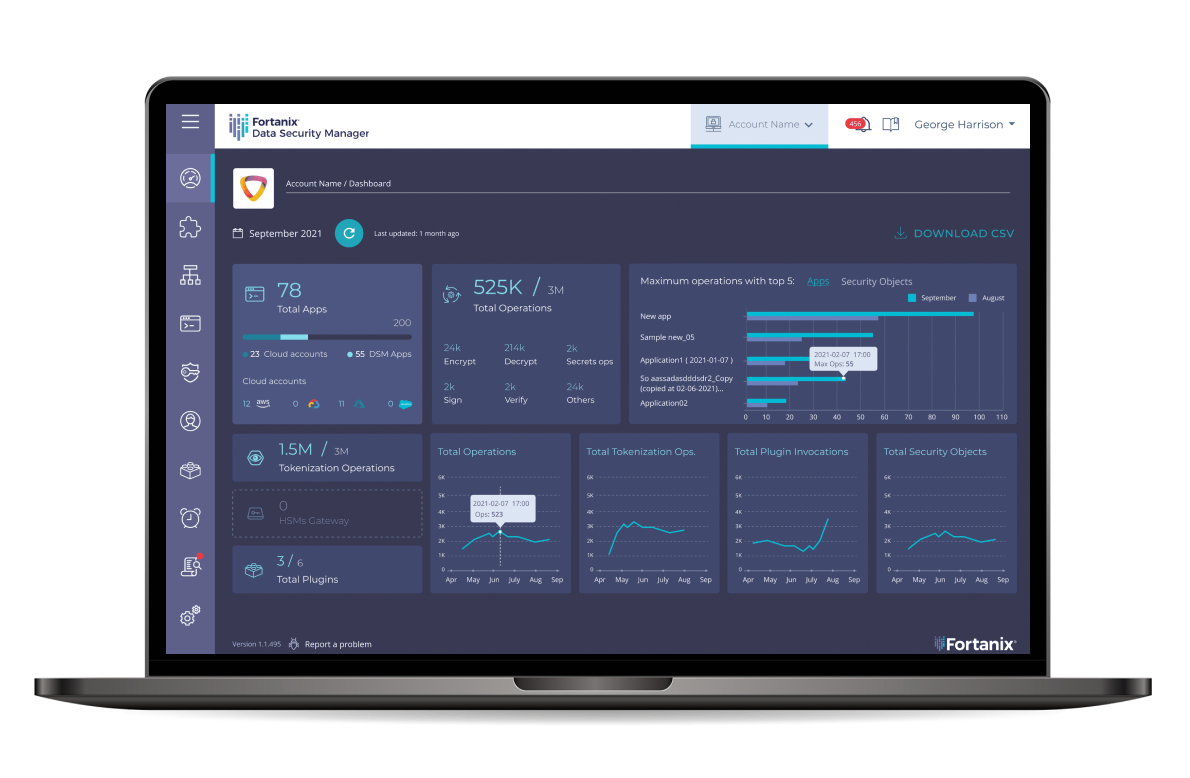
Problem
Digital business transformation is built on a foundation of digital trust. Best practices for digital trust rely on cryptography to protect sensitive data. Today, data goes unprotected because cryptography is often underutilized, misconfigured, and siloed between different environments and groups within an organization. To build digital trust, accelerate digital transformation, and minimize the risk of data breaches, it is critical that businesses use a pervasive encryption approach that standardizes and centralizes cryptographic operations so that encryption becomes universal across all applications, infrastructure, and digital information.
Solution: Pervasive Data Protection Platform
The Fortanix solution delivers a cloud-scale pervasive data protection platform that provides cryptographic services, shared secrets, and tokenization across cloud and on-premises environments from a single centralized point of management, control, and audit. With this powerful new platform, businesses can reduce breach risks, develop secure applications faster, and unlock new revenue-generating opportunities from their data.
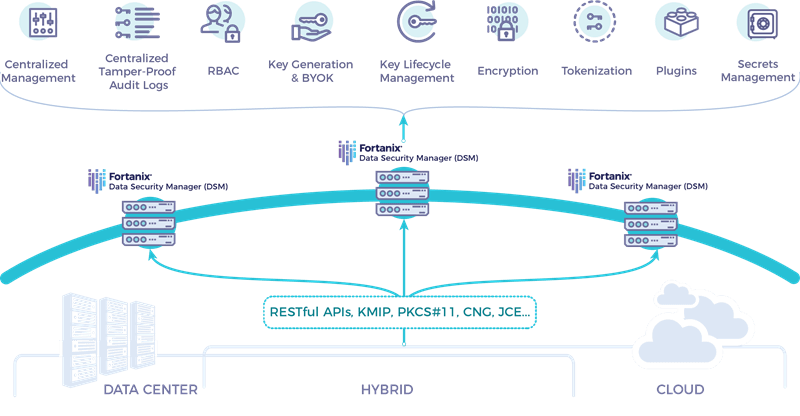

Digital business transformation is built on a foundation of digital trust. Best practices for digital trust rely on cryptography to protect sensitive data. Today, data goes unprotected because cryptography is often underutilized, misconfigured, and siloed between different environments and groups within an organization. To build digital trust, accelerate digital transformation, and minimize the risk of data breaches, it is critical that businesses use a pervasive encryption approach that standardizes and centralizes cryptographic operations so that encryption becomes universal across all applications, infrastructure, and digital information.
Gartner, Hype Cycle for Data Security, 2019, Brian Lowans

How Pervasive Encryption Protects Digital Business
Encryption as a Service
A modern API-driven encryption platform that integrates seamlessly with hybrid, public cloud, and on-premises applications.
Encrypt PII in Public Cloud
Protection for sensitive data in the public cloud that enables businesses to move highly regulated data in financial services, healthcare, and government to the cloud.
HSM Replacement
Replace antiquated and costly hardware security modules (HSM) that don’t support multiple sites, clustering or Rest APIs with a FIPS-validated modern encryption platform.
Database Key Management
Centralize the management of keys for transparent database encryption across multiple types of databases, improving security and eliminating administrative complexity.
Data Privacy Compliance
Encrypt regulated data while in use by applications to enable cross-border movement of sensitive data without violating data privacy laws.
Secure Multi-Party Analytics
Enable businesses to combine sensitive data together to extract business insights from analytics without exposing the underlying data sets to other parties.