Alice wants a service that Bob provides. Alice must provide something of equal value in return. This is achieved by using a medium of exchange such as currency. Alice entrusts her currency to a third party, such as bank, by opening an account and depositing her currency. The bank acts as a custodian of the currency. It maintains accounts for users and facilitates transactions of currency between accounts. Alice directs the bank to transfer currency to Bob’s account when she uses his service.
Such a system has several disadvantages: the bank gets to set transaction fees; the transactions may not be anonymous; the data on the bank’s systems can be hacked, lost, or mishandled; the bank can refuse certain transactions; accounts can be frozen or their balances confiscated.
Blockchain technology and digital currencies
In 2008, Satoshi Nakamoto released a paper introducing blockchain technology. The paper described a decentralized network characterized by peer-to-peer communication which facilitate transactions between people who do not know or trust each other, without reliance on a central authority to maintain account balances. The currency implemented by a blockchain is called a cryptocurrency.
What is cryptocurrency?
A cryptocurrency is a digital asset designed to function as a medium of exchange that uses strong cryptography to secure financial transactions, control the creation of additional units, and verify the transfer of assets. Each user has one or more addresses, each with an associated pair of public and private keys that they may hold in a digital wallet. Only the user with the private key can sign a transaction to transfer units of their cryptocurrency to someone else.
Let’s see how the transaction between Alice and Bob happens in a cryptocurrency system. Bob sends his address to Alice. Alice creates a transaction with Bob’s address and the units of cryptocurrency to transfer, signs it with her private key, and adds her public key for signature verification. Alice then broadcasts this transaction on the blockchain network. The transaction is verified and then recorded in a chain of blocks that is collectively maintained by all computers in network. Once the transaction is sufficiently verified, Bob owns the cryptocurrency.
Understanding how cryptocurrency wallet works
A standard cryptocurrency wallet is used to store the cryptocurrency tokens or coins. For each transaction, the user gives a public address to others to receive funds from them, and a private key that the user uses to spend the stored tokens. This public/private combination mechanism ensures safety of the cryptocurrency tokens but comes with an additional overhead of the user being required to repeatedly generate a random pair of private and public keys and an address and back them up. As the number of transactions increases, this process becomes cumbersome for the user.
Imagine the scenario where the user is not an individual but an e-commerce application which needs to generate thousands or even millions of public addresses daily to receive funds from customers for their purchases. The solution doesn’t sound scalable anymore.
HD Wallet – the new age digital wallet
The BIP 0032 document describes a hierarchical deterministic wallet (or “HD Wallet”). HD wallet solves this problem by deriving all the addresses from a single master seed in a deterministic manner. This eliminates the need to back up every key pair. HD wallet uses a 128-512 bit master key seed, which the user can memorize or save in a physical form. The entire wallet can be recreated from this seed. HD Wallet uses elliptic curve cryptography, specifically the field and curve parameters defined by secp256k1. Elliptic curve cryptography allows for schemes where one can calculate the public keys without revealing the private keys, and keeping the currency safe from being spent by an adversary.
Address generation involves creating a public and private key pair, hashing the public key with SHA-256 and RIPEMD-160 algorithms, calculating the checksum, and converting the output to an alphanumeric representation using the Base58 encoding scheme. A secure execution environment to run these cryptography operations and a robust key management system to secure the key completes the picture of an ideal wallet.
Generating and managing keys on your own has often resulted in unrecoverable losses of funds. The recommended way to generate an address is to use a well-tested, open source, peer-reviewed wallet solution. But such a solution can falter when run in a non-trusted environment, which is typically true for the shared cloud infrastructure that runs modern applications.
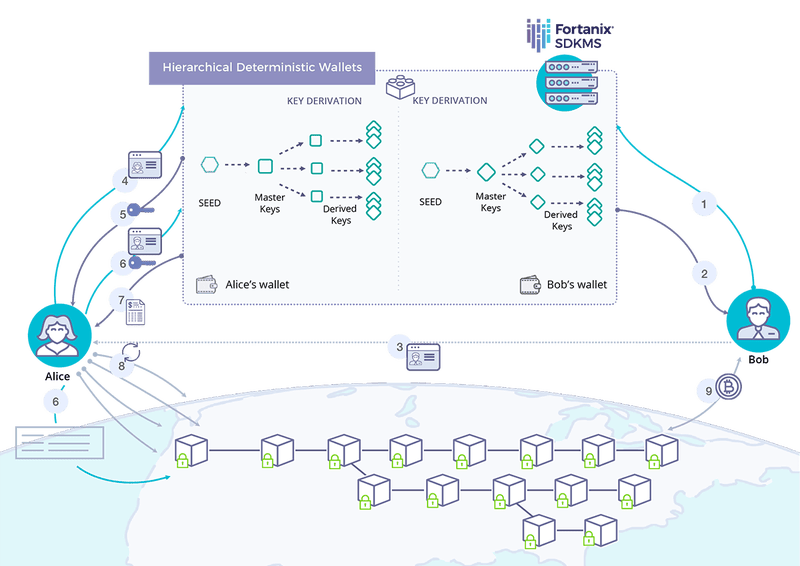
1. Request to generate Address. 2. Fortanix DSM generates a key pair and derives an Address. 3. Bob shares generated Address with Alice. 4. For Alice's Address, request private key from Fortanix DSM. 5. Fortanix DSM returns Private Key to Alice. 6. Create a transaction in Fortanix DSM using Alice's Private Key and Bob's Address. 7. Signed transaction message is sent to Alice. 8. Alice broadcasts transaction message to Blockchain network. 9. Bob now owns the cryptocurrency.
Fortanix HD Wallet – Fortanix DSM Plugins
Fortanix® Fortanix DSM is a unified cryptography and key management solution which offers HSM-grade security with software-like scalability, flexibility, and effectiveness. It has a cryptography toolkit, key management, role-based access control, and tamper-proof audit logs. It comes with a plugin mechanism to extend the system by implementing custom functionality in a high-level, memory-safe language.
Fortanix has implemented a deterministic HD wallet as an Fortanix DSM plugin which uses the Fortanix DSM native cryptography library. Both the plugin and the native cryptography run inside a secure execution environment powered by Intel® SGX technology. The keys are automatically backed up and protected by access control. The implementation can be found here.

 Cite this article
Cite this article







