Unveiling the Hidden Threats: Protect Your Business
In today's fast-paced and ever-evolving digital landscape, data security has become a top priority for organizations worldwide. With the increasing frequency of data breaches and the growing complexity of data privacy regulations, it's more important than ever for businesses to stay ahead of the curve and proactively address potential vulnerabilities in their security posture.
While the cloud gave organizations a lot of flexibility, applying data security has become increasingly complex. The self-service cloud model created silos where developers manage their own environments, but security teams lost visibility into what happens in these silos. They need visibility to ensure that data encryption is applied in line with security best practices, established policies and industry regulations. A lack of visibility is a fundamental problem: how can you protect what you cannot see?
Enter Look, Know, Further: The Game-Changing Approach to Data Security
Look, Know, Further is not merely a solution; it's a paradigm shift in data security strategy. A disruptive approach to data security that emphasizes visibility, assessment, prioritization, remediation and compliance. By focusing on these key pillars, organizations can not only identify and address their data security blind spots but also ensure compliance with regulatory requirements and industry best practices.
Look – Illuminate the Shadows into your Data Security Silos
Visibility is the first step in fortifying your defenses. Without a clear understanding of where sensitive data resides and how it is being protected, organizations are at risk of falling victim to cyberattacks and data breaches (check how to prevent breaches).
For encryption, you need to know where all keys are, and how they map to your data services. By leveraging advanced data discovery tools and technologies, businesses can gain full visibility into their data services and encryption keys across hybrid and multicloud infrastructures, eliminating blind spots and fortifying their data security posture.
Know – Assessing the Risks
Once visibility is established, the next step is assessment. It's not enough to simply know where your data is - you must also assess its security and compliance status. Manual correlation and analysis of at-risk data based on regulatory requirements and security policies is time-consuming and error prone. Users need data-driven insights to quickly and accurately prioritize the most critical security risks and develop a roadmap to adopt new algorithms and new key lifecycle policies such as periodic key rotation. This process is referred to as crypto-agility and it is critical to paving a path to new strategies, including post-quantum readiness.
Further – Remediate and Comply with Confidence
Automating corrective security actions at scale is essential for improving productivity and efficiency. Manual remediation processes are often complex and time-consuming, leading to wasted resources and increased operational costs. By automating remediation workflows and tracking the impact of proposed changes, organizations can accelerate data security improvements, get to a state of continuous compliance, with an efficient use of resources.
Embrace Key Insight
In conclusion, the Look, Know, Further strategy offers a proactive and comprehensive approach to data security. By embracing these pillars, organizations can establish a solid foundation for a secure and compliant data environment.
Enough is enough. It's time to flip the script and reclaim control. What if you could shine a light into the darkest, hidden corners of your infrastructure? What if you could uncover every hidden vulnerability, every rogue encryption key, and every compliance misstep? Imagine having the power to mitigate risks and align with regulatory standards with ease.
Key Insight is available to help modern organizations quickly improve their cryptographic security posture. Fortanix is excited to show how Key Insight can solve your crypto challenges at RSA 2024.
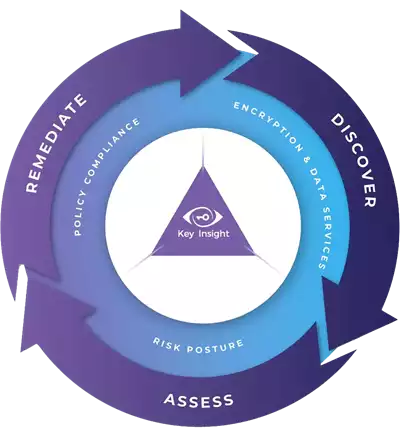
As we stand on the cusp of a new era in data security, the choice is clear. Will you remain in the shadows of data security silos, or will you step into the light with Key Insight? The future of your business depends on the decision you make today. More here

 Cite this article
Cite this article









