Several customers have reached out to Fortanix for feedback on the newly found CPU vulnerabilities.
When we started Fortanix in 2016 and started talking about protecting data in use, the initial reaction from customers was that the approach was visionary. However, we had to spend a lot of time explaining why the approach was necessary and why their existing anti-virus and network firewalls solutions were not enough.
The recent “Meltdown” and “Spectre” vulnerabilities found in CPU are notable for many reasons and provide good lessons to everyone.
Importance of hardware based security
The Meltdown and Spectre vulnerabilities exist in the CPU hardware and are a type of sophisticated attack known as a “side channel attack”. The vulnerabilities were discovered by hardware security experts.
Know more: About Side Channels and Runtime Encryption® with Intel® SGX
The discovery of these vulnerabilities is a reminder that reliably evaluating the security of modern infrastructure requires a solid understanding of the hardware supporting that infrastructure. Hundreds of billions of dollars have been spent on software-only malware detection, virus scanners, and firewalls that did not detect any of these vulnerabilities.
Software security tools will never be able to provide protection if the foundational hardware is insecure. End-to-end security is not just a buzzword, it is a frame of mind that must be embraced to achieve a high level of security.
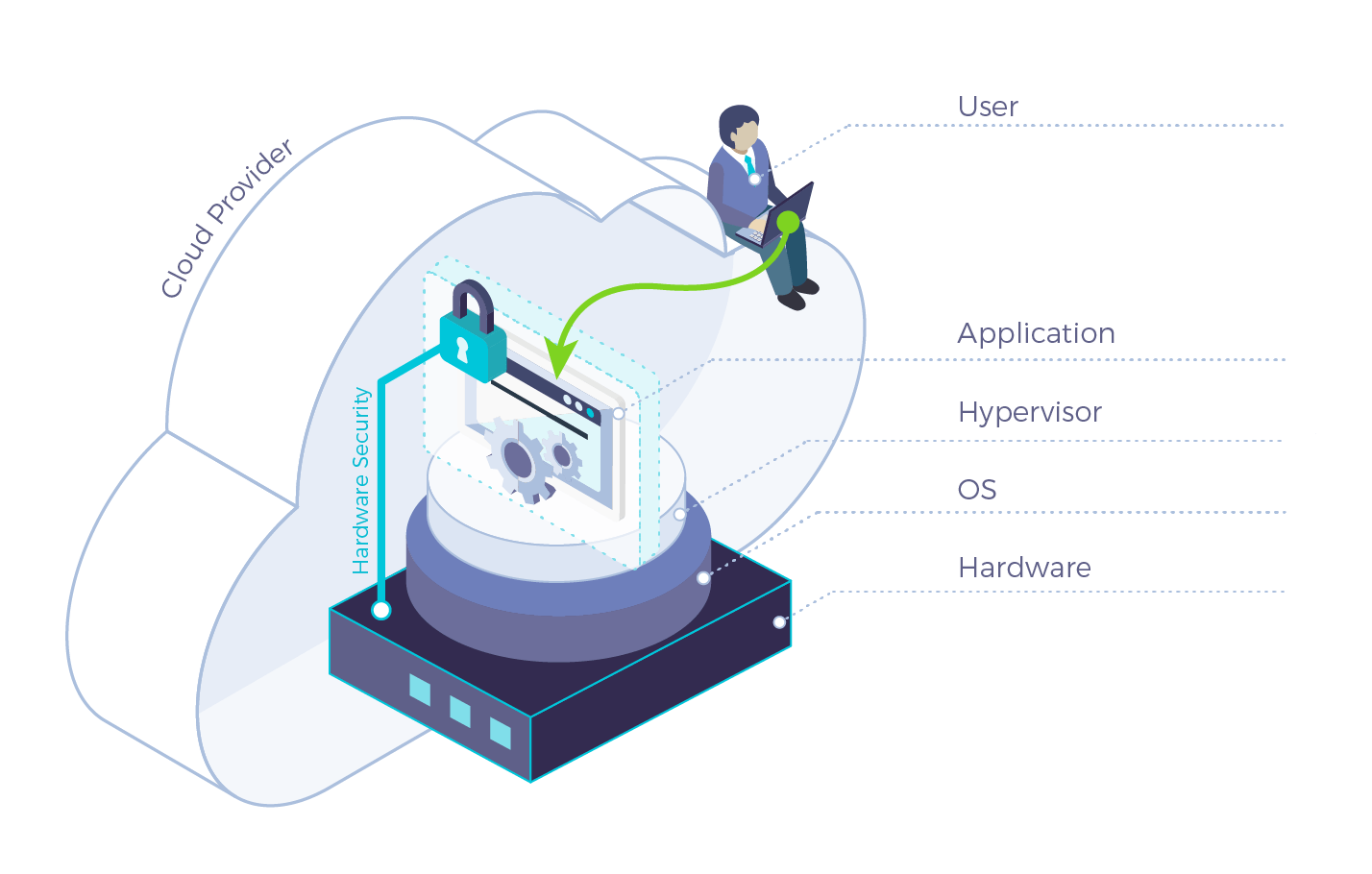
Fortanix has been saying all along that operating systems, hypervisors, and software security tools are not enough to keep applications secure. A new approach is needed that provides security from the hardware to the cloud!
Encrypting everywhere including Runtime
The Meltdown and Spectre vulnerabilities allow unauthorized reads of data of running programs. This is a reminder that encryption remains the most effective tool to protect data.
Encrypted data is unintelligible even when disclosed. The mathematical nature of encryption trusts nothing. Mathematics is easy to analyze and hard to defeat. Encryption can most readily be deployed to secure data at rest.
Tools like PGP and BitLocker ensure that if someone steals your hard-drive, the data remains protected. Similarly, encryption can be used to secure data in motion. TLS ensures that your communication with your favorite e-commerce website is protected from disclosure or modification.
Until recently, data in use was the window where data remained exposed, due to a lack of solutions for encryption of data in use. Fortanix has developed technology for protecting data in use, or as we call it, protecting data at runtime.
Fortanix’s Runtime Encryption® solutions keep data encrypted and secure even when held in an application’s in-memory data structures or when actively being used for computation. The Meltdown and Spectre vulnerabilities are a reminder that data in memory can be vulnerable despite the security claims of modern system software.
Fortanix was founded on the principle of providing deterministic security using Intel® SGX secure enclaves. Our mission is more important than ever in light of the recent findings.

 Cite this article
Cite this article







