Digitization and cloud initiatives have caused data sprawl for businesses of all sizes. Adoption of multi-cloud and hybrid IT infrastructure have created data silos that have delineated ownership between enterprise and cloud providers.
API based data access has brought in a further layer of complexity when coupled with dynamic policies and scattered privileges. The data breaches we see today across large banks, retailers, healthcare institutions, tech companies, public cloud providers and even the government is symptomatic of the complexity that exists in the landscape today.
Heck, even security companies have been breached. How does one secure data and protect privacy? What kind of technology is best suited to make data security a reality?
In most Enterprises, the tech stack itself is constantly evolving. A need to protect sunk investments and legacy technologies combined with the want to adapt to the new, means there isn't usually a single pane of glass to span across the entirety of the data lifecycle.
Bringing a consistent data security posture bridging the old and the new is often a challenge. Often competing technologies attempting to solve the problem in different ways cause further confusion.
Research from leading industry analysts often offer a good representation of the maturity of different technologies and where they are vis-à-vis expectations and adoption. In my opinion, the Gartner® Hype Cycle™ for Data Security,, published in August 2022 does a great job of capturing the broad technology spectrum and to define where they are in the life cycle of adoption and expectations.
While no single vendor supports all data formats, locations or every aspect of data security, in our opinion solutions from Fortanix present valuable options to the Security and Risk Management (SRM) decision makers.
It has always been my belief that even as organizations embrace more technology from specialized vendors, the complexity of training, deploying, managing, interoperating between these different silos decreases the security posture rather than increase it.
The chain is always only as strong as its weakest link, and the more links we bring to the security stack, the greater the probability of it becoming weaker.
The Gartner Hype Cycle makes a point along similar lines about convergence, citing findings from the 2022 Gartner CISO: Security Vendor Consolidation XDR and SASE Trends survey, says 56% of respondents are prioritizing data security platform consolidation specifically.
In other words, we consider taking a platform approach versus a point product approach. Ideally this should simplify the areas of learning, deployment and management and thereby reduce the surface area exposed to human errors or malicious intent, while simplifying visibility and management.
Fortanix has active solutions in or is actively investing in certain areas consistent with this convergence trend, allowing enterprise and mid-market customers to simplify their security posture across on-premises, hybrid or cloud environments.
Figure 1.0 – Fortanix Data Security Manager (DSM)
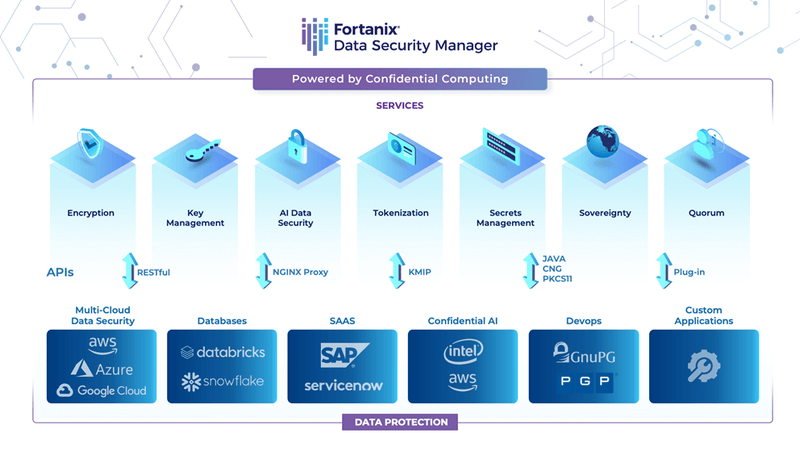
Here are a few prominent areas where Fortanix is already delivering deployable solutions, or is actively investing in for the near future, with its Data Security Manager (DSM) platform –
- Data Security Posture Management (DSPM) – As per Gartner, “Data security posture management (DSPM) provides visibility as to where sensitive data is, who has access to that data, how it has been used and what the security posture of the data store or application is.
This requires a data flow analysis to determine the data sensitivity. DSPM forms the basis of a data risk assessment (DRA) to evaluate the implementation of data security governance (DSG) policies”.
To us, with the profile of customers that Fortanix has straddling several highly regulated industries, federal agencies etc., being able to evaluate this with sensitive data is significant. This is a strategic area of investment for Fortanix.
According to Gartner, in the Table 1 - Priority Matrix for Data Security, 2022 in the Hype Cycle report, this technology has a benefit rating as transformational. - Data Security Platform - This is a broad area which actually represents an interesting trend. According to the Hype Cycle report “Data security platforms (DSPs) aggregate data protection requirements across data types, storage silos and ecosystems, starting with data discovery and classification”.
We consider this as perhaps the biggest area of Fortanix’s focus both on terms of product evolution to a platform approach, as well as the unification of hitherto silo’d entities, or legacy systems bringing them under a single pane of glass approach.
