Problem Statement Overview
To protect your company’s sensitive data, you must first find it and then classify it as either sensitive or non-sensitive data - after all, you cannot secure the unknown. Originally cybersecurity was a very straightforward process; first, secure the network edge or perimeter and then secure the layers in an inward progression. Data security, while considered important, was often the last area to receive budget allocation. As data privacy laws and regulations became more common, companies began to realize the value of their data and how bad of a risk a data breach could be. Companies shifted their focus towards a more granular level of data security, including finding where all their data resides, classifying it, and providing the right level of protection for it. But the solution became increasingly difficult, as data began to grow at increasingly faster rates throughout their company’s environment, creating challenges to even locate the data. Then the shift towards the cloud, multicloud, and hybrid environments exponentially made what was already a huge undertaking to find the data even more difficult.
"To ensure data security, it is critical to have a unified way to find, classify and protect data. Organizations must build the right data security governance and controls to account for constantly changing data-sharing requirements and privacy laws. As more organizations use multicloud data lakes and analytics pipelines, the complexities of hybrid work and digital transformation make it more challenging for them to maintain control and protect the data."
Imperva Data Security Fabric (DSF)
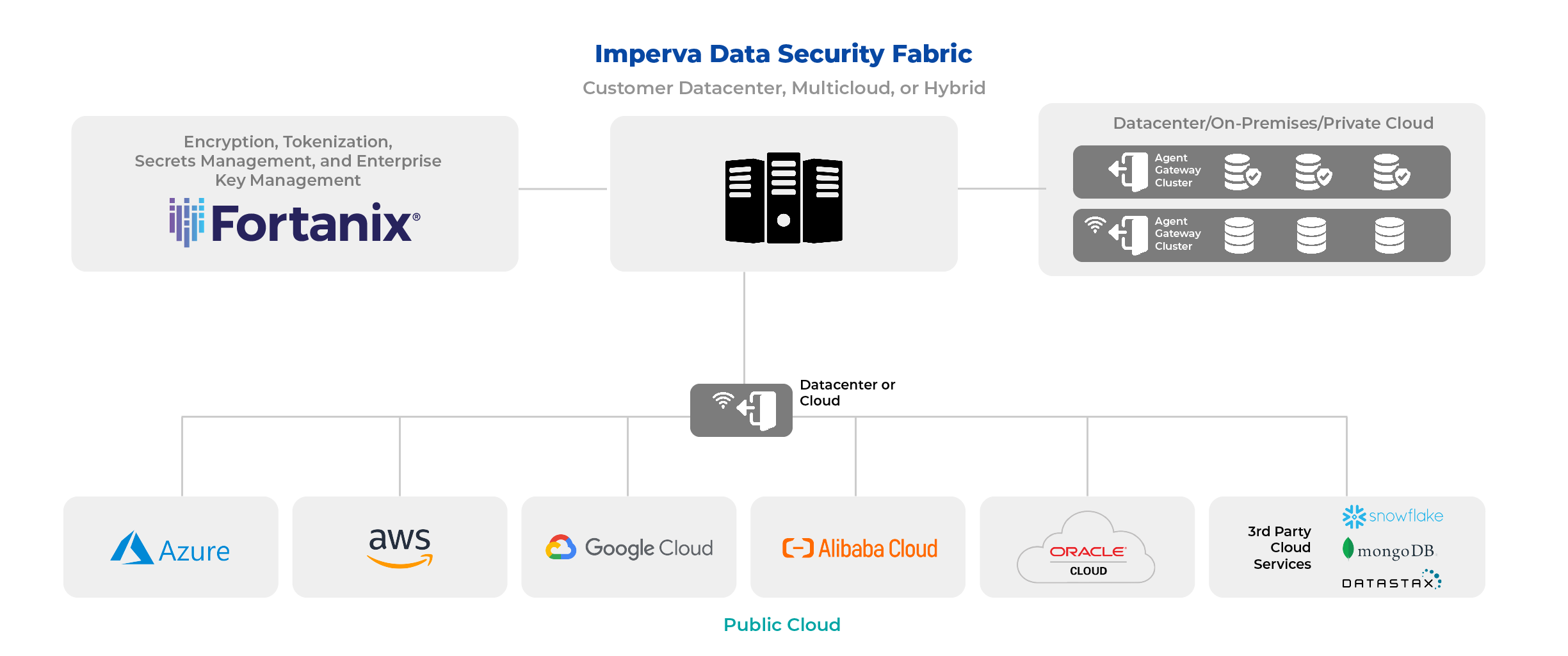
The award-winning Imperva Data Security Fabric (DSF) discovers, classifies, and secures all high-value data across file systems and data repositories.
Imperva Data Security Fabric (DSF) is a data-centric solution that enables security and compliance teams to quickly and easily secure sensitive data no matter where it resides with an integrated, proactive approach to visibility and predictive analytics.
Imperva’s Data Security Fabric solution simplifies data governance, security, and workflow management for sensitive data (structured, unstructured, and semi-structured) across multicloud and hybrid environments. This integrated solution helps organizations demonstrate compliance with industry regulations and maintain a strong data security posture through automated processes, audit analysis, and customizable reports. In addition, the Data Security Fabric solution accelerates incident responses, and forensic investigations with centralized management, prioritization of context-aware security alerts, and advanced analytics.
The following capabilities are available as a part of Imperva’s Data Security Fabric (DSF) solution:
- Data Activity Monitoring (DAM)
- Data Discovery and Classification
- Data Access Control
- Data Risk Analytics (DRA)
- Mitigation & Response
- Threat Detection & Prevention
- Compliance Management
State-of-the-Art Data Security
The Imperva Data Security Fabric (DSF) uses a combination of data science, machine learning, and behavior analytics to provide real-time protection for data repositories against internal and external threats, monitor user activity while alerting data security teams of suspicious behavior that exceeds the normal user behavior baseline. Data Security teams can utilize the Imperva DSF dashboard to provide visibility into suspicious behavior, where sensitive data resides, who is accessing it, if sensitive data is protected with the proper controls, automated risk and compliance reporting, as well as explanations to assist them, so they can quickly analyze the situation and respond to them.

