The reports of hackers getting into the network and hiding unspotted are on the rise. Be it the GoDaddy password breach or the very recent BDO Unibank hack— a lot of sensitive information is at stake impacting several users.
Thus far, companies have found a certain sense of data security via database encryption and encrypted communication (TLS) mechanisms. Despite these measures taken by IT, data breaches continue to make headlines.
So how do hackers breach sensitive data despite be encrypted? The answer is runtime. The application running on a host with all the data pulled from a database or over the network has every byte of data decrypted in the memory for the CPU to compute.
Along with the PII, the proprietary algorithms, cryptographic keys all stand exposed during runtime, and I will show you how.
Anybody with access to your host, be it an employee, service provider, hacker, or even malware can dump the content of this unencrypted memory region using open-source tools and get access to all the information meant to be protected.
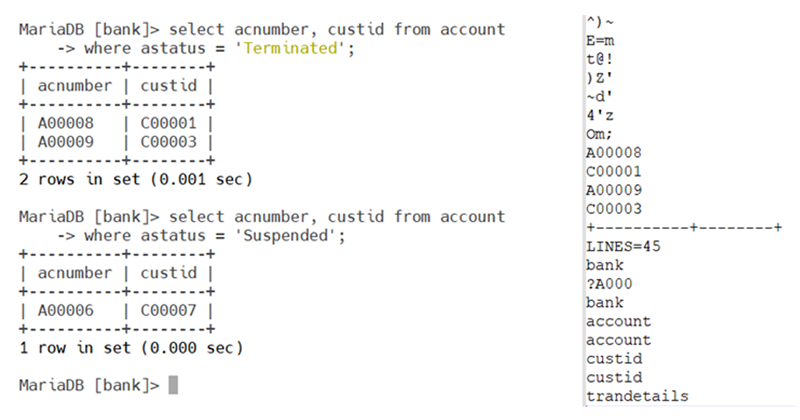
I can demonstrate the same by running a SQL query against my encrypted database, and simultaneously dumping the contents of this unprotected memory region.
In figure LH.1, you find a SQL query against an account table from a synthetic bank database. Figure RH.1, which is a snippet of the memory dump exposes the sensitive information which includes the secret key used to decrypt the data, along with other information of the account holder.
Are there any solutions to these challenges?
While preventing every breach or controlling every bad actor is a tough feat to achieve—we can certainly limit the damage by protecting the data.
Homomorphic encryption allows computation on encrypted data as it was unencrypted. But this scheme of cryptographic computation remains too slow to run complex functions and is not completely ready yet for enterprise adoption.
Confidential Computing is a promising and enterprise-grade solution that is available today. The confidential computing infrastructure is available across the regions from the major cloud vendors.
And we have Fortanix further easing the adoption of confidential computing for enterprises that provide solutions to manage the entire lifecycle of this confidential computing infrastructure and services to ‘lift & shift’ and orchestrate the applications.
The security policies enforced by Fortanix solutions include identity verification, data access control, and attestation to ensure the integrity and confidentiality of data and applications. These policies along with the audit logs help easily verify compliance requirements and regulations like GDPR and HIPAA.
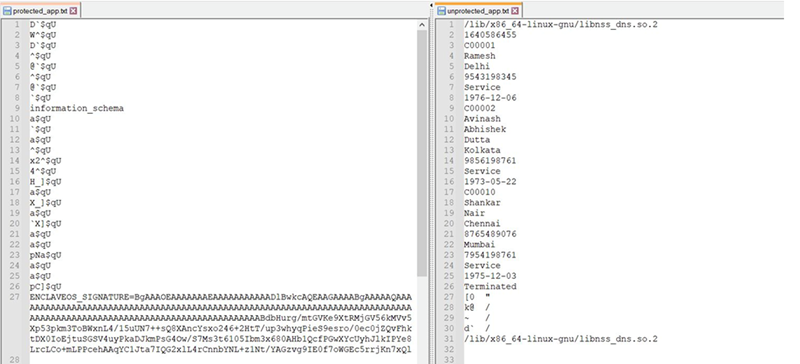
Repeating the same exercise of SQL query in a confidential VM, let us evaluate the content of the memory dump file in figure LH2. Recreating figure RH2 which is the memory dump of unprotected application alongside for easy comparison. There is no sensitive information that you see in the memory dump file (figure LH.2) of the application protected by the Fortanix confidential computing technology.
With the announcements of Confidential VMs by the major cloud vendors and Fortanix helping accelerate enterprise deployments in real-world settings with its Confidential Computing technology, the time is ripe for you to protect your data from breaches and make a secure statement to your customers.
To know more about Fortanix Confidential Computing Manager, read here.
Got question? Want to talk to our experts? Click here.
Want to see the magic working for your environment? Book a free demo here.

 Cite this article
Cite this article








