For historical reasons and technological barriers traditional HSM and key management did not, and still cannot, be delivered as a managed service. And that has been the case for the last 25 years.
But what if they could be delivered as a secure, easy and simple to consume managed service? Would you consider it? If you would — this post is for you.
The Problem
Enterprises, large and small, require encryption services, and the needs are increasing fast:
- Migration to the cloud accelerates the need: Data stored on public clouds must be encrypted at all time (no need to mention ad-nausea the daily data breaches). So does the data in motion that moves from the cloud to the users and back to the cloud.
- Compliance introduces increasing requirements for data protection and thus accelerates the needs.
- And then there is GDPR!
The Gap
Presently, most enterprises do not have in-house skill-sets, and in many cases neither the required budget, to engage with encryption, key management and HSM. On the face of it, this is a classic scenario calling for the introduction of managed services (MSP and MSSP), as was the case with network security in the past.
But existing and legacy HSM and key management solutions were not designed to be delivered as a service, let alone managed service. And, adding to the conundrum – how can one trust 3rd party to manage its most sensitive data?
Looking at it with clean state: How should managed HSM and key management look like if they were to be delivered as a managed service?
- First and foremost, the HSM should be able to be delivered as a service. And, to simplify things, the HSM and the key management should be one, integrated solution. This means technology and solution designed from the ground up to be delivered as a service.
- Management must be centralized for all functions – both for the end-users and the managed service personnel.
- To deliver scale and flexibility, the managed HSM and key management would have to be scalable (horizontally, infinitely, painlessly, cheaply). It should accommodate various deployment scenarios and different customer needs.
- To be a viable solution, the usability and TCO for both the managed service and the customer must be on-par with the standards of SaaS and public clouds.
