Introduction
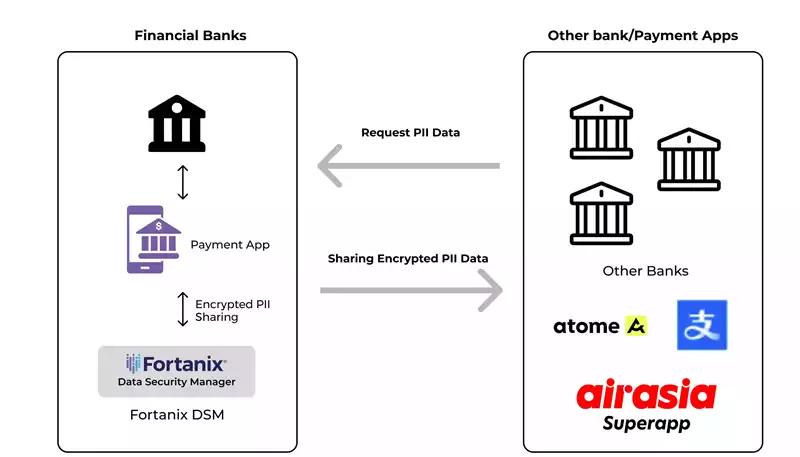
With the rise of digital payment apps such as ATOME, AliPay, and others, banks need to collaborate with these platforms to expand their services. This collaboration necessitates the protection of customer data when shared with digital payment apps, highlighting the need for advanced Hardware Security Modules (HSMs) to manage transactional data securely.
Problem
Legacy HSMs, while still widely regarded as secure due to their FIPS 140-2 Level 3 Certification, have not kept pace with modern demands. These traditional HSMs need to support an increasing number of appliances to handle the growing needs of the fast-paced payment industry.
Their outdated design relies on traditional data center controls, including Administrative Cards and Physical Pin Entry devices, an inadequate solution for today's requirements for automation and agility in financial institutions.
Additionally, to enhance the ever-demanding need, these HSMs do not provide the options for adding customized plugin.
The Fortanix Solution
Fortanix Data Security Manager (DSM) offers a next-generation HSM solution that can be deployed on-premises or in the cloud. Designed to eliminate the exponential expansion of hardware, Fortanix HSM simplifies cryptographic workflows for modern developers and is easy for security teams to manage.
Unlike other vendors, Fortanix HSM supports load balancing across clusters, preventing traffic concentration on a single node. Additionally, Fortanix provides a fully SaaS option without compromising FIPS compliance.
The novel Fortanix solution allowed a major global financial institution to modernize its payment applications, thus enabling secure data sharing with other banks, digital payment apps, and financial bodies like CIBIL for credit scores.
This modernization supports a fully connected payment industry.
Requirement In Detail
There are two approaches to fulfill this requirement: the Legacy HSM style and the Fortanix style.
1) Legacy HSM Style:
1. Bank A and Bank B exchange signed public keys (certificates).
2. Bank A signs and encrypts the payload using:
- RSA key for CEK (Content Encryption Key) encryption.
- RSA/EC key for payload signing.
3. Bank B receives the encrypted payload as a JWE.
4. Bank B decrypts the JWE and verifies integrity using AAD (Additional Authentication Data).
5. Bank B verifies the signature for authenticity.
6. Bank B accepts the data.
Downsides of Legacy HSM Style:
1. Limited payload support (>512KB).
2. Scalability issues for higher TPS needs.
3. Slow processing.
4. Requires more hardware to handle non-crypto operations. (JWE has lot of mathematical computation to be done and this is overcome in this method)
2) Fortanix Style: Fortanix's next-generation HSM offers plugins to perform the necessary steps while offloading non-crypto tasks to the client side. This client-side Java library handles non-crypto operations locally and sends only critical cryptographic tasks to Fortanix HSM for key usage, including signing and CEK encryption. This approach eliminates the downsides of legacy HSMs, enabling banks to perform more operations efficiently.
a. Customized Plugin to make the calls limited to Crypto operation to DSM.
b. Highly scalable by reducing the number of non-cryptographic calls
c. First of its kind – UI for HSM
d. Removes TPS related requirements to a bare minimum as the TPS is handed at client level.
Pre-requisites:
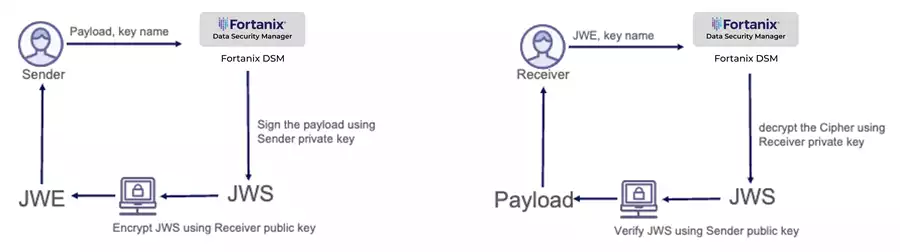
- Sender will have one Asymmetric key and Receiver will have another Asymmetric key
- Both should exchange their public keys
Flow:
- Sender will sign the payload before Encryption
- JWS will be used as a payload during JWE encryption
- Receiver receives JWE, decrypt and verify it
Algorithm to sign and encrypt the data using RSA and EC keys:
Inputs required:
- DSM JCE provider
- payload
- RSA public Key
- EC private key//RSA private key
Algorithm to decrypt and verify the JWE using RSA and EC keys:
Inputs required:
- DSM JCE provider
- JWE string
- RSA private key
- EC public key/RSA public key
Adoption Success
One of the top 10 banks in the UK successfully deployed Fortanix HSM, adopting it globally across 60+ countries. They integrated with various digital payment apps such as Alipay, FPDS, ATOME, AIRAsia, PEGA, and NRTOB, migrating from their legacy HSM infrastructure. This bank now boasts approximately 50+ global integrations using Fortanix HSM.
Conclusion
This global bank revolutionized its HSM landscape, leading the way for a connected payment industry without compromising security or increasing hardware footprint, thereby reducing costs.
The bank continues to expand its footprint across various markets, adopting additional options like DSM-Accelerator for other payment signing use cases. Fortanix HSM is FIPS 140-2 Level 3, PCI DSS certified.
Do you need to transform your HSM landscape? Learn more about Fortanix HSM or contact us to modernize your legacy HSM infrastructure with our next-generation solution.

 Cite this article
Cite this article









