On the final day of September, President Biden proclaimed October 2022 to be “Cybersecurity Awareness Month” and called upon “the people, businesses, and institutions of the United States to recognize the importance of cybersecurity, to take action to better protect yourselves against cyber threats, and to observe Cybersecurity Awareness Month in support of our national security and resilience.”
While the activities of malevolent spirits and nefarious characters are usually associated with Hallowe’en, at the end of October, cyber threat actors pursue their illicit objectives throughout every hour, of every day (and night), of every month of the year.
Cybersecurity, to defend against modern cyber threats, demands a constant state of vigilance and protection is upheld for our valued data and applications.
The persistence of cyber threat actors, coupled with an emerging context of great power competition and coordinated nation-state operations in the cyber domain, places a societal responsibility for cybersecurity on every individual, organization, and government agency.
Fortanix is recognized as a pioneer, and the world-leader, in the application of Confidential Computing technology to protect data and software applications throughout the entire data lifecycle.
The enhanced protection provided by Confidential Computing now renders it a frontline tool to support the President’s aspiration that US citizens, businesses, and institutions defend themselves against criminal and state-derived cyber threats.
In this extended two-part blog to mark Cyber Security Awareness Month, I will look at how Confidential Computing is being applied by Fortanix to protect customer workloads featuring a broad range of different data and application types.
What to Expect?
In the first part of the blog, I will look at how the application of Confidential Computing by Fortanix enables our customers to demonstrate compliance with their internal policies and applicable data protection legislation.
With global data flows forming the lifeblood of today’s, digital, economy, how can large and small enterprises extract value from data, while respecting the privacy and confidentiality requirements imposed by different legal frameworks? How can compliance with regulatory controls be demonstrated and audited as an intrinsic feature of enhanced cybersecurity?
The second part of the blog, to be published later in October, will move beyond the implementation of cybersecurity with Confidential Computing to assess how an improved security posture can serve as a value driver for organizations in the emerging context of Web 3.0.
I will address the question of whether cybersecurity should be viewed as a strategic investment or maintained as an operational expense.
I will also consider how Confidential Computing can be leveraged by customers to enable new, and innovative, business models premised upon secure collaboration between parties and the ability to adapt to potential changes in the regulatory regime.
What Really is Cybersecurity?
Let’s begin by defining what we mean when we refer to “cybersecurity.” A Google search on the term yields a myriad of variations on a theme.
We will keep it simple by focusing on the leading dictionary definition of cybersecurity as “the state of being protected against the criminal or unauthorized use of electronic data, or the measures taken to achieve this.”
At Fortanix we reflect this in a data-first security approach, where security is considered as a property of the data and not a characteristic of the infrastructure used to process the data. Why do we take this approach?
Well, the evidence is clear: computer networks and their access perimeters are no longer safe and should be regarded, by default, as untrustworthy.
This assumption applies whether data is being processed on-premises, in a firewalled datacenter, or in the cloud, using third-party infrastructure.
In April, the US Cybersecurity and Infrastructure Security Agency (CISA), in cooperation with international partner agencies, issued Alert AA22-110A.
The Alert, published in response to the Russian invasion of Ukraine, warned of the risks posed by a host of cyber threat actors referred to by a host of different pseudonyms that reads like the character list for a Halloween party.
CISA and others identify the entities listed in Alert AA22-110A as the source of cyberattacks perpetrated against critical infrastructure and high-profile target organizations across the globe.
As I commented in February, at the beginning of hostilities, the war in Ukraine, coupled with the hostile background activity of other states, places everyone on the front-line when it comes to cybersecurity.
Cyber criminals and the nation states that are obscured behind a veil of criminal activity pose a clear and present risk to our personal data, intellectual property, cyber-physical systems, and financial security.
However, contemporary cyber threats are not always external to an organization. As the recent case of two US citizens charged with offering protected healthcare information (PHI) of military personnel to the Russian state [source] illustrates, insiders with privileged access to data also pose an inherent cybersecurity risk.
