Monthly Newsletter
January 2025

The U.S. Cybersecurity Revolution: Are We Ready A New Dawn in Cyber Defense: Understanding Executive Order 14144
The recent executive order from the White House has sent ripples through the cybersecurity community, marking what may be the most decisive shift in the nation's approach to cyber defense in recent history. The order demands the establishment of AI programs for cyber defense, mandates post-quantum security readiness, and insists on upgrades to hardware security modules and trusted execution environments. The implications of the executive order extend far beyond government networks. Read the blog by our founder and CEO, Anand Kashyap, to learn how to take a proactive stance to ensure that AI serves as a shield rather than a vulnerability.

Protect data at rest with Fortanix and IBM Hyper Protect Services
IBM and Fortanix have teamed up to enhance data protection. Their solution combines Fortanix Data Security Manager with IBM Hyper Protect Services and FIPS Level 4-certified Hardware Security Modules. This allows businesses to secure critical assets in a scalable, virtual environment using their existing infrastructure.

Gartner® Report: How to Improve Data Security with Cloud Key Management
In this Gartner report, you will learn:
- What data risks are created due to residency, security, privacy, and compliance requirements
- Risk factors associated with different cloud key management choices
- How to evaluate the available cloud Bring Your Own Key (BYOK) or Hold Your Own Key (HYOK) and KMaaS technology options
- Strategies for selecting a key management to achieve the right balance between security and performance

New Integrations
● Nutanix :
Integrating Nutanix Acropolis Hypervisor (AHV) and Fortanix Data Security Platform delivers comprehensive security and encryption capabilities for enterprise virtualization environments. This solution enables organizations to protect their virtualized workloads while maintaining the simplicity and efficiency of Nutanix's hyper-converged infrastructure.
● Couchbase:
Integrates with Fortanix's Data Security Manager to provide robust encryption and key management capabilities for sensitive data. This integration allows organizations to leverage Fortanix's encryption services while maintaining Couchbase's high-performance NoSQL database capabilities.
● Dell PowerFlex :
The integration of Fortanix Data Security Manager (DSM) with Dell PowerFlex using CloudLink provides robust data encryption and centralized key management. Through KMIP server configuration, this solution enables secure data protection, key lifecycle management, and regulatory compliance while maintaining PowerFlex's high performance and scalability for modern workloads.

Webinar: How to Prepare Your Organization for PQC
This webinar explore the challenges and best practices for integrating PQC into your software supply chain. We discussed:
- The NIST PQC standards: Learn about the recently standardized PQC algorithms (ML-KEM, ML-DSA, and SLH-DSA) and their implications for security.
- Navigating the software supply chain: Understand the complexities of modern software development and the challenges of managing cryptographic dependencies.
- The role of Software Bills of Materials (SBOMs): Discover how SBOMs can help identify and manage cryptographic components within your software ecosystem.
- Streamlining PQC migration with Fortanix Key Insight: Explore how Fortanix Key Insight can simplify the process of identifying, assessing, and mitigating risks associated with PQC migration.

Carahsoft Webinar Series: Prepare for the Post-Quantum Cryptography Era with Fortanix
Join us on February 6 to continue the conversations from AFCEA WEST in a webinar in which you will learn how Fortanix can empower the DoD and its partners to stay ahead of the quantum threat.
During this webinar, attendees will:
- Discover automated cryptographic key discovery and manage inventory
- Implement role-based access control (RBAC) for human and machine users
- Configure policy management and auditability
- Achieve scalable, agile cryptographic implementation and control for future-ready security
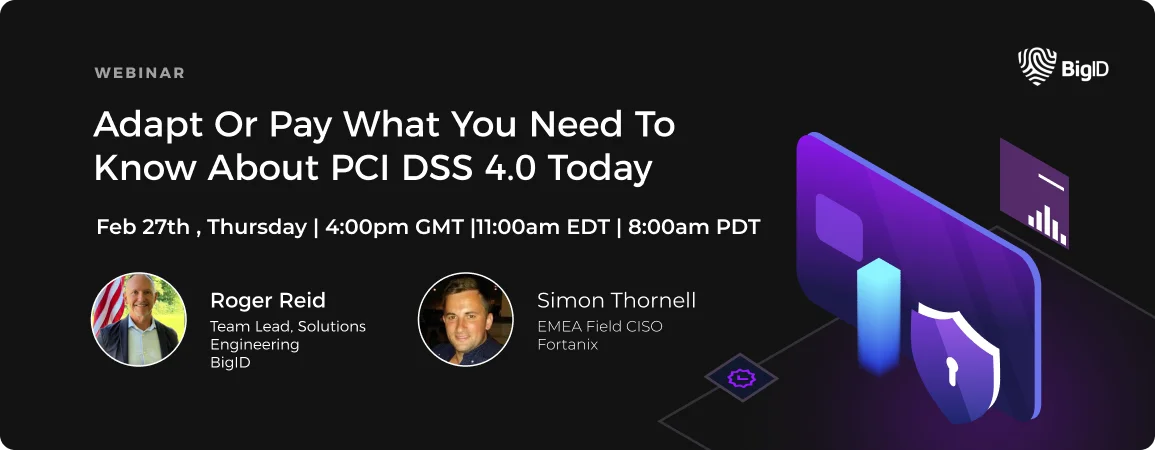
Adapt or Pay: What You Need to Know About PCI DSS 4.0 Today
Join BigID and Fortanix in an exclusive webinar to help you navigate the complexities of data security for PCI DSS 4.0. In this webinar, you will learn:
- Key new data security requirement for PCI DSS 4.0
- How to pinpoint sensitive payment and cardholder data across databases, cloud environments, and messaging apps and then apply the right data security solution to meet the new standard requirements
- How the right technology partners can help your organization comply faster and more efficiently