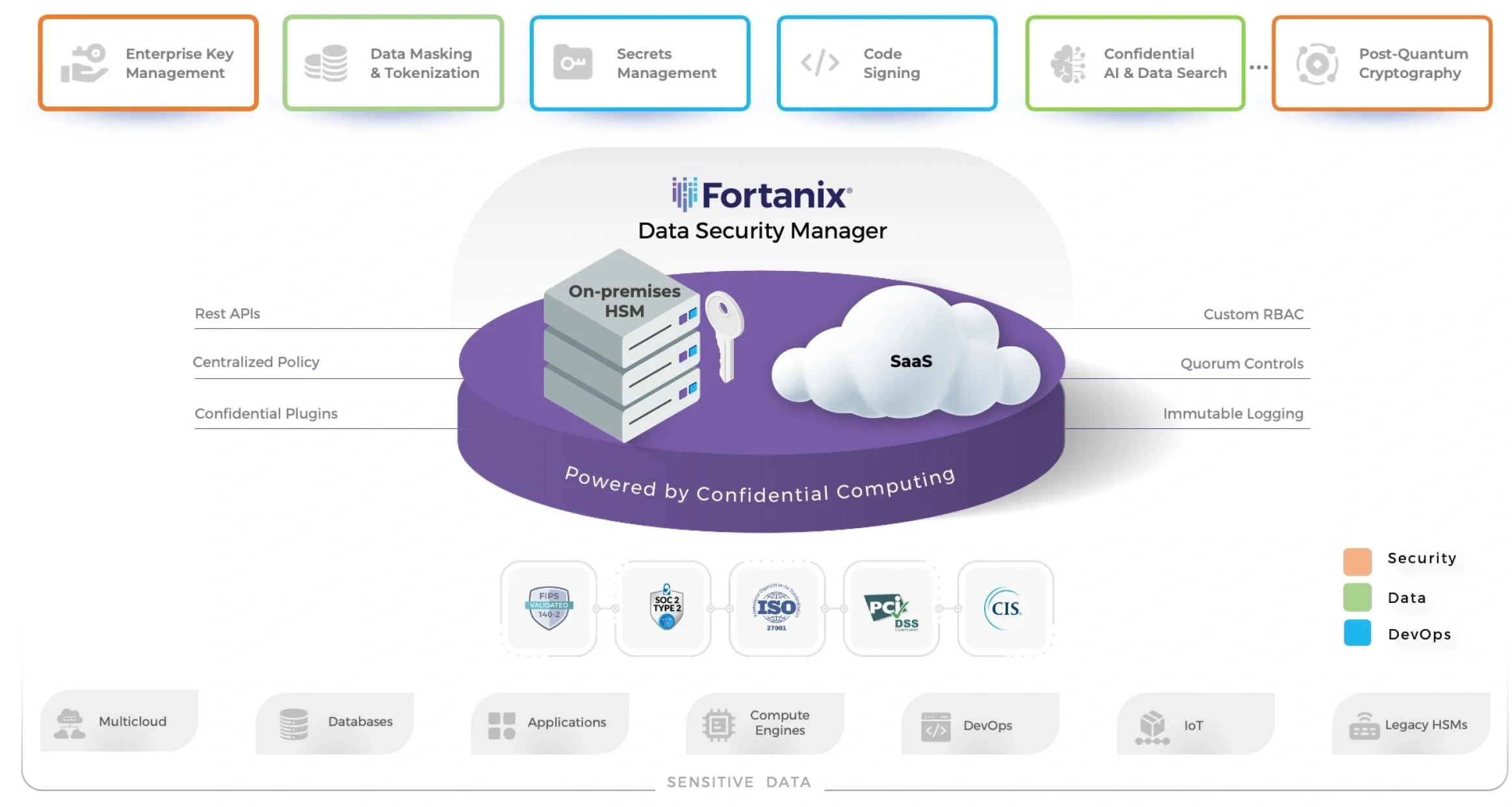
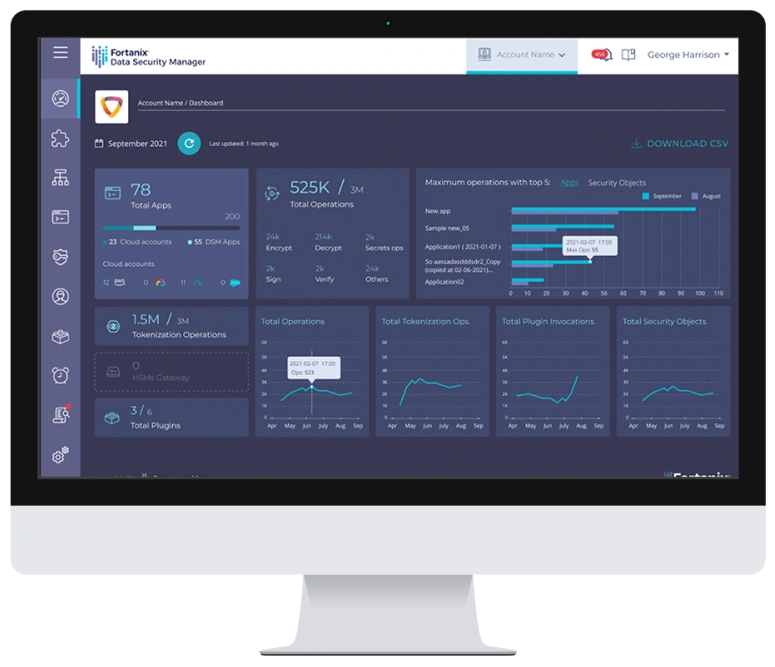
Fortanix Data Security Manager (DSM)
Unified Data Security Platform
The Fortanix Differentiation