In the cited case, the healthcare information offered to a foreign government is subject to regulation under the privacy and security rules imposed by the US Healthcare Insurance Portability and Accountability Act of 1996 (HIPAA).
Such information is of high value to cyber threat actors as the sensitive data within private medical records can be used for extortion and coercion of the individual to whom it pertains.
No wonder Statista reported that in 2019 the global cost per stolen healthcare record was $429 [source], more than twice the equivalent cost of stolen financial records, at $210.
But if the organizational perimeter is permeable and we can’t trust those responsible for the control and use of our data, what can be done to enhance our security posture and address the sophisticated threat vectors and well financed adversaries we now face? All is not lost.
The first step is to recognize the scale of the threat, the implications of a data breach in terms of both punitive financial penalties and reputational damage, and accept, a priority, that security needs to be deployed at the data level: at rest – where it is stored, in transit – where data is communicated, and in use – where data is processed.
The second step is to establish control. It is becoming increasingly important to be able to audit and demonstrate the use of data, to ensure compliance with legal obligations that may form a composite framework of regulatory obligations where each instrument applies in a different respect.
Regulations applicable to the data processed by an organization may also originate from outside the local jurisdiction, adding complexity in the control of data use.
For example, the EU General Data Protection Regulation (GDPR) is extra-territorial in its scope as it applies to the protection of “data subjects” constituting “any person in the EU, including citizens, residents, and even, perhaps, visitors.” While GDPR imposes fines for an applicable data breach of €20 million, or 4% of worldwide annual turnover – whichever is larger, this may not be the extent of any financial risk derived from weak cybersecurity if other statutory obligations apply to the affected data.
In today’s complex risk landscape, characterized by pervasive threats, the privacy enhancing technology of Confidential Computing is positioned to reduce risk exposure and support regulatory compliance, providing auditable proof of the cybersecurity measures implemented to protect data and sensitive applications.
Confidential Computing involves isolating data and applications inside a hardware-based trusted execution environment (TEE). The TEE comprises a region of protected memory that is encrypted to prevent access to the data processed inside it.
Although there are different technical approaches to creating a TEE, depending on the underlying hardware platform, the isolation provided to deployed workloads restricts the ability of an attacker to access data from outside the TEE boundary.
Hence system-level components, including the host operating system and virtual machine manager, privileged users, applications using the same hardware platform, resident malware, and undetected network intruders, are all denied access to the contents of the TEE.
With compatible hardware now available, at scale, from OEM vendors and public cloud service providers, Confidential Computing is being used today, in production, by Fortanix and well over 100 customers to protect workloads featuring artificial intelligence and machine learning (AI/ML), relational database applications, web services, and blockchain applications – to name only a few examples.
Crucially, the provisioning of a TEE requires “attestation” of the underlying hardware platform to verify the integrity of the platform and the protected memory region. Attestation provides a means of assuring that the deployed workload has not been tampered with and is secured in use at runtime.
Unique cryptographic signatures, generated from the hardware-based identity of the CPU used for computation, allow different applications to verify that each is secure before interaction. Attestation reports can also be integrated with system logs to assert protection of the processed data, in line with any policy relating to its use.
Thus, attestation, provides a solid foundation for the evaluation of compliance with data protection regulations and an auditable record of data and application use.
The Fortanix Advantage
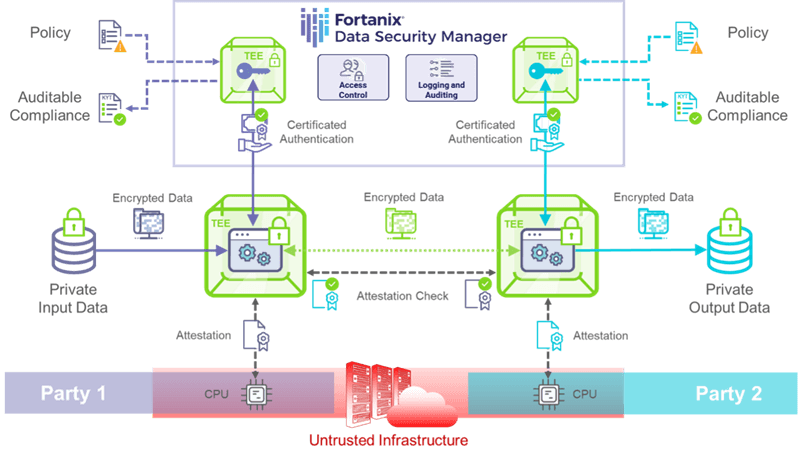
Fortanix is uniquely positioned in the Confidential Computing market, as we first implemented the technology to build Fortanix Data Security Manager™ – a cloud native, fully featured, and flexible hardware-security module (HSM) replacement, available as Software-as-a-Service (SaaS) with up to FIPS 140-2 Level 3 certification.
