Challenges with existing solutions
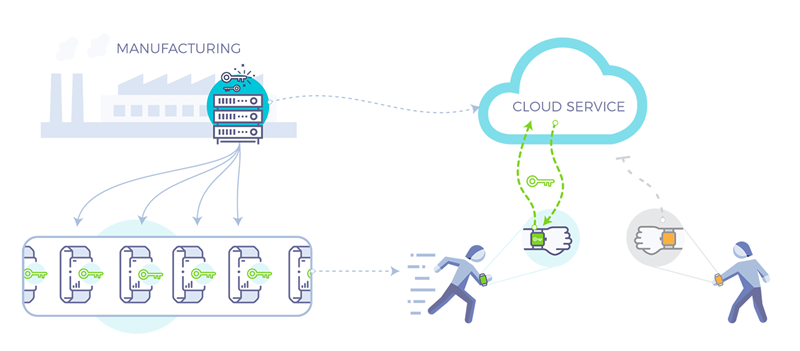
Manufacturers typically rely on Hardware Security Modules (HSMs) to secure the device keys. The keys are generated at the company headquarters (HQ) and exported securely using a wrapping key. The wrapped keys are then transmitted to another HSM at the manufacturing site where they keys are unwrapped and injected into the devices during the manufacturing process.
Device manufacturers face a growing threat from counterfeit devices, which have the potential for severe financial and brand reputation damage. These devices are typically manufactured in remote sites that may not have the same level of security as the company headquarter.
Organizations have traditionally addressed this problem by injecting cryptographic keys into devices during manufacturing. However, managing this injection process in today’s cloud-centric and geographic-disparate world requires a new solution.
Fortanix DSM delivers a scalable cloud-native solution for an end-to-end management of the manufacturing process across global sites, including those not connected to Internet.
The traditional approach based on HSMs struggles to meet the following requirements:
- The company may use a mixture of on-premises or cloudbased infrastructure. And, thus it needs a solution that supports hybrid and multi-cloud scenarios.
- Many IOT devices now reach many millions of users, e.g., smart meters or smart thermostats. Thus, the solution should scale with the business requirements to millions or billions of keys and be able to perform crypto operations at a very high rate.
- Since any failure can cause disruption at the manufacturing site, the solution must be extremely reliable and resilient.
- The company should have full control of the entire key injection process at the manufacturer sites, even when these sites are not connected to Internet. The company may establish policies controlling the rate of production or the number of devices at a site.
The traditional HSMs have limited availability in cloud and offer limited built-in capabilities suitable for manufacturing devices. Thus, the companies had to develop custom code to run in secure execution environment offered by HSMs. However, the custom code development is a painful process reliant on a limited and complex SDK. The HSMs themselves pose significant operational challenges, accentuated even more in the remote environments.
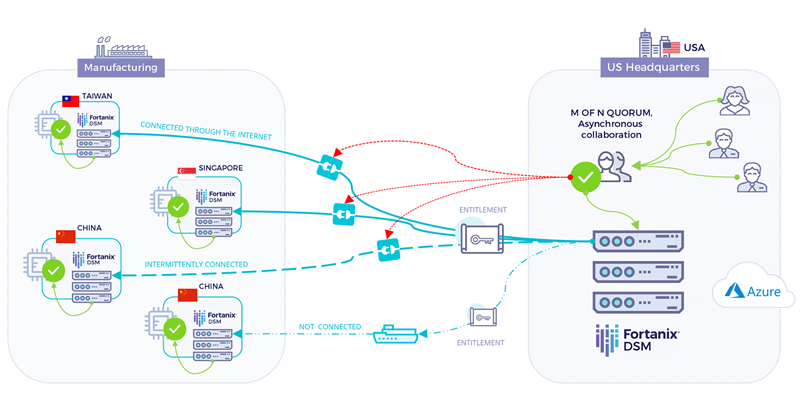
Secure Manufacturing using Fortanix DSM
Fortanix DSM is the ideal solution for secure manufacturing. It is secure, reliable, highly available, and horizontally scalable. The Runtime Encryption Plugin feature in Fortanix DSM allows custom code to be run in a trusted execution environment. This allows policies for usage and access control of keys to be defined and enforced by a device manufacturer across multiple sites.
An IoT device manufacturer typically deploys a Fortanix DSM cluster at the headquarters, and a Fortanix DSM cluster at each manufacturing site. Each of these clusters contains a certificate issued by a common root CA, which allows the site clusters to trust the cluster at the headquarters. There is no network connection between the Fortanix DSM clusters at the two sites.
The following are the sequence of events in the secure manufacturing process:
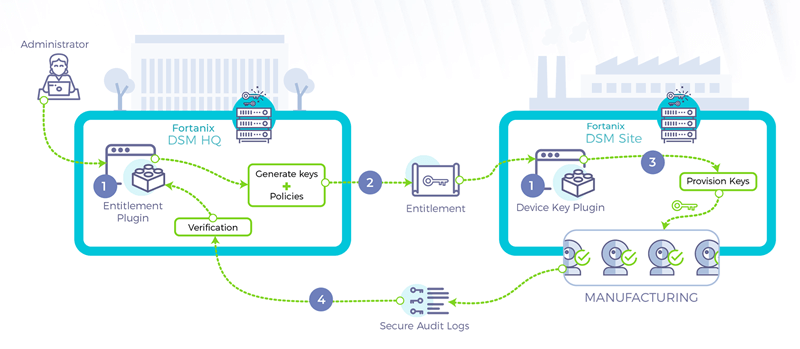
- The device manufacturer creates a Fortanix DSM cluster at its headquarters (called “Fortanix DSM HQ”). Another Fortanix DSM cluster is created at the manufacturing site (called “Fortanix DSM Site”). The processing at both ends is done within Runtime Encryption plugins — an “Entitlement Plugin” at Fortanix DSM HQ, and a “Device Key Plugin” at Fortanix DSM Site.
- Entitlement Plugin generates a set of keys and associated policy for usage of those keys, and then creates a package with this information. The Entitlement Plugin then encrypts the package with the public key of the Device Key Plugin. The encrypted package is finally signed with its private key to create the final entitlement. This entitlement is then transmitted to Fortanix DSM Site.
- The Device Key Plugin at Fortanix DSM Site receives the entitlement. It first verifies that the entitlement is signed by a plugin it can trust. This is ensured by the PKI infrastructure in place which issues certificates for Fortanix DSM HQ and Fortanix DSM Site. Then it uses its private key to decrypt the entitlement. The plugin then launches the process for provisioning the keys according to the policy specified in the entitlement. During the process, the plugin logs its activities. This audit log is then encrypted using the public key of the Entitlement Plugin and signed using the private key of the Device Key Plugin. The signed and encrypted audit log is then sent back to Fortanix DSM HQ.
- The Entitlement plugin receives the signed and encrypted audit logs. It verifies that the logs have been signed by a FortanixDSM cluster that it can trust, and then decrypts the logs. The plugin then analyzes the decrypted logs to verify that the policy of key usage has been enforced at the manufacturing site.