Challenge
Google Workspace has been the productivity suite of choice for small businesses and Fortune 500 corporations alike. Needless to say, it safely harbours petabytes of sensitive or regulated data belonging to these organizations.
While Google runs atop the latest cryptographic standards, many organizations seek greater security and control over their cloud encryption keys. Especially the ones which operate in highly regulated industries — like defence, aerospace, or government. Housing the authentication keys separate from the storage system makes the data indecipherable to the CSP. At the same time, users can continue to leverage their collaborative services, access content on numerous devices, and share encrypted files externally.

Solution Overview
With Fortanix Data Security Manager SaaS (DSM SaaS), customers can bring a FIPS 140-2 Level 3 certified External Key Management Service for Google Workspace. Fortanix DSM SaaS integrates directly into Google Workspace Client-Side Encryption (CSE) capability for external key management. CSE allows customers to protect their data in Google Cloud — separating data from the key. The database encryption keys are managed outside of Google Workspace in the customer’s Fortanix DSM SaaS account.
Complete control over encryption keys:
For leveraging Google CSE users need to need to set up their encryption key access service with an external key manager that abides to CSE requirement.
No access to plaintext content:
For leveraging Google CSE users need to need to set up their encryption key access service with an external key manager that abides to CSE requirement.
Minimized impact on user experience:
For leveraging Google CSE users need to need to set up their encryption key access service with an external key manager that abides to CSE requirement.
Top Benefits

Centralized Management

Speedy Setup

Key provenance

Unmatched Scalability

Superior Control
Joint Value Proposition
Google Workspace Client-side encryption aims at bolstering data confidentiality while touching upon a varied range of data sovereignty and compliance requirements. This is in addition to the industry-leading cryptographic standard that Google uses to encrypt all data at rest and in transit between facilities.
Fortanix Data Security Manager integrates with Google Workspace External CSE to replicate the same level of security for the keys as in an on-premises environment while moving their data to the cloud. Not only is the data undecipherable to Google, but the encryption keys are also never stored in GCP. The user has complete control over the authorization of Google Workplace data and keys.
Users also get to define and control policies for Google Workspace Key Encryption Key (KEK) from Fortanix DSM SaaS account. Upon receiving the file, the corresponding data encryption key is decrypted using customer-provided keys only after authenticating the user with customer-controlled authentication.
Fortanix DSM SaaS provides FIPS 140-2 Level 3 hardware-based protection, with complete separation between users and regions as needed. It also offers centralized management with audit logging, enterprise-level access controls, multisite and hybrid cloud support, built-in encryption, key management, tokenization, and support for various interfaces, including REST APIs, PKCS11, CNG JCE, and KMIP.
Core Integration Features
How Does Google Client-Side Encryption Work?
Google Workspace CSE works for browsers and mobile apps by encrypting and decrypting content on the end user’s devices. The Google Workspace client calls into Fortanix DSM SaaS that the customer has configured and deployed, and the client performs cryptographic operations to seal and unseal Google Workspace content.
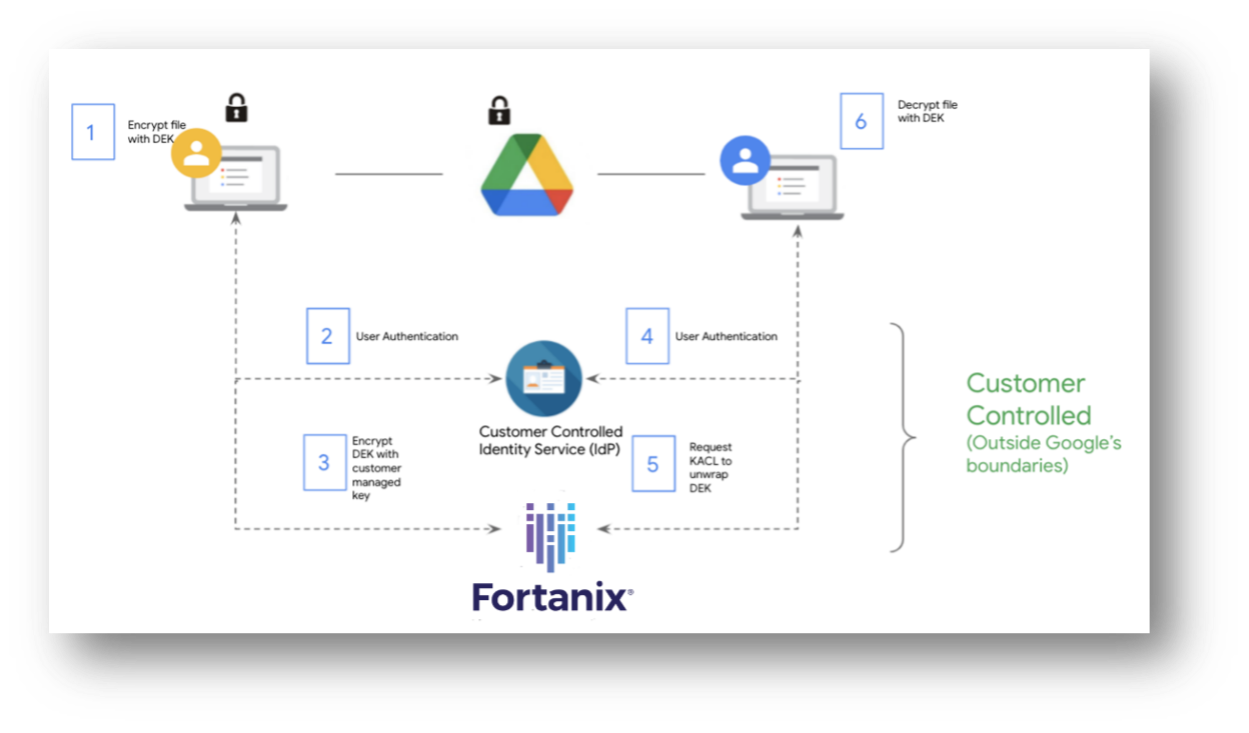
Google Workspace CSE uses envelope encryption to protect data and it relies on web browsers for performing client-side operations. First, a data encryption key (DEK) is generated in a Google Workspace client, and it’s used to encrypt the data symmetrically. Then the DEK is handed over to Fortanix DSM SaaS to be encrypted symmetrically using a Key Encryption Key (KEK). The encrypted content and the encrypted DEK are then sent to Google infrastructure for storage.