Confidential
Computing
Hardware-backed secure enclaves to protect data-in-use with the Fortanix Confidential Computing Manager

Highest Industry Certifications
Certifications include FIPS 140-2 Level 3, PCI-DSS, ISO 27001, CIS and SOC-2 Type 2

DSM
Accelerator
Accelerate performance of latency-sensitive applications and support high transaction volumes

REST APIs and Confidential Plugins
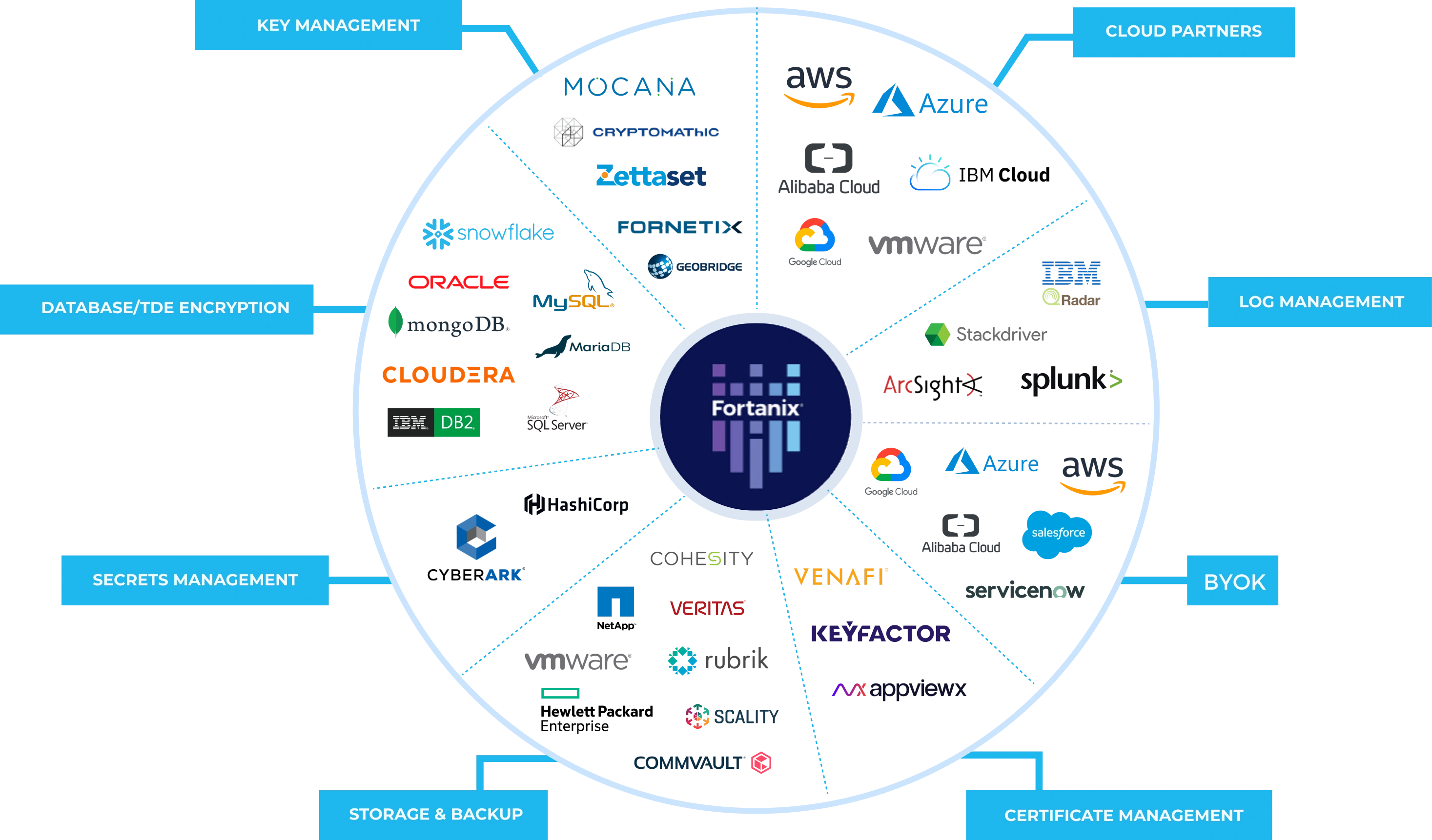
OpenAPI v3.0 to automate secure development with over 125+ ecosystem integrations

