The Challenge: A Fragmented Security Landscape
Enterprises must manage multiple specialized solutions, including key management, hardware security modules (HSMs), data tokenization, and key inventory. The solutions often operate in silos, leading to increased complexity and cost. Such fragmented systems pose significant risks related to regulatory compliance and governance.
Challenges of Key Management Problems
- Lack of Standardization: Native encryption practices are inconsistent and lack standardized methodologies.
- Governance Issues: The absence of governance frameworks results in poor oversight and management of keys.
Hardware Security Module (HSM) Inefficiencies
- Underutilization: HSMs are frequently underutilized as the legacy HSMs do not have load balancer to ensure traffic is routed between multiple devices which makes one node taking traffic while others are underutilized, leading to operational inefficiencies.
- Complex Management: Integrating and maintaining HSMs is complex and resource intensive.
Data Tokenization Troubles
- Home-Grown Solutions: Many organizations rely on proprietary tokenization solutions to temporarily solve the requirements; however, these solutions may not meet industry standards.
- Inadequate Masking: Existing masking techniques are often insufficient as they do not use certified Random number generators.
- Random Number Generation (RNG): The lack of certified RNGs compromises tokenization strength.
Key Inventory Issues
- Compliance Risks: Organizations struggle to meet regulatory requirements, increasing compliance risks. This is because the Key lifecycle governance requires the Keys to be tracked; however, there are not many tools available to cover the entire Tech Stack
- Key Management: Identifying and managing keys across the estate is challenging. Many organizations opt for manual inventory, which is prone to human errors, and no solution can help provide a single pane of Key Inventory.
Overall Security Landscape
With all the above challenges listed, Enterprises are usually ending up with the below:
- High Maintenance Costs: The fragmented nature of existing solutions results in high maintenance costs.
- Governance Gaps: Persistent lack of governance leads to ineffective security management.
- Disjointed Infrastructure: Isolated crypto solutions create a disjointed security infrastructure.
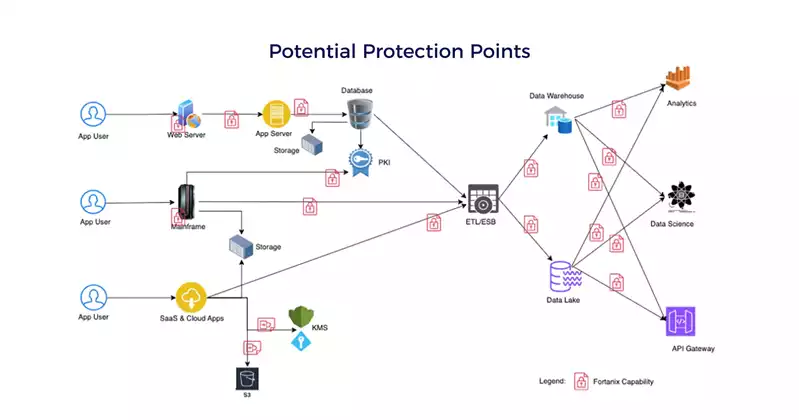
Fortanix: A Unified Solution to Data Security Challenges
Fortanix addresses these issues with an advanced approach to data security, offering a comprehensive solution that simplifies key management, optimizes HSM utilization, enhances data tokenization techniques, and ensures comprehensive key lifecycle governance.
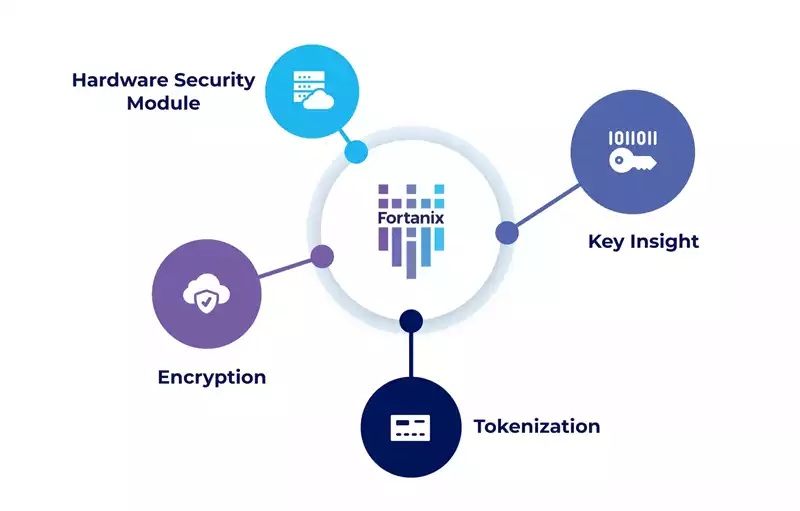
Fortanix Central Key Management System
Fortanix's key management system integrates with various use cases, including Key Management Interoperability Protocol (KMIP) for storage and Transparent Data Encryption (TDE) for databases, facilitating application-level encryption and providing a robust framework for data security.
With a lot of new technologies being consumed and the wider tech stack that is in existence, Fortanix has a lot of third-party integrations that can be leveraged to make it one of the most powerful key management systems in the industry.
