One of the data risks today is limited data visibility.
Limited data visibility occurs because of data dispersion in cloud and hybrid environments. It refers to how data is spread across multiple locations, such as cloud services, on-premises systems, and third-party applications.
When data is siloed, security teams cannot get a comprehensive overview of where sensitive information resides. As a result, it creates "blind spots"—where data is vulnerable because it is not actively monitored for unauthorized access or potential breaches.
Secondly, data visibility issues can worsen with the accumulation of test data stores. DevOps teams frequently create numerous data stores for testing purposes. They must create these separate environments and conduct testing to avoid jeopardizing actual production data.
To solve the above challenges, Data Security Posture Management (DSPM) is more important than ever.
DSPM provides visibility into an enterprise data security status for real-time risk assessment. It monitors data assets, classifies data sensitivity, and data access permissions.
DSPM takes a multi-layered data security approach. This approach identifies whether data is protected at various levels and stages, combining preventive, detective, and corrective controls.
How Data Security Posture Management (DSPM) Works:
1) Data Discovery and Classification: DSPM tracks data location, access, usage, and security status. It employs advanced automation tools to monitor various data repositories, identifying sensitive information like social security numbers and credit card details. DSPM solutions classify data based on predefined categories and sensitivity levels against real-time monitoring and dynamic data flows within an organization.
2) Anomaly Detection: DSPM sets a baseline for normal data activity and continuously monitors real-time data against this standard. It identifies anomalies that could indicate potential threats or unauthorized actions, alerting security teams to investigate and address risks. Anomalies may involve unusual access patterns, unexpected data transfers, or changes in user behavior that suggest account compromise.
3) Data Risks Assessment: DSPM detects account compromises and takes corrective actions like reconfiguring access controls, applying patches, and revoking unauthorized access. It maintains detailed logs of data audits and automatically updates data management policies to ensure compliance with new regulatory requirements.
However, Data Security Posture Management is not enough for data security. It does not evaluate the encryption standards applied to the sensitive data. You also need to supervise the cryptographic security posture.
Let us understand why.
DSPM helps enterprises identify their data location and whether it is protected, which is a basic necessity. Beyond this, organizations need to know how well their data is protected/encrypted and whether there are any discrepancies with the encryption policies.
Limitations of DSPM Tools
- Insufficient Encryption Evaluation: While the DSPM solution successfully identifies the locations of this data and flags potential access issues, it fails to scrutinize the encryption standards in place. For instance, an organization may still use an outdated encryption algorithm such as Triple DES, which is considered weak by current security standards. As a result, while the DSPM tool highlights where the data is stored and who can access it, it does not recognize that the underlying encryption may be easily compromised.
- Overlooking Key Management: Key management refers to generating, distributing, and storing encryption keys, which are fundamental to protecting data. When an organization uses a robust DSPM to monitor where its sensitive data resides and who has access to it, however, if the encryption keys used to protect that data are stored on a shared network drive without proper access controls, a malicious actor could easily access those keys and decrypt the data. In this case, the solution through DSPM tools fails to provide a complete security posture because it does not evaluate the security measures surrounding key management, leaving the organization vulnerable to potential breaches despite having visibility into its data assets.
- Complexity in Hybrid Environments: An organization utilizing a private cloud for sensitive data and public cloud services for less critical workloads may have differing security policies and enforcement mechanisms for each environment. Consequently, if a vulnerability is identified in the public cloud but not adequately assessed in the private cloud, attackers could exploit this inconsistency. The reliance on multiple vendors means that the security measures may not be uniformly applied, complicating the data protection efforts and making it difficult to ensure complete compliance and security monitoring across all platforms. DSPM alone is not enough.
As a solution, enterprises need a Security Control Evaluation to flag any gaps or insufficiencies in encryption, such as Fortanix Key Insight.
How Does Fortanix Key Insight Work
The solution helps overcome the challenges of securing data and key management. Key Insight discovers keys and maps them to data services across a dispersed multi-cloud environment. it works on three fundamentals.
1) Discover and visualize all encryption keys, their mapping to cloud data services, and lifecycle management status.
2) Assess data security risk posture against established policies, regulations, and industry standards.
3) Remediate large-scale corrective actions to continuously comply with security policies and regulatory mandates.
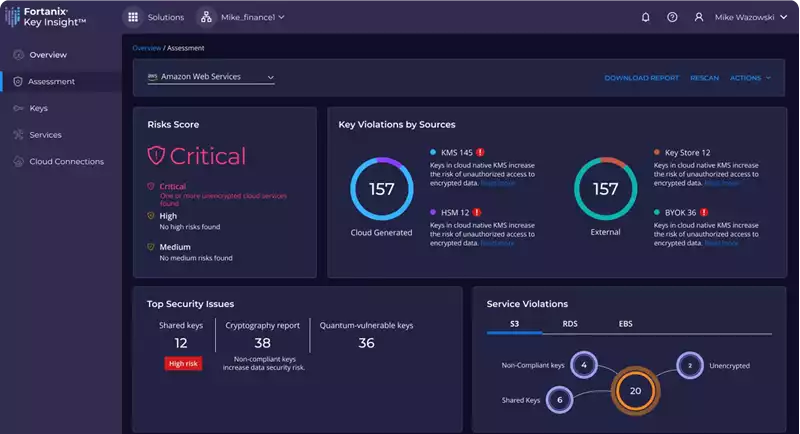
What You Get with Fortanix Key Insight
Consider the following benefits:
- Discover and catalogue your encryption keys and data services from a single view.
- Monitor all keys across multi-cloud environments, track their lifecycle, and see how they connect to cloud data services.
- Automatically gather and organize information about keys and data services across the organization or individual accounts.
- Use a unified dashboard to oversee cryptographic security, with options to dive deeper into specific issues.
- Data-driven heatmaps help you spot major security risks and prioritize action steps. Detect keys that are vulnerable to quantum attacks.
- Keep track of your overall cryptographic security with a single score.
- Visualize which services are at risk using an intuitive key-service relationship diagram.
- Assess the potential impact of a compromised service with a blast-radius diagram.
Conclusion
As data grows exponentially, the number of encryption keys required to protect this data also increases. This creates a new challenge: managing and securing a vast number of keys. While Data Security Posture Management (DSPM) provides solutions for protecting large amounts of data, it’s only a first step in understanding your attack surface. To effectively secure your enterprise data, you must also implement strong encryption strategies and Key Management practices.
Fortanix Key Insight ensures that all encryption keys are effectively handled, stored, and monitored, which is non-negotiable for maintaining robust data security.
Connect with our team and take a free trial now.

 Cite this article
Cite this article









