The Future is Quantum, and It's Closer Than You Think
In cutting-edge technology, few concepts hold as much promise and potential disruption as quantum computing. The idea of harnessing the unique properties of quantum mechanics to solve complex problems at unimaginable speeds has long fascinated researchers and tech enthusiasts alike. But what was once a theoretical dream is now hurtling toward reality, and it's time for organizations to prepare for the darker side of the quantum-coin: your critical data that was encrypted for safekeeping, will soon—just a couple of years—be laid bare by quantum computing’s code-cracking abilities.
Introducing "Preparing for Post-Quantum Cryptography: Mapping your Organization’s Data Security Strategy to the Effects of Quantum Computing" a whitepaper by Dr. Richard Searle, Vice President of Confidential Computing at Fortanix. In this new whitepaper, Dr. Searle dives deep into the world of quantum computing, its looming threats to modern post quantum data security, and the crucial steps organizations must take to safeguard their sensitive information in the post-quantum era.
The Post Quantum Revolution Unveiled
Our current digital landscape relies heavily on classical computers, with binary bits processing information as 0s and 1s. Quantum computers, however, introduce a paradigm shift. These machines leverage quantum bits or qubits, which exist in multiple states simultaneously, thanks to superposition and entanglement. This intrinsic parallelism promises computational capabilities to outpace even the most advanced current supercomputers.
Related Read: Should I be concerned about Quantum Computing
As exciting as this sounds, quantum computing carries a double-edged sword. While it holds immense potential for solving complex problems, it also threatens the very foundation of data security as we know it. The whitepaper delves into post quantum algorithms that could potentially crack encryption methods that have safeguarded our data for decades, like the RSA algorithm and Elliptic Curve Cryptography.
From Theory to Reality: The Looming Threat
In 2019, Google claimed "quantum supremacy" by successfully applying a 54-qubit quantum processor to solve a problem in 200 seconds that would take classical supercomputers an estimated 10,000 years. This monumental leap marked the beginning of a new era, with quantum computers demonstrating their process.
Moreover, companies like IBM are rapidly advancing quantum computing technology, with processors boasting thousands of qubits. This quantum progress, while revolutionary, opens Pandora's box of security risks. Sensitive data that classical encryption methods have long shielded could now be vulnerable to quantum attacks.
The Post-Quantum Dilemma: When and How to Act
The whitepaper doesn't just highlight the impending threats; it provides a roadmap for action. Dr. Searle outlines three crucial steps to prepare for the post-quantum era:
- Undertake Discovery: Understand your existing data security landscape. Identify where cryptographic keys are used, their vulnerabilities, and the potential impact of a breach. Prioritize data according to risk levels and plan for the transition to post-quantum cryptography.
- Gain Control of Encryption: Establish robust access controls for key management. Ensure a seamless transition to new post quantum encryption algorithms while maintaining visibility and control over cryptographic operations.
- Build "Crypto-Agility" into your operations: Embrace crypto-agility by adopting a unified security platform. Implement and operationalize new cryptographic standards while keeping data security intact.
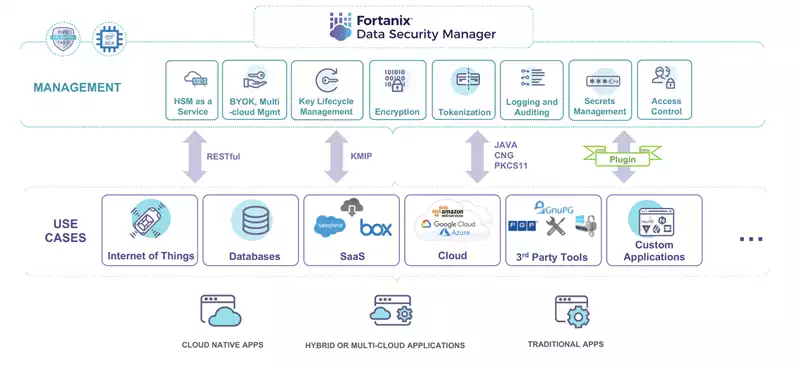
Enter Fortanix: Your Quantum-Ready Partner
Fortanix is a pioneering force in confidential computing and data security technology. The Fortanix Data Security Manager platform (DSM) is a data-centric security solution that empowers organizations to transition seamlessly to the post-quantum cryptography era. With Fortanix, you can adopt new cryptographic algorithms, safeguard your sensitive data, and maintain control over all encryption operations, while ensuring compliance with evolving data protection requirements.
As the post-quantum era inches closer, the need for comprehensive data security strategies is more pressing than ever. Dr. Searle's whitepaper is a beacon of knowledge, with practical insights into the complex landscape of quantum threats and solutions. Don't wait until it's too late; prepare your organization for today's quantum revolution.
To embark on your post-quantum journey and learn how Fortanix can fortify your data security, download the whitepaper "Preparing for Post-Quantum Cryptography" by Dr. Richard Searle.
Disclaimer: This blog post summarizes the whitepaper "Preparing for Post-Quantum Cryptography." For in-depth insights, recommendations, and expert analysis, we encourage you to read the full whitepaper authored by Dr. Richard Searle.

 Cite this article
Cite this article









