Cloud applications have put trust in the accuracy and security of the cloud infrastructure and associated code to ensure their classification and uprightness. But what if the infrastructure itself is compromised, or a hidden gateway in the OS/hypervisor could bargain the application’s security or control its state? So, what is the solution? Encryption? Encryption is an effective tool for data protection; however, its use is currently limited to data at rest and data in motion. When an application starts to run, its data in use is vulnerable to a variety of attacks including malicious insiders, root users, credential compromise, OS zero-day exploits, and network intruders.
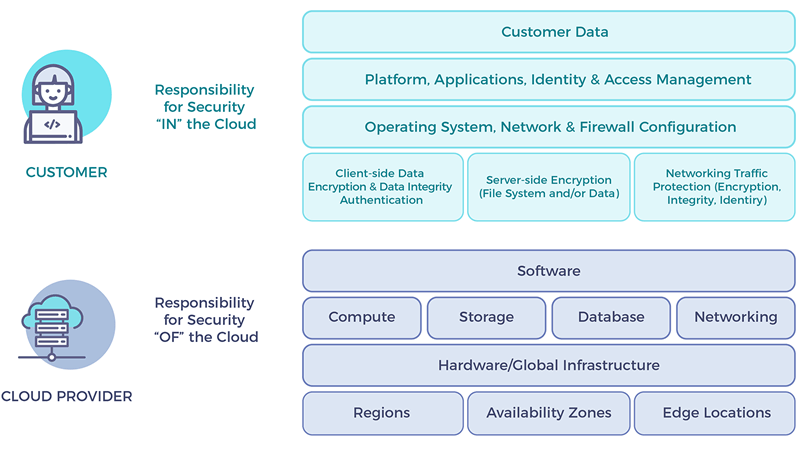
To protect applications and data at runtime, an isolated memory location called a secure enclave is used to run the application in a trusted execution environment (TEE). An enclave is protected by a hardware in the CPU that safeguards data being processed from access outside the TEE. Examples of TEE include ARM’s TrustZone, AMD’s Secure Encrypted Virtualization (SEV), and Intel’s Trusted Execution Technology (TXT) and Software Guard Extensions (SGX). Recent data breaches have raised concerns about privacy and security of sensitive data on the cloud. Confidential computing powered by secure enclaves allows a variety of enterprise use cases to run on the cloud without compromising the security. A secure enclave guarantees confidentiality, integrity, and security for the application running within it.
An enclave enables applications to process encrypted data without the possibility of exposing plain-text data to the operating system or any other running process – including any form of malicious attack. In any cloud infrastructure, the data and applications running within the enclaves become inaccessible to the cloud service provider. Enclave based computing covers a wide range of use cases.
Use Cases
-
Containerized application: Containers make applications portable, increase resource efficiency, and improve developer productivity. The enclaves provide effective isolation to mitigate security risks in a production environment. Secure enclaves protect containerized applications at runtime from host-level attacks.
-
Secure and Private Analytics on Multi-Party Data Sources: Sensitive data (PII, PHI, trade secrets, confidential information, and so on) processed by certain applications (including Hadoop, R, Python, and TensorFlow) resides within tightly secured and controlled production environments within the trust boundary. Privacy and security of the data is assured in these environments.
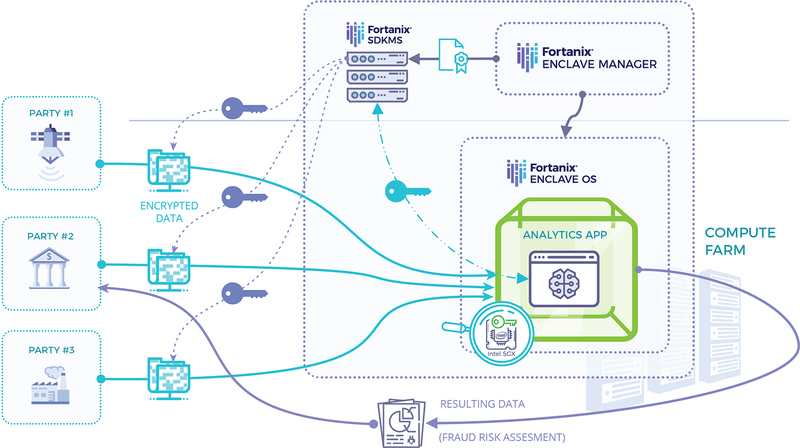
- Key Management: Encryption is an effective tool to protect data; however, the risk transfers to the encryption keys. Secure enclave based key management solution delivers unmatched security by ensuring that only authorized users have access to the keys. Fortanix DSM is the prime example of Intel SGX® based, unified key management and HSM solution.
To conclude, the secure enclave makes it difficult for hackers to unscramble delicate data without legitimate approval even with the physical access to the infrastructure. Think of enclaves as the magic boxes where you would run in your sensitive data and application without worrying about its security, integrity and confidentiality. Even if the bad guy has the root access or your infrastructure is compromised, your sensitive data remains secure. This futuristic approach to cloud security, sooner or later, will become the fundamental security building blocks for the enterprises.

 Cite this article
Cite this article






