The Big Hack demonstrates that the cyber warfare has moved from realm of the software to realm of the hardware. Software-based security, such as anti-malware, firewall, user behavior analysis, network flow analysis, etc. are ineffective in the face of such sophisticated attacks.
Hardware implants, in the form of tiny microchips on the motherboard, were used to attack the operating system and then spy on and exfiltrate private data. Implants are even worse than interdiction, a technique used by US spy agencies as reported by Snowden.
Interdiction is used to alter and manipulate hardware in transit to insert hardware-based attacks. Implants occur at the time of manufacturing, which makes detection extremely difficult.
Attacks like The Big Hack have huge security implications. Even FIPS 140-2 Level 3 and Level 4 devices, such as Hardware Security Modules (HSM), may get impacted by this because the attack happens even before the tamper-response and tamper-detection modules are inserted. The possibility of hardware implants in servers in the public cloud can erode trust among customers who don’t feel like they have any control over the supply-chain process.
No software-only security solution can protect against these hardware manipulations.
Only hardware can fight and defeat hardware. Fortanix Runtime Encryption® decouples the security of an application from the security of the infrastructure. It assumes that the infrastructure is compromised, as was the case in the Big Hack. However, applications running with Runtime Encryption® remain protected wherever they run.
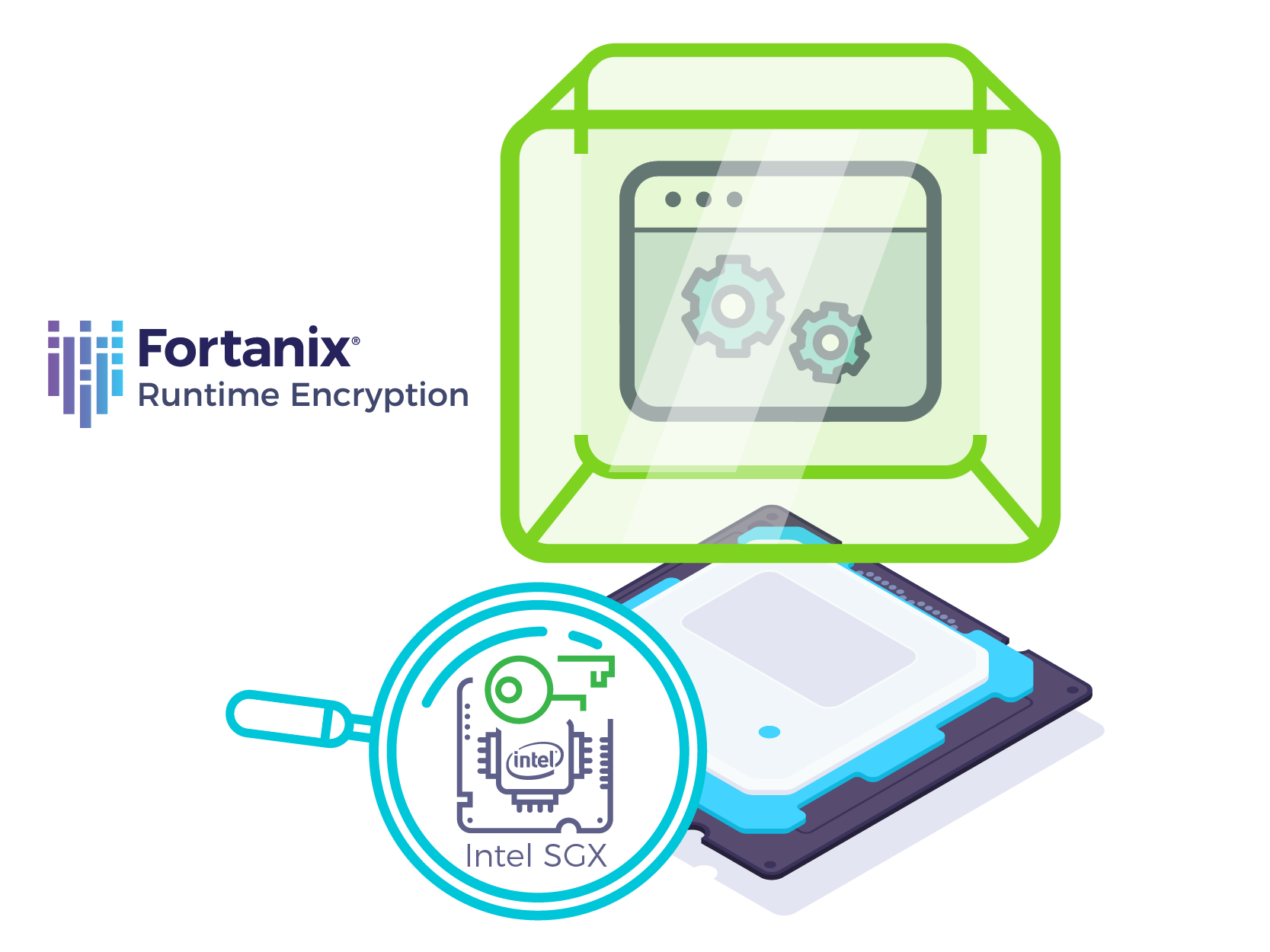
Runtime Encryption® uses secure enclave technology such as Intel® SGX in the processor to ensure that data always remains encrypted, even when in use. Only authorized code can be loaded into enclaves, and it can’t be modified once loaded.
This ensures the confidentiality as well as the integrity of data and code. Data stored at rest as well as data in motion are also encrypted using keys available only inside the enclave. This ensures that no data is visible in plain text outside the SGX enclave, ever. You can’t hack what you can’t see!
Also read: How SolarWinds Busted Up Our Assumptions About Code Signing
Applications built on Fortanix Runtime Encryption®, such as Fortanix DSM, and Equinix SmartKey, powered by Fortanix, are protected from The Big Hack. To learn more about Fortanix Runtime Encryption®, reach out to us at info@fortanix.com.

 Cite this article
Cite this article