Fortanix Data Security Manager
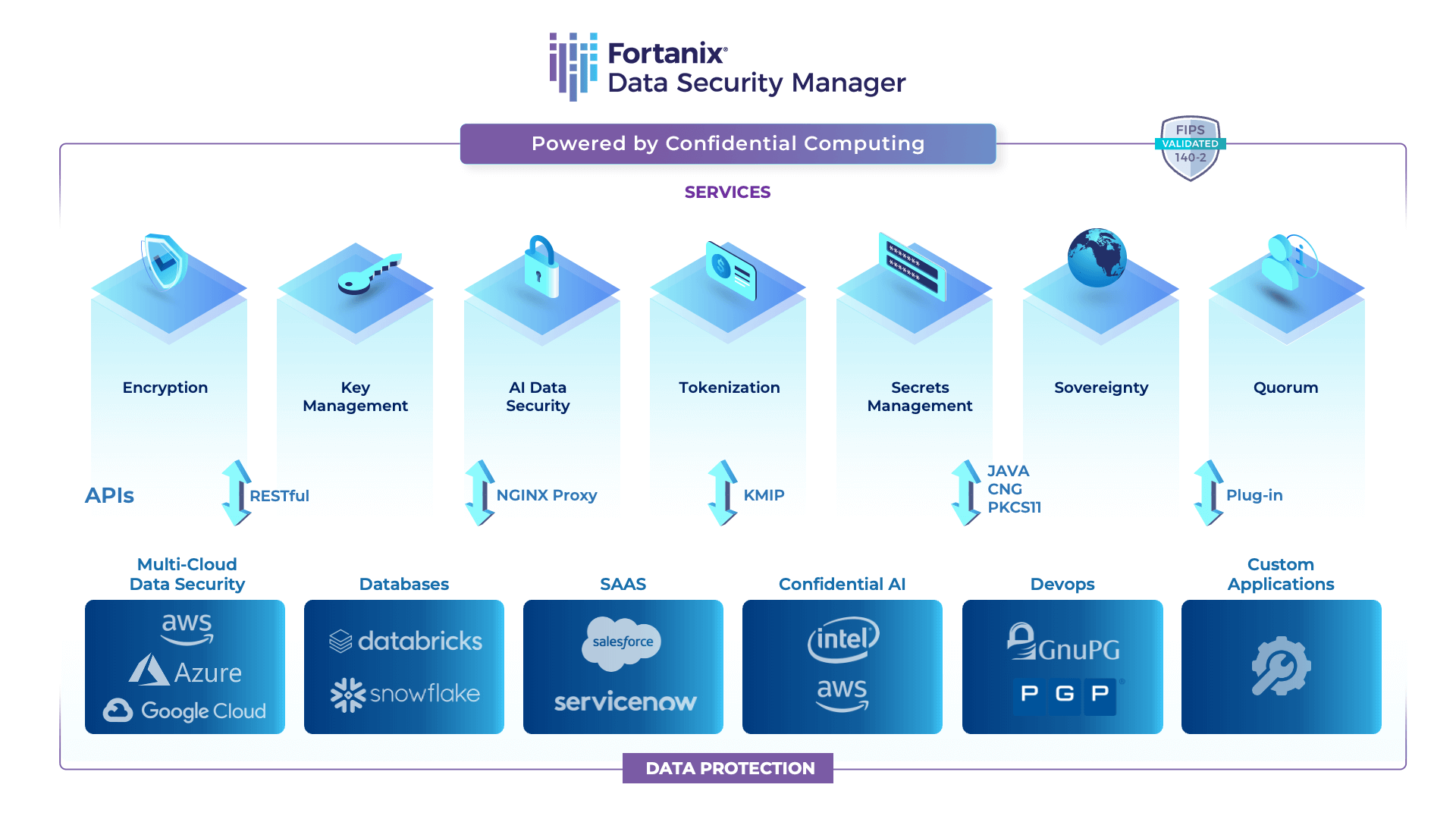
Fortanix Data Security Manager (DSM) is a unified data security platform that delivers a wide range of data security services, including encryption, multicloud key management, and format-preserving encryption, /tokenization, /data masking, TDE, and several others from one single console. It is powered by confidential computing and enables secure generation, storage, and use of cryptographic keys, certificates, and other secrets such as passwords, API keys, or tokens.
UNIFIED DATA PROTECTION: Fortanix Data Security Manager delivers HSM, Key Management, Encryption, Tokenization and other security capabilities for your hybrid and cloud-nativeapplications, all from the same integrated solution.
REST API-DRIVEN ARCHITECTURE: Powerful RESTful APIs make it easy for developers and DevOps teams to use and integrate data security into their applications.
FLEXIBLE DEPLOYMENT: Primarily delivered as a SaaS offering, it also offers other deployment options- on-prem appliance, software, and virtual deployments.
SUITED FOR ANY IT INFRASTRUCTURE: The platform secures data across your IT infrastructure including all cloud platforms (AWS, Azure, GCP), databases (Oracle, SAP HANA, SQL, Server, and more) and applications like ServiceNow, Snowflake, Salesforce etc.
POWERED BY CONFIDENTIAL COMPUTING: With Fortanix Confidential Computing technology powered by Intel® SGX secure enclaves, data always remains secure across its lifecycle- at-rest, in-transit, and in-use.in-use.
Imperva and Fortanix Better Together
To protect your data, it must first be located and classified. By using the joint solution from Imperva and Fortanix, your company will be able to achieve an end-to-end process of data discovery, classification, and encryption/tokenization that enables your company to reduce risk, increase your company’s data security posture management while streamlining and simplifying your regulatory compliance efforts.