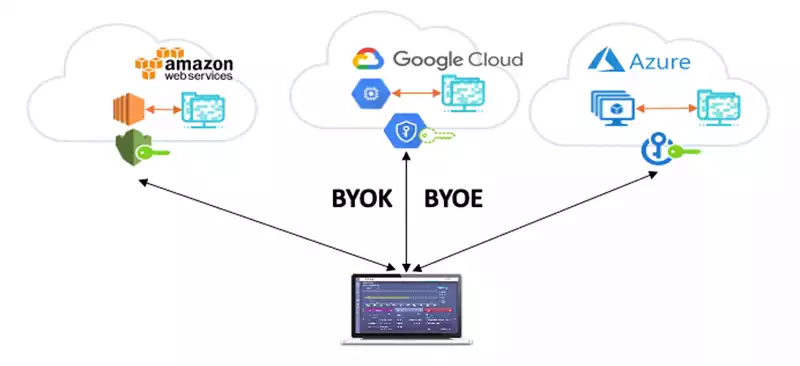
Fortanix Cloud Integration
Fortanix provides seamless integration with major Cloud Service Providers (CSPs) for "Bring Your Own Key" (BYOK) and "Bring Your Own Encryption" (BYOE) strategies. This integration supports compliance with regulations such as SG Monetary Authority (SG MAS), Hongkong Monetary Authority (HKMA), and India Data Protection, ensuring secure data management in the cloud.
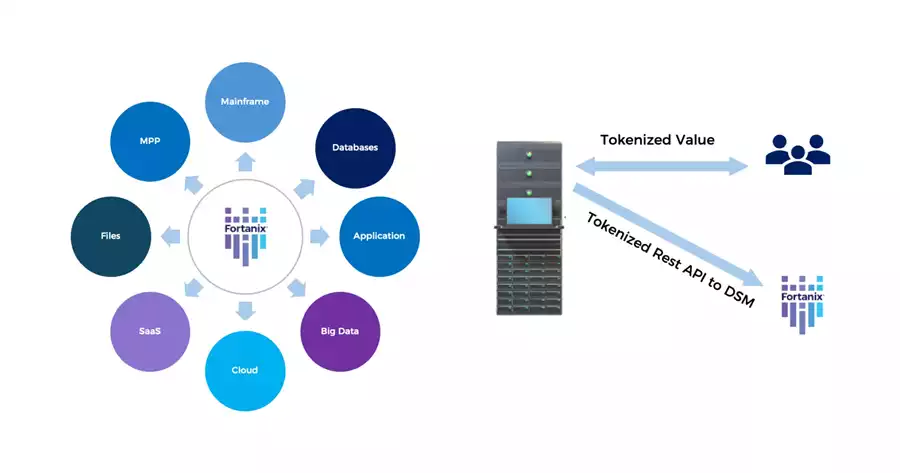
Fortanix Data Tokenization
Fortanix's vaultless tokenization platform meets increasing regulatory demands for tokenizing Personally Identifiable Information (PII) and Payment Card Industry (PCI) data. The scalable, agentless solution is compatible with various tech stacks, supporting environments like Hadoop, databases, cloud, big data, and mainframes. Featuring a FIPS-certified RNG, it ensures compliance and offers predefined templates and customizable policies.
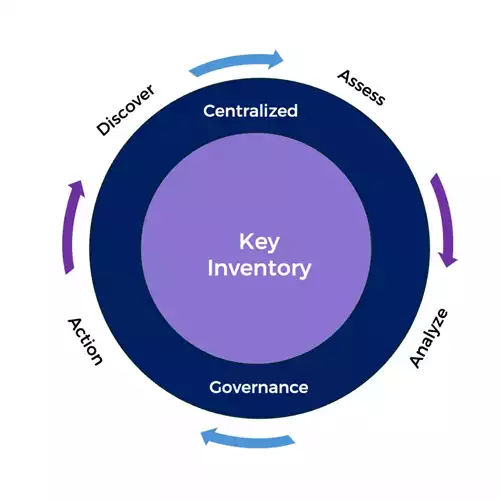
Fortanix Key Insight
Fortanix Key Insight provides a unified view of cryptographic keys across cloud and on-premises environments. It helps organizations adhere to industry standards (e.g., NIST, PCI DSS) by identifying key generation dates, sources, and rotation schedules. This centralized inventory supports PCI v4.0 compliance and offers on-premises scanning for a comprehensive cryptographic key posture.
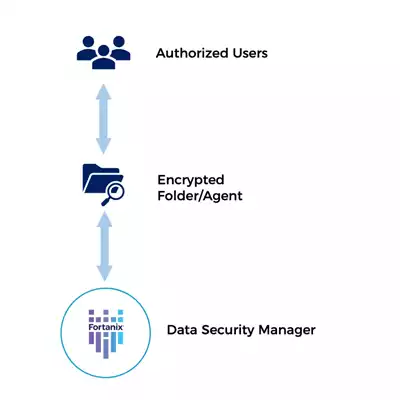
Fortanix File System Encryption
While application-level encryption is preferred, certain use cases necessitate file and folder encryption. Fortanix's solution supports major Linux and Windows server OSs, offering encryption for scenarios where application-level options are unavailable. It reduces backup storage costs and provides granular policies configurable down to the file level.
Fortanix Pretty Good Privacy (PGP) Use Case
Meeting FIPS 140-2 Level 3 standards, Fortanix PGP enhances file-sharing operations, serving as a secure replacement for GnuPG and other PGP tools. We have an active integration with Sequoia PGP making the entire PGP use case move from standalone to the central key management system.
Conclusion
Fortanix offers a unified solution that reduces costs and complexity while ensuring regulatory compliance and robust governance. This holistic approach transforms the security landscape for organizations, providing a secure and efficient data security framework.

 Cite this article
Cite this article









