Data and Security Silos Growing
Data breaches lead to massive monetary losses, hefty penalties, and severe brand damage. While traditional firewall and cloud security defenses shield the perimeter, the data itself remains vulnerable. Encryption is the final line of defense, but enterprises lack robust control over encryption keys, leading to significant risk. The proliferation of data and encryption key silos creates control and visibility challenges for security and compliance teams. They aim to reduce data exposure risk by tracking and analyzing all encryption keys and related data services. However, discovering keys across a dispersed environment requires complex and often manual data collection, distracting teams from strategic security projects such as post-quantum preparations.
Furthermore, security teams struggle to quickly assess if they comply with data security best practices or other policies and must navigate a wide array of point products to govern consistent and scalable crypto policy.
What these teams need most is the discovery, visibility, and assessment of all disparate data services and associated encryption keys across a hybrid multicloud infrastructure. They also need an agile and scalable way to mitigate discovered risks and misalignments with established regulatory and data security policies and standards.
Discover, Assess, and Remediate Data Security Gaps
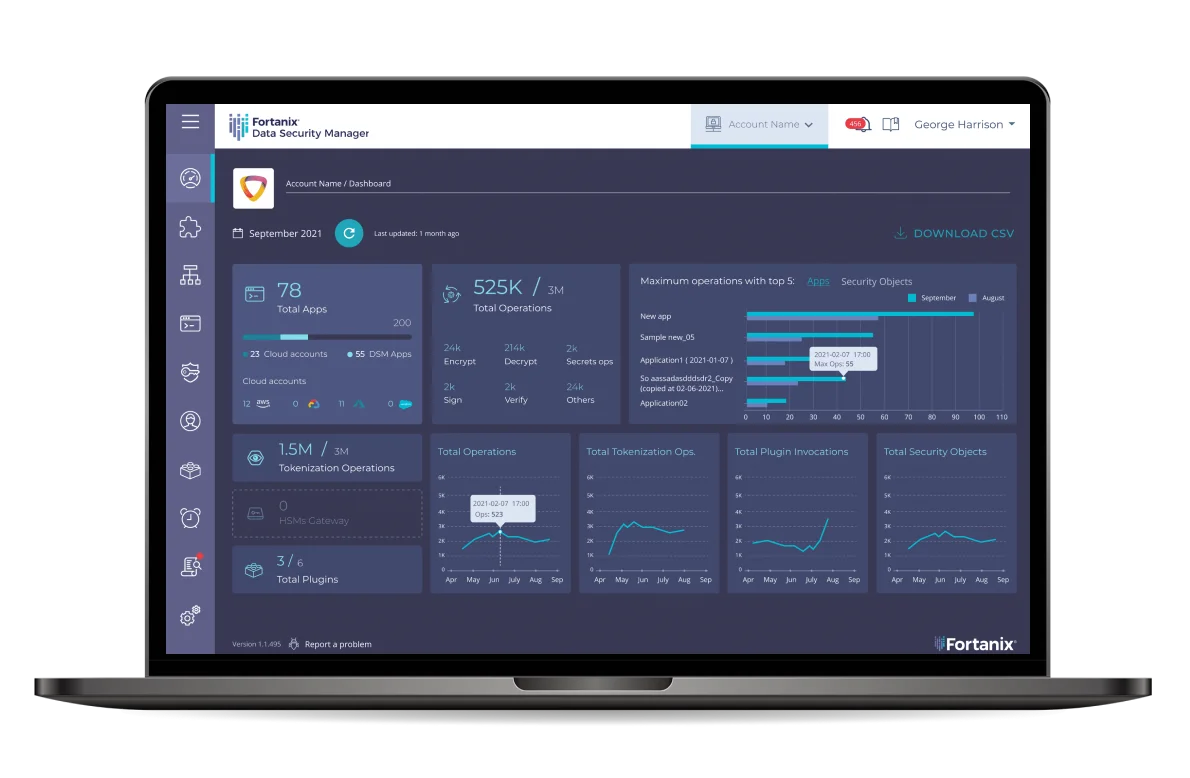
Fortanix Key Insight automatically discovers your encryption keys and data services across the silos created by perimeter-focused security in hybrid multicloud environments. A unified dashboard shows the mapping of your keys and data services and provides details of your cryptographic security posture.
Security and compliance teams get data-driven insights to quickly define the biggest data security risks and show the alignment with security best practice policies and industry regulations. The information is organized by key type, source, status, etc., enabling security teams to quickly identify the types and utilization of keys, assess the encryption status of services, and evaluate the overall cryptographic security posture of the organization.
With this insight, organizations get increased awareness of the most pressing data security and compliance risks and can quickly implement corrective actions to improve the cryptographic security posture and track the progress.
Fortanix Key Insight enables proactive, continuous mitigation of data exposure risks. The solution provides crypto-agility to quickly transition to a more robust cryptographic security posture and prepare for the post-quantum era.
Key Features
- Discover and catalog your keys and data services – Monitor all encryption keys in multicloud environments, their
lifecycle management status, and how they relate to cloud data services from a central view. - Unified dashboard with drill-down capabilities –Out-of-the-box dashboards to monitor cryptographic security
status, including various violation types that need attention. - Automated data collection – Dynamically collect siloed information about all keys and data services that belong to the organization or individual accounts.
- Data-driven heatmaps – Quickly identify the biggest data security risks and prioritize the recommended next steps.
- Quantum key detection – Identify vulnerable keys that lack quantum-resilience.
- Cryptographic Security Score – Monitor your overall cryptographic security status with one indicative score.
- Service key relationship – Pinpoint at-risk services with an intuitive key-service relationship diagram.
- Blast-radius assessment – Analyze the blast radius of an at-risk service in a simple diagram.
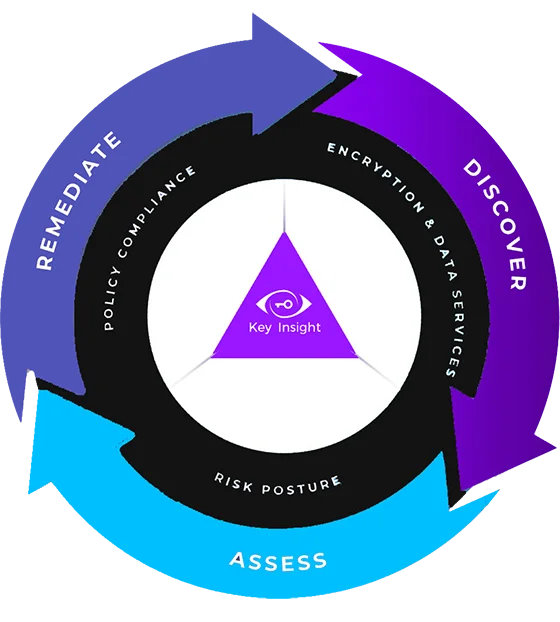
Benefits
Discover and reveal your data security blind spots.
Eliminate security blind spots and discover data exposure risks across on-premises datacenters and multicloud environments (hybrid multicloud).
Validate and prove compliance
Increased awareness and proactive insight into the most pressing data security and compliance risks.
Accelerate productivity and efficiency.
Faster security improvements and continuous compliance, with a more efficient use of resources.