This product provides state-of-the-art security for the cryptographic keys that are essential to the security of data at rest and in transit. Users can configure fine-grained policy controls to restrict access to data by human and software-based users, with quorum approval support preventing misuse of keys by any one user.
Fortanix’ Confidential Computing technology allows for the generation of a unique certificate at runtime, which is bound to an application following attestation of the TEE. This certificate can subsequently be used for authentication of the application to Fortanix Data Security Manager to access stored secrets.
Using this feature, encrypted data can be ingested by an application secured by Confidential Computing with data only being decrypted inside the TEE. Decryption follows verification of the application identity by the key management service, using attestation as the root-of-trust for certificated authentication.
Data is protected in use during computation inside the TEE and application outputs can be encrypted using a key stored in Fortanix Data Security Manager. The encrypted output data can be distributed to a selected endpoint along with a “Know Your Transaction” (KYT) report that documents the attestation, authentication, and cryptographic operations associated with the entire end-to-end workflow.
Within complex application pipelines, attestation checks between TEEs can effectively establish a secure network within the network to maintain security at the data level. In this way, Confidential Computing can guard against unseen network intrusion, unauthorized access by privileged users, and uncontrolled use and proliferation of data.
This applies equally to deployments on compatible public cloud infrastructure and on-premises hardware installations. Mutually distrusting parties can now collaborate using sensitive data and applications that neither wants exposed to the other, even on an untrusted infrastructure, such as the public cloud.
Confidential Computing represents, therefore, an enabling technology for efficient data collaboration in vital areas of activity including medical and pharmaceutical research, financial crime prevention, and the development of artificial intelligence (AI) systems that require vast amounts of data to train new computational models.
All of this can be achieved by Fortanix customers within a Zero-Trust Architecture (ZTA), consistent with both the guidance provided in NIST Special Publication 800-207 [source] and the directives of Executive Order 14028, issued by President Biden in May 2021 [source].
The illustration below shows how Confidential Computing encapsulates sensitive workloads to protect the data and applications of independent parties and support auditable compliance of workloads under different policy and regulatory frameworks:
And so, we return, full circle, to the goals of Cybersecurity Awareness Week. The aims of this initiative are clear – to encourage action that will “better protect” the United States against the scourge of cyberattacks and cybercrime, an imperative that holds true wherever you are in the world.
Cybersecurity is about reducing exposure to risk and verifying that the target of cyber threat actors – our precious data – is protected with sufficient safeguards to meet the legal obligations and rules governing data protection that are enforced by regulatory agencies on our behalf.
The data-first approach to security supported by Fortanix products, using Confidential Computing, provides full-lifecycle protection for our customers’ data and critical applications, and straightforward auditability of their compliance with internal and regulatory policy requirements.
In this opening part of my blog, I have placed an emphasis of the application of Confidential Computing to a familiar environment of centralized data owners, managed datacenter and cloud-based infrastructure, and regulatory oversight.
In the next part, I will move to consider how Confidential Computing provides the foundation for tomorrow’s data environment, where decentralization, unregulated cryptocurrency, and individual control over data reflect a new normal.
In the meantime, to find out more about how Fortanix can support you on the journey to improved cybersecurity and auditable compliance.

 Cite this article
Cite this article