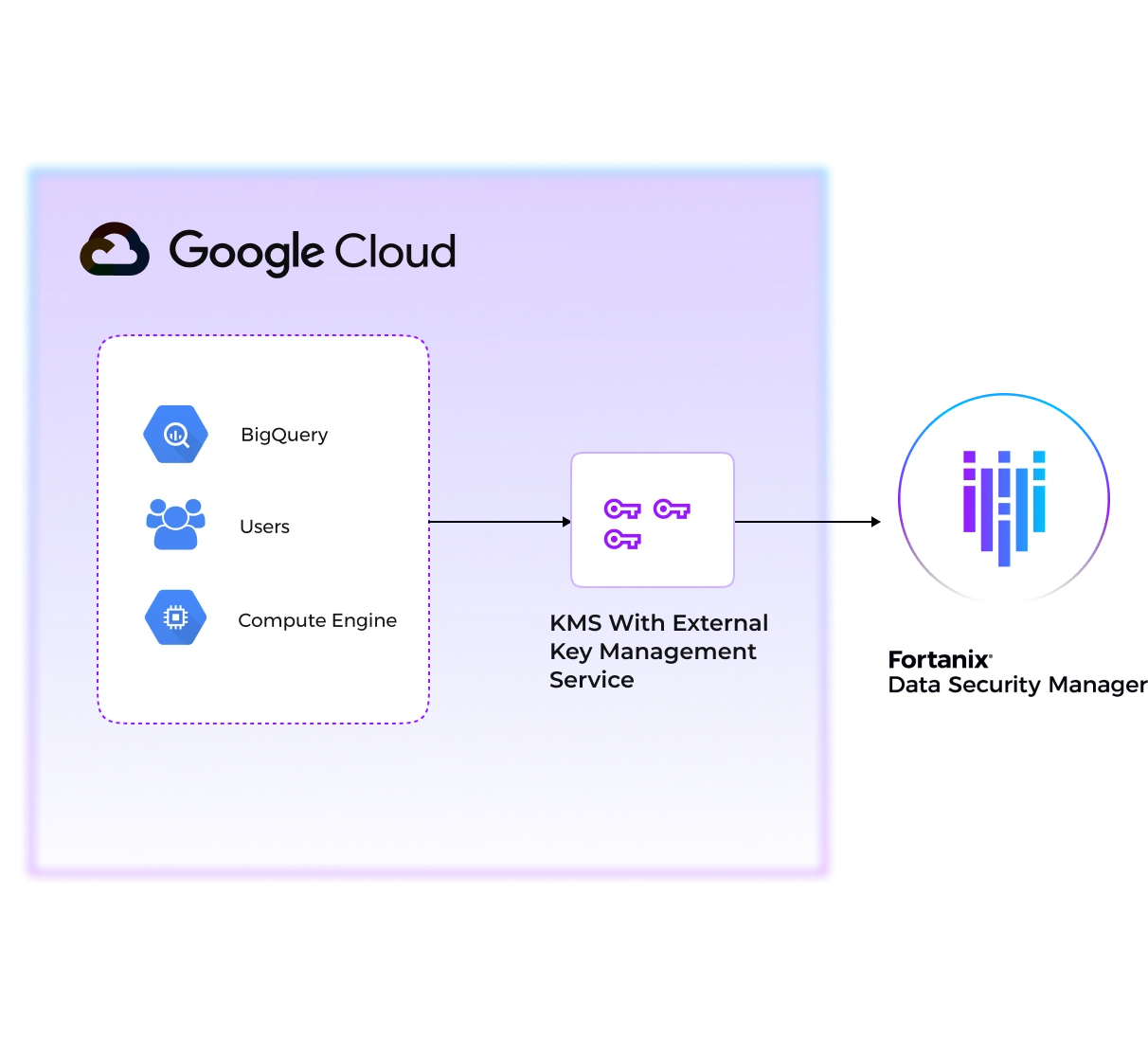
Fortanix integrates with Google Cloud Platform (GCP) External Key Manager service to enable organizations to move the data to the cloud and get the same level of security for keys that they're used to in their own on-prem environments. Encryption keys are always under customer control and stored inside a FIPS 140-2 level 3 certified HSM, away from the cloud. At a click of a button, in real time, enable and disable access to your data from specific instances and locations.
Benefits

Compliance mandates such as GDPR/Schrems-II require organizations to store keys separately from the data it protects. Fortanix helps meet compliance by giving customers control of their keys with FIPS 140-2 Level 3 certified hardware security modules (HSMs). Fortanix has dedicated datacenters in the European Union (EU) and can guarantee that keys remain within the EU boundaries, as per GDPR mandate. With an additional corporate entity established in The Netherlands, Fortanix operates outside USA jurisdiction to further protect the data of European citizens.

Organizations that want to fully control their risk must have full control of the keys that protect their data. By using the KMS solution from their cloud provider, they trade proximity for exclusive control. Cloud providers can be forced by a court order to hand over keys and data. With DSM as an external key store (XKS), organizations have full control and ownership of their keys and data. To further meet regulation mandates, Fortanix DSM also provides a kill-switch functionality. This allows administrators to immediately block access to data-at-rest on the GCP platform with just a couple of clicks to change permissions for any, or specific, instances and locations.

Define, enforce, and track data access policies from a single interface, and accelerate cloud migration. Fortanix DSM provides a single and secure source to protect keys and data, regardless of whether they are used on-premises, or in the cloud. DSM provides granular, role-based policies, including quorum approvals, and integrates seamlessly with existing authentication identity providers.
Key Differentiators
Immediately identify the most important risks, and drill down into the details.

Centralized management
HSM gateway acts as a management layer for your legacy HSMs and enables a transition to Fortanix’s innovative on-premises HSMs, or its industry-first HSM as-a-service.

SaaS or on-premises deployment
Choose the flexibility of a SaaS platform but you can also opt for a virtual machine deployment or FIPS 140-2 Level 3 physical appliance with built-in HA/DR with multi-cluster support.

State-of-the art data security
The DSM platform is built on Confidential Computing technology and is FIPS-140-2 Level 3 validated for secure key storage. In addition, Fortanix offers a plethora of advanced security capabilities like Quorum approvals, plugins, Role-Based Access Control (RBAC) and much more.
Resources
Here are some of latest news, blogs, resources, events, and more