- The solution must feature comprehensive and secure service tiering, while assuring data & customer privacy.
- But how can one assure the security and privacy of HSM and key management in a managed service? The main requirement is that the managed service, while having all the operational privileges and capabilities, will never be able to peek into the managed customer tenants. This can only be achieved by new levels of isolation between tenants, users and roles.
The Solution
So, there you have it, the blueprint of HSM and key management for this day and age, which can easily and securely be delivered as a managed service. Only, such a solution already exists, today: Fortanix DSM.
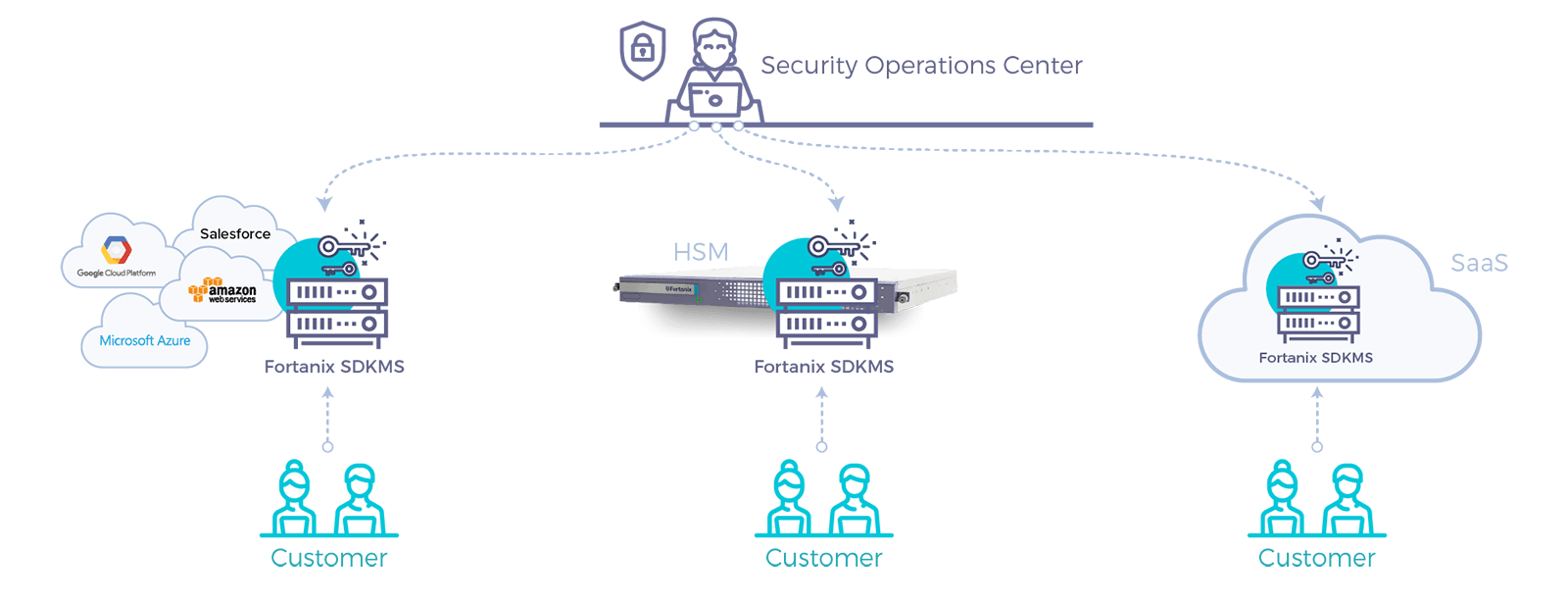
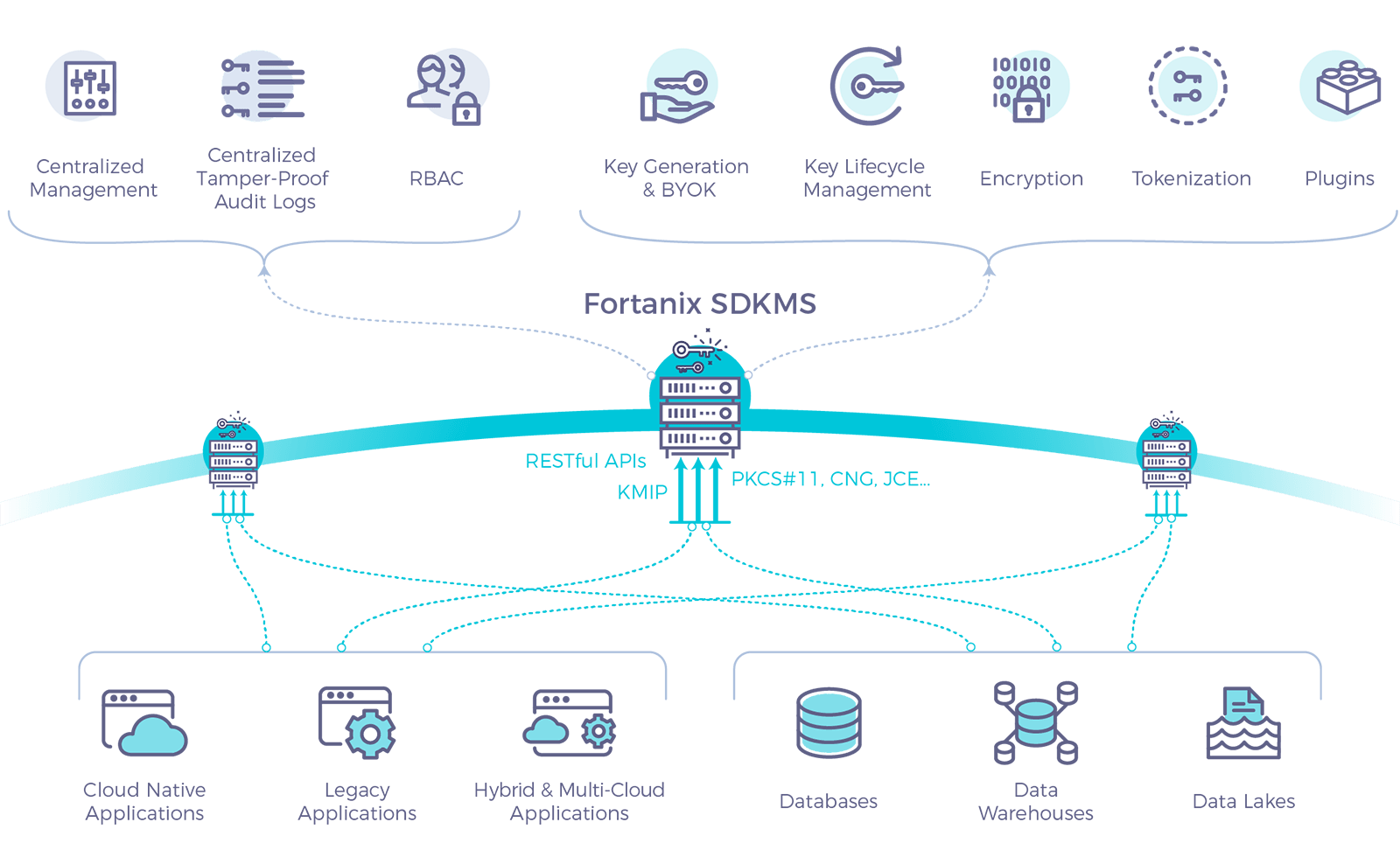
Fortanix DSM
Fortanix DSM is the world’s first commercial product using Intel SGX technology and allows customers to en-joy a cloud-scalable HSM and key management integrated solution which is also FIPS 140-2 level-3 certified:
- Offered as a multi-tenanted SaaS service, single-tenant or on-premises (self-hosted service).
- RESTful interface assures easy and seamless integration of enterprise applications.
- Scales to billions of keys per node and horizontally to an infinite number of nodes.
- Keys are automatically synchronized across the nodes of the tenant’s cluster, with strict end-to-end encryption (all TLS connections terminate inside the HSM/trust-boundary).
- High-availability, load-balancing and multi-region support are all built-in.
- Integrates with a variety of software (Hadoop, Cassandra, etc.), services (S3 CMK, etc.) and platforms (PCI, etc.).
- Supports multiple interfaces - PKCS#11, KMIP, CNG, JCE, etc. – in the same solution.
- A tamper-proof audit log is maintained for all sensitive operations/actions in Fortanix DSM.
- No access to the key material: No one, not even Fortanix or managed service provider, has access to any of the key material. Administrators, even those with root access to the servers, will not have access to Fortanix DSM
- Remote attestation of nodes for the right security posture, before nodes are enrolled into the trusted pool of servers.
- Confidentiality of all the key material, audit logs and data assets is assured, independent of the overall security of the infrastructure.

 Cite this article
Cite this article







