Data is the new gold, and enterprises are under immense pressure to minimize data exposure risks by tightening internal data security policies. Expanding data privacy regulations, such as the GDPR, are also obstructing cloud expansions because they require organizations to increase their cloud data security control. Security and compliance teams face a significant challenge managing data sprawl and an ever-growing list of security tools across dynamic multicloud infrastructures.
Data encryption is a highly effective solution to secure and control access to organizational data. Encryption safeguards data wherever it resides, making encryption key management and security crucial to an organization’s security posture. The effectiveness of encryption hinges on the strength and management of these keys, which need to be regularly discovered, updated, and rotated. With the rise of quantum computing, traditional cryptography must be re-evaluated, especially regarding key strength and types.
Insurance Company in Search of Control
A well-known global insurance company approached Fortanix to gain control over its cryptographic security posture. To effectively govern corporate data security policies, their security and compliance teams require centralized and detailed visibility into their crypto security posture.
They needed to know, at any point in time, exactly which cryptographic keys were in use, where they were deployed, and which data services utilized those keys. Immediate insight into encryption strengths and key lifecycle information was also essential.
Their infrastructure spanned Azure and Google Cloud, using hundreds of services and thousands of keys for both symmetric and asymmetric encryption. Regulatory auditors required the company to demonstrate comprehensive control of keys, their details, and their mapping to services.
NIST and security best practices recommend using a unique key for each service, akin to using different keys for different homes, even if owned by the same person. Unfortunately, many enterprises often share a single key between multiple services, weakening their security posture. Locating such misalignments with security policies is time-consuming and predominantly manual, occupying valuable cycles of the insurance company’s cloud and security teams.
However, this information is essential to prove compliance, prompting the CISO to task admins across multiple cloud teams with mapping keys, detailing key attributes, and identifying which services use them. This labor-intensive task is prone to errors and can easily consume team resources for weeks or months.
Fortanix Key Insight identify these vulnerabilities within minutes. The security teams configured Key Insight to scan their cloud environments with a read-only account, and within about 10 minutes, they had a detailed view of the company’s cryptographic posture. The teams could immediately see the total number of keys, encryption types, key-to-service mappings, and an overall risk assessment.
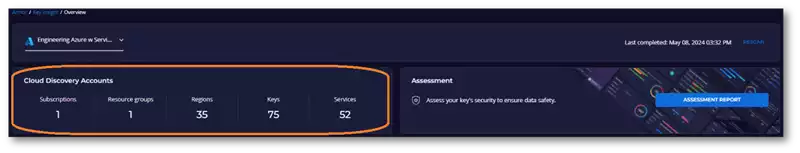
Figure 1: Discover Keys and Services
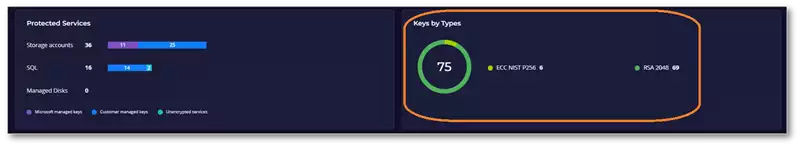
Figure 2: Key Encryption Type Discovered Automatically
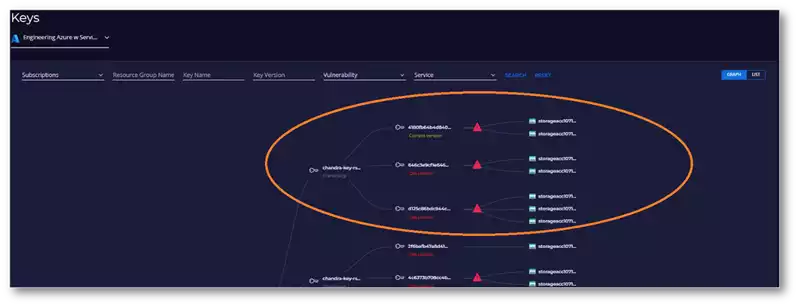
Figure 3: Vulnerabilities Identified in Keys mapped to Services
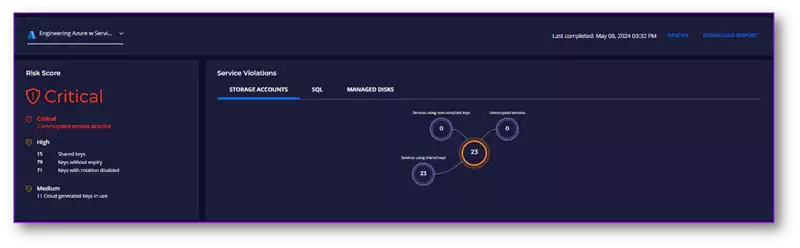
Figure 4: Overall Risk Assessment and Service Violations
Conclusion
Like many other enterprises, this insurance company knew they had to take control of their cryptographic security posture to meet and prove compliance. Instead of burdening their security and compliance teams with cumbersome, error-prone manual tasks, Key Insight provides security teams and auditors with all critical information from a single dashboard so teams can prioritize the most pressing risks, quickly improve the insurance company’s security posture, and accelerate compliance.
Contact and Trials:
- For more information, contact a Fortanix sales representative: Contact Us
- Test drive Key Insight and Data Security Manager for free: Start Your Free Trial

 Cite this article
Cite this article









