Introduction
This week, NIST released [source] three of the long-awaited post-quantum cryptography (PQC) standards. With these algorithms, organizations can future-proof their most sensitive data against the looming threat of quantum computers capable of breaking most of the encryption we rely on today.
What is PQC, and why the urgency?
In today’s perimeter-less world, encryption is the last line of defense in preventing data exposure. For many data privacy and security regulations, encryption is a hard requirement or a fast way to ensure you protect the regulated data properly.
Quantum computers operate differently from the digital computers we have today. They are especially good at solving select, complex mathematical problems. Unfortunately, this includes the math we rely on in current asymmetric cryptography.
Post-quantum cryptography uses different algorithm approaches that can be performed by current computers but are very difficult to break using quantum computers' attack vectors.
Even though quantum computers with the capacity to break current algorithms don’t exist, hackers already operate under a “harvest now, decrypt later” strategy.
Since information such as Intellectual Property (IP), angel investors, or state secrets will still be sensitive and hold their value for decades or indefinitely, you must prepare now. By understanding the imminent impact and taking proactive steps today toward quantum readiness, you ensure continuity and security in the quantum age.
How to prepare for PQC in your organization
Transitioning your cryptographic infrastructure to PQC (Post Quantum Cryptography) is not trivial. Still, with proper planning and the proper tools to execute the plans, the journey is well-defined and has minimal operational impact. Zooming out on the overall process, there are four stages:
- Inventory: You need detailed visibility into your cryptographic security posture. This means knowing where all encryption keys are, which services use them, and what sensitive data these services process.
- Assessment: Evaluate your most significant data exposure risks. What data is most sensitive, and how well is it encrypted today?
- Planning: Does the service support new PQC libraries? What is the vendor’s timeline, or can you migrate the service?
- Test and Execute: ensure the new scenario does not create service disruptions, and schedule maintenance windows to minimize disruption.
Choose Fortanix as your ultimate travel partner!
The Fortanix platform is purpose-built for agile data security and simplifying your cryptographic operations. Fortanix provides solutions for all critical steps in your post-quantum readiness journey.
Fortanix Key Insight discovers encryption keys and data services in your on-premises and multicloud environments. It reveals details about the encryption keys, such as algorithm strengths, rotation frequency, and how your data services use them.
Key Insight immediately shows your most significant risks, and which keys are quantum vulnerable. This makes Key Insight an invaluable tool to plan and prioritize post-quantum cryptography.
Cryptographic agility is essential for transitioning to a strong and resilient data security posture. The Fortanix platform provides a Key Management System (KMS) solution with integrated Hardware Security Modules (HSMs), helping organizations simplify and regain control of their cryptographic operations across hybrid multicloud environments. Organizations can then transition to new cryptographic standards smoothly and with efficient resource use.
Fortanix has always been at the forefront of security technology. The company was an inaugural member of the Confidential Computing Consortium, alongside companies like Google, Intel, and Microsoft, which technology powers the platform.
Fortanix also immediately recognized the advantages of using the Rust programming language and built the Data Security Manager platform as early as the 1.0 release of Rust. Rust is widely recognized for producing highly secure code, completely sidestepping the most significant cause of security bugs by enforcing memory safety at the language level without sacrificing performance.
Our approach to PQC is no different. We provided early support for Google Client-Side Encryption to enhance the privacy and confidentiality of Google Workspace customers. At Google Next, Fortanix announced its implementation for hybrid post-quantum key exchange as part of the cipher suite for TLS 1.3. Now that the NIST standards are released, Fortanix engineers are primed to implement PQC across our internal systems and workflows, for example, by using LMS for code signing.
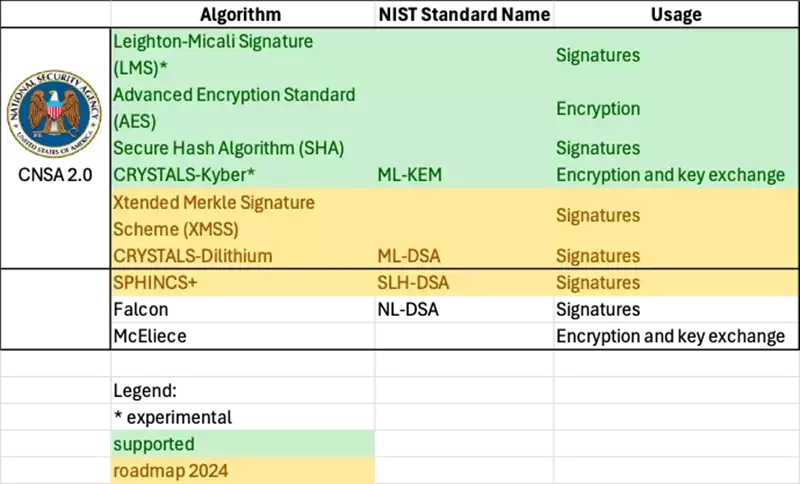
Fortanix DSM already supports LMS signatures and ML-KEM, while ML-DSA support is already scheduled for September. With the newly released NIST standards, Fortanix will implement support for XMSS and SLH-DSA shortly after that.
The table below shows a list of NSA-recommended quantum-resistant algorithms, as recommended by the NSA, how they are called in the NIST standard, and their use case.
If you are ready to start your journey, contact us to discuss how Fortanix can help, or take a risk-free scan of your cryptographic security posture with a free Key Insight trial.

 Cite this article
Cite this article