HSM and
HSM Gateway
FIPS 140-2 Level 3 HSMs to unify and manage end-to-end key lifecycle management and legacy HSMs

Saas and
On-Premises
Rapidly deploy a highly scalable SaaS solution, or opt for a virtual or physical appliance

Policy-Based
Enforcement
Enforce least privilege data access with RBAC, Quorum controls, and immutable logging

Confidential
Al
Unlock the power of securely unifying private data and Al models with Confidential Computing
Zero Trust Solutions Powered by
Confidential Computing


Enterprise Key Management
Consolidate administration of cryptographic keys across the enterprise

Data Masking and Tokenization
Tokenize sensitive data early and once to keep it private, portable, and compliant

Secrets Management
Securely store, control, and manage secrets to “shift-left” in software delivery lifecycles

Secure DevOps with Code Signing
Manage cryptographic keys and certificates for leading code signing tools
Flexibility To Deploy via SaaS or On-Premises
Consume as SaaS
- FIPS 140-2 Level 3 backed service
- Rapid deployment and global scale
Virtual Appliance
- Instant KMS
- Infinite scalabilty
On-prem Appliance
- FIPS 140-2 Level 3 appliance
- Native clustering & management
Industry-Leading, Multi-Tenant SaaS
Scaling to Billions of Transactions
Accelerate Business Outcomes With
Security at the Speed of Business

Trusted execution environments powered by Confidential Computing encrypt and secure data whatever its state: at rest, in motion and in use
Centralized key management with discovery, visibility, command control, policy enforcement and reporting empowers data, security and DevOps teams to increase productivity and business impact
Industry-leading SaaS, advanced HSMs, and innovative security controls combine to deliver performance at scale while lowering total cost of ownership (TCO)

