Today, Fortanix introduced a new feature in the Fortanix DSM to support integration with the Google Cloud’s External Key Manager service, which was announced today at the Google Cloud Next UK conference. Google Cloud’s External Key Manager allows certain services running in the Google Cloud Platform (GCP), namely Big Query and Google Compute Engine (GCE) to use an encryption key managed in an external key management service and controlled entirely by the customer.
In the first part of this blog series, we’ll provide an overview of Google External Key Manager service, how Fortanix takes advantage of this new capability and the value to Google Cloud and Fortanix joint customers.
While many cloud service providers have allowed customers to bring their own keys (BYOK), Google Cloud Platform is the first public cloud provider enabling customers to bring their own key management system (BYOKMS) where encryption keys can be stored in their own data centers with a single point of management and auditability.
With this new capability, Fortanix customers can migrate new classes of sensitive financial services, healthcare and other applications that require the highest levels of data privacy compliance to the public cloud.
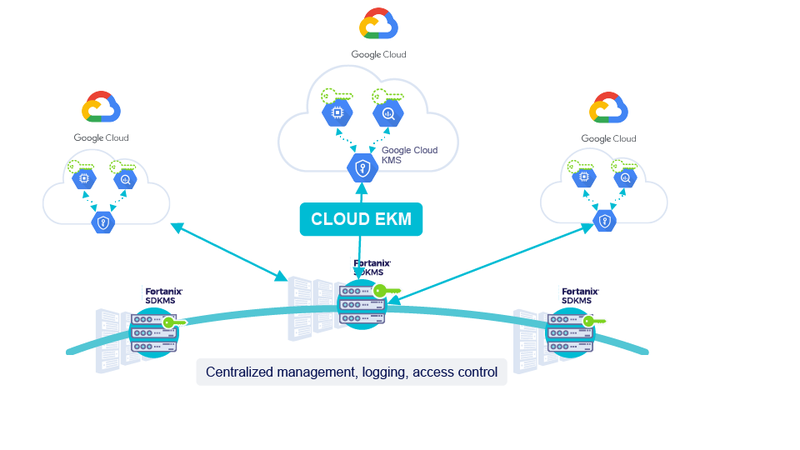
External Key Management with Fortanix DSM provides customers the following benefits:
-
Complete Control of Keys - Fortanix provides customers with a kill switch, which allows them to stop decryption of data-at-rest in certain GCP services by simply disabling their key in Fortanix DSM. As the key material never leaves Fortanix DSM, the customer is in complete control of how to authorize the use of the Google Cloud’s External Key Manager keys. This level of control has never before been available to customers as they adopt public cloud.
-
Achieve Compliance - Many companies want to move to the public cloud to get all the benefits associated with it but are held back by regulators who insist that they manage their own keys and secure them by storing them in FIPS 140-2 Level 3 certified hardware security modules (HSMs). Fortanix DSM offers a FIPS 140-2 Level 3 Fortanix Runtime Encryption Appliance, enabling financial services, healthcare and other regulated industries to meet their compliance requirements. TM: A Certification Mark of NIST, which does not imply product endorsement by NIST, the U.S. or Canadian Governments
-
Simplified and Centralized Encryption - Many companies are adopting a multicloud or hybrid cloud strategy to augment their internal data centers, which often creates many different systems and ways of managing the lifecycle of encryption keys. Managing keys in five or six different hybrid, public cloud and on-premises environments increases complexity, cost and security risk. As workloads move to the cloud, keeping cryptographic keys secure and making them available to applications and services regardless of where they run is critical to successful digital transformation. Google Cloud’s External Key Manager makes it possible for Fortanix DSM to become that single, simple and centralized encryption platform that accelerates moving applications to public cloud, while providing a single set of cryptographic services to on-premises, hybrid and cloud workloads.
How does Google Cloud’s External Key Manager work?
Services running on GCP, such as Big Query and GCE, currently can use an encryption key hosted by Google Cloud KMS or Cloud HSM to secure their data at rest.
An envelope encryption scheme is followed where the data is encrypted using a local data encryption key (DEK), which in turn is encrypted using a key encryption key (KEK) in Cloud KMS or Cloud HSM. While the encrypted DEK is stored with the data, the KEK lives in Google Cloud KMS or Cloud HSM.
Give a read on how Fortanix secures VMware Infrastructure on Google Cloud.
To allay the concerns of some of their customers who don’t want to trust the public cloud with both their keys and data, Google has introduced External Key Manager, which extends the envelope encryption scheme to allow the KEK to be encrypted using an externally managed key encryption key (EKEK).
How do Google Services use Cloud EKM keys from Fortanix DSM?
Currently, Google Compute Engine (GCE) and Big Query are the two services which can use Google Cloud’s EKM. To configure these services to use a key managed in Fortanix DSM, an externally managed key needs to be created in Google Cloud KMS, which is linked to the actual key in Fortanix DSM. All requests to use this externally managed key are automatically sent to Fortanix DSM.
