Challenge
Backup data is not only critical for business continuity, but it also acts as a last line of defense against data breaches and sophisticated ransomware attacks. Ponemon Institute report quantifies the average cost of a single ransomware attack at $5 million due to productivity loss, downtime, and information theft, while the cost of a data breach averages $8.64 million in the United States. To reduce cybersecurity risk, organizations should encrypt backup data to avoid data loss, ensure availability and avoid regulatory penalties. While encrypting data is easy, securing encryption keys from cybercriminals requires enterprise key management to provide secure access control and a Hardware security module (HSM) to securely store keys.
Cohesity eliminates mass data fragmentation by consolidating data silos onto a single, easy-to-manage multicloud data platform. It hosts enterprise-class data services, including backup and recovery, file shares, object stores, DR, dev/test provisioning, and analytics. The joint Cohesity and Fortanix solution provide a unified data security platform that includes immutability, WORM, RBAC, and full enterprise key lifecycle management, a FIPS 140-2 level 3 HSM, encryption to protect backup data from ransomware and data breaches. The solution also helps avoid regulatory penalties from General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), and other privacy regulations. The Fortanix Data Security Manager integrates seamlessly with Cohesity to secures data across multiple public clouds, hybrid, and on-premises environments.
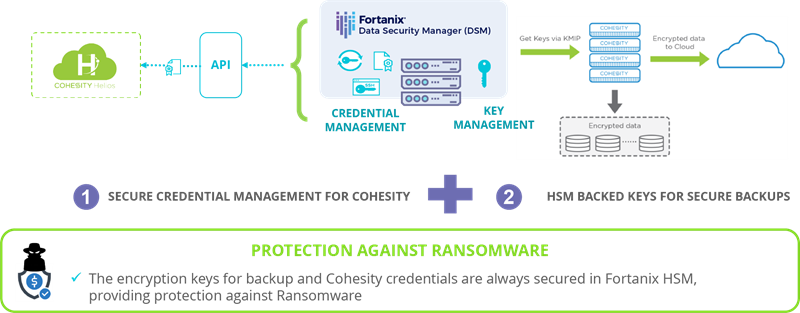
The Fortanix and Cohesity joint solution provides critical layers of defense including:
- ENTERPRISE KEY MANAGEMENT-
Fortanix secures cryptographic keys, protecting backup data whether it is in the cloud or on-premises. With an intuitive web-based interface, businesses can now manage all the data keys from a single centralized platform. - COMPLETE SECURITY FOR DATA AND KEYS -
Fortanix provides end-to-end security for keys and data (at-rest, in-transit, and
in-use) protected with a FIPS 140-2 Level 3 HSM and layers of defense including Fortanix Runtime Encryption® technology. - VERIFIABLE AUDIT AND ACCESS CONTROL FOR COMPLIANCE -
Fortanix enforces policies that protect against unauthorized access and provides secure, comprehensive, tamper proof audit logs that meet compliance requirements.