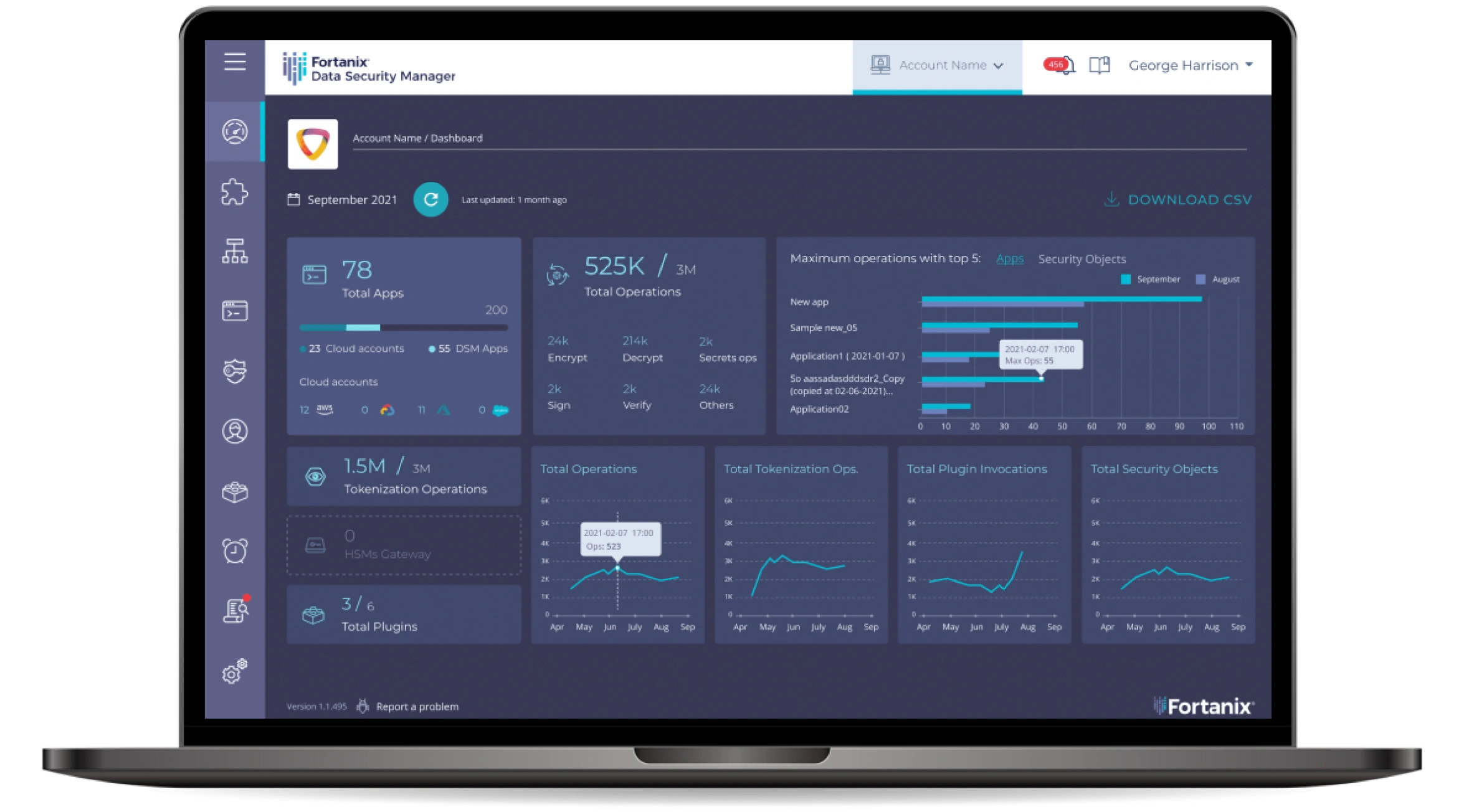
Centralized Management and
Policy-Based Enforcement
Auditing in a Scalable SaaS Solution That Makes Data Security a Breeze.
Trust Built on the Industry’s Most Stringent Certifications
Take us for a Test Drive or Start
your Deployment for Free
| DSM Explorer | DSM Enterprise | |
|---|---|---|
| Ideal for | Small-sized teams and mid-market organizations to explore limited set of data security use-cases and prove time to value quickly | Fully-featured edition with the industry’s broadest set of features for enterprise and government organizations |
| Deployment | SaaS | SaaS / On-premises |
| Use-cases | Tokenization Google EKM AWS XKS BYOK – AWS BYOK – Microsoft Azure Client-side Encryption | No restrictions |
| Sales engagement | Self-Service | Recommended |
| Support | Basic Support | Multi-tier support |
| Cost | FREE GET STARTED | Based on features 30-DAY TRIAL |
Resources
Here are some of latest news, blogs, resources, events, and more
























 3910 Freedom Circle, Suite 104,
3910 Freedom Circle, Suite 104,