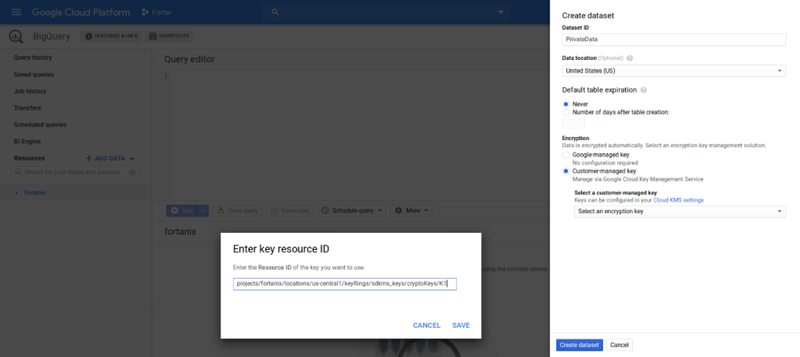
In Big Query, customers can choose to disable result set caching, in this mode, every request to decrypt the data goes to Fortanix DSM. This would allow Fortanix to become a kill switch, where an administrator can simply disable the key used by Big Query, and new queries for datasets associated with the Fortanix key would be prevented.
This is an extremely powerful feature for many customers who would like to be in control of their data even when they make it available to public cloud to take advantage of the analytics solutions such as Big Query.
Key Access Justifications: Decide When and How Your Data can be Decrypted
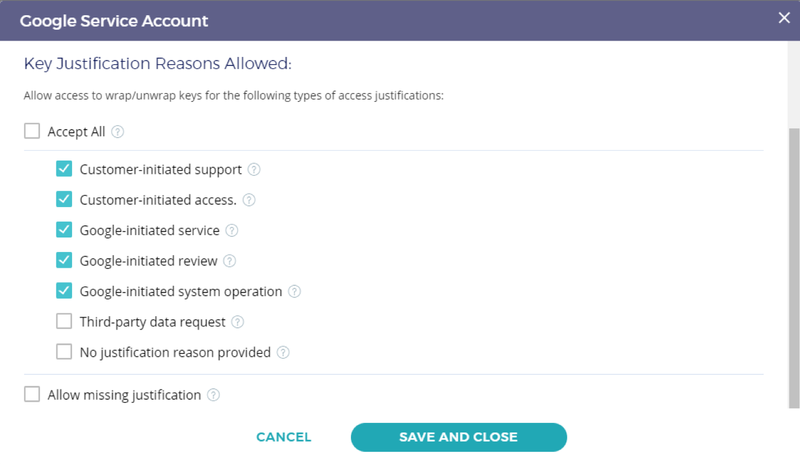
Key Access Justifications is an upcoming feature that will work with Google Cloud’s External Key Manager. It will provide a detailed justification each time one of your keys is requested to decrypt data, along with a mechanism for you to explicitly approve or deny providing the key using an automated policy that you set.
Coming soon, Fortanix will also take advantage of Google Cloud’s Key Access Justifications, enabling customers to accept or reject cryptographic requests through External Key Manager based on an access reason policy.
For example, the administrator could allow a customer or Google initiated access to the Key Encryption Keys (KEK) but reject access to third-parties or when no justification is provided. When a cryptographic operation is performed using the KEK, Fortanix creates an audit log entry for each operation which includes the access reason.
The combination of Google Cloud’s External Key Manager, Key Access Justifications and Fortanix will deliver a level of control that will make you the ultimate arbiter of access to your data stored in the Google Cloud Platform. Key Access Justifications is coming soon to alpha for BigQuery, Compute Engine and at-rest Persistent Disk.
Stay tuned for Part 2 of this blog series for more detailed implementation information on implementing Fortanix DSM with Google External Key Manager and Key Access Justifications.
Availability of Google Cloud External Key Manager and Fortanix Integration
Google Cloud External Key Manager is currently available in Alpha on Google Cloud and will soon be coming to Beta. The Fortanix DSM integration will also be soon available in Beta and is available as an on-premises solution with a FIPS 140-2 Level 3 validated Fortanix Runtime Encryption Appliance, as software that can be deployed on-premises, and as SaaS offering through Equinix SmartKey, powered by Fortanix.
Google Next London 2019 Announcement:
For those at Google Next London 2019, We recommend attending- Bringing You More Control: New Services for Data Security and Transparency on Wednesday, November 20th at 4:15–5:05 PM
Speakers:
- Greg King, Information Security Engineer, Paypal
- Il-Sung Lee, Senior Product Manager, Google Cloud
- Joseph Valente, Product Manager, Google Cloud

 Cite this article
Cite this article