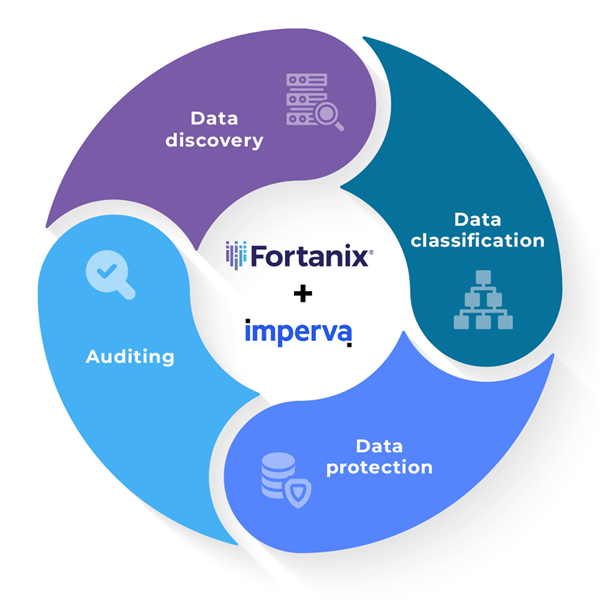
The Imperva Data Security Fabric solution enables customers to discover sensitive data wherever it resides and to classify it, so that it may be protected by Fortanix. The company can then use the Fortanix Data Security Manager to secure the data through encryption, and tokenization. Fortanix encrypts and tokenizes the sensitive data in structured databases using a REST API via the DSM Graphical User Interface.
Fortanix DSM then secures sensitive data through cryptographic techniques to protect it. Encryption keys are stored in the Fortanix FIPS 140-2 Level 3 certified HSM, and cryptographic operations are securely executed within the module. Once the encryption is done via Fortanix, only the customer can validate the results via the Imperva Data Security Fabric console and reports.
Key Benefits
- Discover, classify, and secure—all kinds of data, no matter where it resides (cloud, multicloud, on-premises, and hybrid environments).
- The combined solution facilitates all types of data security, confidential computing, and cryptographic needs such as encryption, tokenization, and enterprise key management.
- Sensitive data is safeguarded from insider and external threats
- Protected data is still useful due to the ability to preserve the data semantics and inherent functional properties.
- Data security can be achieved at scale, with minimal latency and high throughput using the combined solutions of DSF + DSM.
Top Benefits

Discover, Classify, and Protect Data

Data Security with Zero Boundaries

End-to-End Data-centric Automated Data Protection

Lower TCO

Simple and Scalable

High availability and security