Fortanix’s DSM has been widely adopted due to this unification and a platform approach that represents the easy button for several enterprises. - Confidential Computing – As defined by Gartner, “confidential computing is a security mechanism that executes code in a hardware-based trusted execution environment (TEE), also called an enclave. Enclaves isolate and protect code and data from the host system (plus the host system’s owners) and may also provide code integrity and attestation”. –Among other use-cases, confidential computing allows for businesses to use data in the cloud in a more trusted manner.
This is mentioned as an emerging technology in the Gartner Hype Cycle for Data Security report. We consider Fortanix is a pioneer and leader in this area.
We believe, there is also widespread momentum building in the rest of the industry with public cloud providers, chip vendors and other software vendors starting to get behind this technology. For highly regulated industries, it removes one of the barriers for cloud adoption, while preserving data integrity and privacy. - Blockchain for Data Security – As opposed to traditional methods of data security, blockchain-enabled methods provide a way to decentralize security, while increasing checks and balances. There is less reliance on centralized arbitrators, and these have spawned several use-cases most notably with Decentralized Finance (DeFi), powered by what’s called as the Web3.0 infrastructure. Gartner rates the benefit as high, while maturity is still on an emerging scale.
Fortanix is investing in these areas with its solutions for DeFi use-cases using crypto and blockchain infrastructure. The recent announcement about the industry’s first Web 3.0-era solutions based on confidential computing are a step in this direction. We expect more use-cases to evolve over time. - Multi-cloud Key Management as-a-Service (KMaaS) – This refers to the control of keys in one or more public or private cloud service platforms, usually deployed as a SaaS offering and levering a Hardware Security Module (HSM).
Controlling keys across multiple CSPs while supporting Bring Your Own Key (BYOK) initiative to deliver a consistent policy framework for data access with the proliferation of keys, ownership, regulatory requirements, data protection and privacy – all of which are increasingly important in a hybrid and multi-cloud world.
This area while quite mature in some respects is also undergoing transformation as enterprises seek to simplify deployment and governance. Fortanix has a highly differentiated solution addressing this space and we continue to see adoption in leaps and bounds. The enforcement of Shrems-II and GDPR like regulations have also caused public cloud providers with their own key management systems to look at external key management solutions with the likes of Fortanix. Google and Fortanix, for example support a solution for external key management (EKM) on Google Cloud Platform. - Secure Multi-party Computation (SMPC) – This outlines collaboration between different entities allowing each entity to share insights on protected data without compromising privacy.
Fortanix simplifies and secures the process of sharing private data without exposing it to other parties or violating privacy regulations. Multiple parties contribute encrypted data to a trusted execution environment called an enclave, where the data is combined, analyzed and then results are output in an encrypted format back to each party with the results of the analytics.
Data remains encrypted throughout the entire process, protecting the privacy of the data while it is transferred, during computation and while stored. - Format Preserving Encryption – Format Preserving Encryption a.k.a Tokenization has become increasingly popular and relevant in recent times to protect data at rest and in-use for a variety of use-cases, with privacy and compliance requirements being at the top of the food chain. It is regarded as an important anonymization technique. Fortanix has a strong offering here
- Privacy by Design (PbD) – This is a foundational focus area concerned with instituting a culture of privacy intertwined with technology. It is an area of continued investment for Fortanix.
- Enterprise Key Management (EKM) – With cryptography and tokenization becoming mainstays for protecting data, preventing data breaches and ensuring privacy, enterprise key management leverages software or hardware appliances for multiple symmetric encryption solutions, facilitating key distribution, key storage and maintaining consistent key lifecycle management.
Fortanix has a mature EKM solution with 100+ integrations into its Data Security Manager (DSM) platform.
This makes the implementation of key management across the enterprise relatively simpler compared to traditional solutions in the market. The user guide here is an excellent example of the key lifecycle management solution.
With a rich set of capabilities, the Fortanix Data Security Manager (with an on-premises and SaaS version) is architected for a more unified approach to the data security lifecycle.
It combines best-in-class data security capabilities with operational simplicity and flexibility to accelerate the time to value for Enterprise and mid-market organizations globally today.
In addition to the Gartner Hype Cycle for Data Security, Fortanix is also recognized in the following Hype Cycle reports –
- Hype Cycle for Cloud Security, 2021
- Hype Cycle for Compute, 2022
- Hype Cycle for Workload and Network Security, 2022
- Hype Cycle for Edge Computing, 2022
SOURCE:
Gartner Hype Cycle for Data Security, 2022, by Brian Lowans, August 2022
GARTNER and HYPE CYCLE are registered trademarks and service marks of Gartner, Inc. and/or its affiliates in the U.S. and internationally and are used herein with permission. All rights reserved. Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s Research & Advisory organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.

 Cite this article
Cite this article








