Industry Certifications
Transparency
Fortanix advocates transparency as it builds trust. We take great pride in showing our SaaS platform availability We prioritize quality and security during the development of our products. This is reflected in our development process, where we integrate frequent quality and security feedback through various means such as automation, manual review, and collaboration across teams. Additionally, we publish several of our components as open-source software on our Github profile.

Secure By Design
Fortanix was an inaugural member of the Confidential Computing Consortium, alongside companies like Google, Intel, and Microsoft. Confidential Computing protects data in use in a Trusted Execution Environment (TEE). For Fortanix’ DSM, this TEE is realized through Intel® SGX technology. This allows DSM to run isolated from the rest of the system in a so-called secure Enclave, with its data encrypted in memory at runtime. This ensures that nothing other than DSM’s running code has access to sensitive data—not even Fortanix can access this data. Even in the very unlikely case that an attacker gains access to a DSM host, DSM would still protect sensitive data from the host itself and leave the attacker with empty hands.
Fortanix immediately recognized the advantages of using the Rust programming language and built the Data Security Manager platform as early as the 1.0 release of Rust. Rust is widely recognized for producing highly secure code, completely sidestepping the biggest cause of security bugs by enforcing memory safety at the language level, without sacrificing performance.
Fortanix takes security seriously on all fronts, and we use SGX Enclaves as part of a holistic secure-by-design approach for our product architecture. We discern 7 layers of security for each system running a DSM node:

Datacenter Security
We only deploy our systems in highly secure datacenters with a proven track record in security and availability.

Hardened FIPS Validated Chassis
Our systems reside in hardened chassis that protect against physical attacks and conform to the FIPS 140-2 standard.

CIS-Compliant OS
The CIS-compliant host OS uses sensible security defaults throughout the system, and each component has the least amount of privileges needed to function.

Firewall
Each system has a strict set of firewall rules, designed to only let necessary traffic pass.

Intel SGX
The DSM application itself runs in an Intel SGX Secure Enclave, protected from the host OS.

FIPS-Validated Software and Hardware
DSM is a FIPS-validated cryptographic module, meaning that not just the application itself but also its environment are carefully controlled to maximize security.

Side-Channel Resistant Crypto Libraries
We take great care to verify that our cryptographic libraries can resist side-channel attacks, securing cryptographic operations even when the underlying OS is compromised.
You Control Your Keys & Data
With Fortanix’s FIPS 140-2 Level 3 validated Hardware Security Modules (HSMs) and the Confidential Computing technology, customers are assured they stay in control of their keys. Instead of using CSP-native Key Management Systems (KMS), Fortanix simplifies operations with a centralized key manager and takes the root of trust outside of the CSP platform. This way, neither the CSP nor Fortanix can access customer keys and decrypt their data.

Key Provenance
The Fortanix Data Security Manager SaaS platform can provide signed Provenance Attestation messages for the keys it generates. This allows a relying party such as a Certificate Authority to verify that a key pair was generated in DSM SaaS. The signing key hierarchy for Provenance Attestation messages is based on a private Root Certificate available at the following URL:
Fortanix Attestation and Provisioning Root CA
The Certification Policy documents for this Public Key Infrastructure can be found at the following URLs:
attestation-and-provisioning-root-ca-CP.pdf
service-attestation-pki-CP.pdf
For more information about working with Provenance Attestation messages, see the Fortanix DSM SaaS documentation.

Availability
Data Security is a fundamental part of any business’ continuity. Hosting an organization’s encryption keys for daily operations is an enormous responsibility. For Fortanix, the uptime of our SaaS platform is one of the main priorities. Site Reliability Engineers work in shifts to ensure personnel is available 24/7 to address incidents before they become external disruptions. Furthermore, these teams ensure our customers get all the scale and performance they expect from a critical SaaS solution. The system status is publicly available: status.fortanix.com.
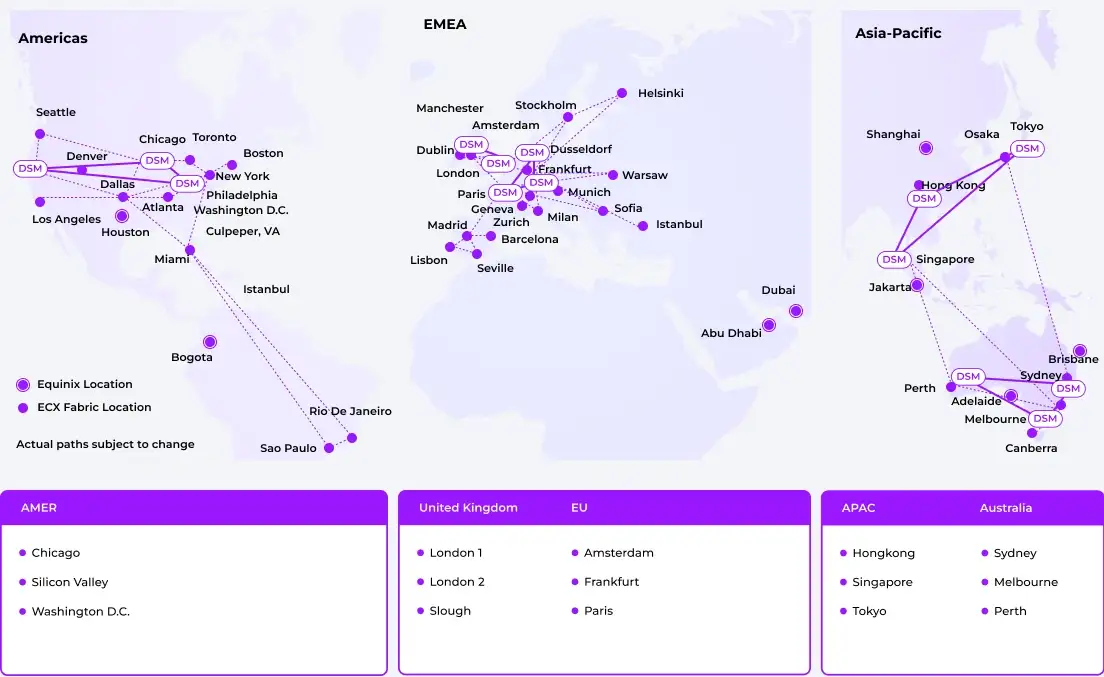
The platform has multiple levels of geographic and regional redundancies, with datacenters worldwide. Three separate datacenters or “availability zones” serve customers in each region to ensure high availability in case of a disruption. Data is replicated synchronously between all nodes in a region, while daily off-site backups ensure continuity even if the worst happens.
Vulnerability Reporting
External parties that believe to have found a security issue within any product or infrastructure managed by Fortanix are invited to report their findings to the Fortanix security team at security@fortanix.com. If your report includes sensitive information, encrypt it using our PGP key.
Please include the following information in your report:
- A description of the issue, including preconditions for exploitation.
- Version numbers of the software affected.
- Steps to reproduce.
- PoC, if possible.
- Your contact details, including your PGP public key if applicable.
- Any other relevant information.
All Fortanix-managed products and infrastructure are in scope, except:
- Social engineering attempts.
- Physical attacks (e.g. at our offices or data centers).
- (Distributed) Denial of Service attempts.
- Compromising employee accounts in any way.















