As RSA Conference is growing bigger and noisier every year, it’s becoming harder to take a bird’s-eye view of the security space. Still, a few observations can be drawn.
The birds are out of the cage
The main themes over the last years - dead perimeters, emergent AI/ML, and rise of DevSecOps:
- Perimeter is officially dead, but its spirit still lingers on. It’s frequently mentioned, always in negative and past sense. Interestingly, very few people remember the beginning of it all – good old Jericho Forum, back in 2003.
- With Endpoint security AI/ML is all the rage. AI/ML is carried out mostly in the backend/cloud, as it’s becoming increasingly hard (not to say impossible) to autonomously detect/prevent on the endpoint itself. And there’s the common belief (or conviction – depending on who you ask) that performing AI/ML on numerous and bigger datasets will improve the accuracy of the results.
- With device management and enforcement AI/ML is all the rage too! It’s becoming im-possible to handle the plethora of devices coming in and out of the local network. Still, efforts are made to introduce new solutions, which are using AI/ML to help identify and manage rogue and unauthorized devices.
- Adding AI/ML in the course of the last few years haven’t brought any radically new and disruptive technologies or solutions.

So where did the innovation go?
Encryption.
It appears that the only significant new technology introductions occur on the data encryption side of things.
The new face of encryption: Business enabler
With the introduction of new encryption technologies, encryption is able to be extended to new domains – encrypt applications as they run, perform analytics on encrypted data etc.
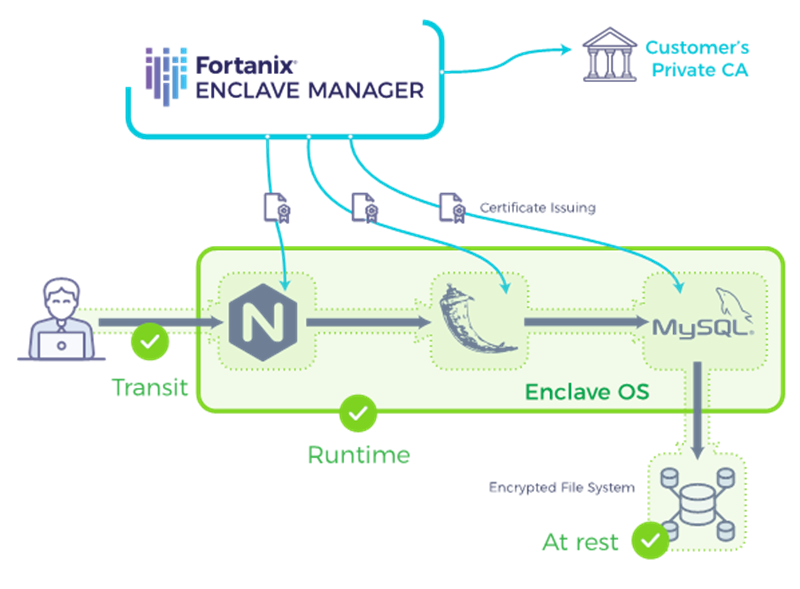
It’s not a surprise then, that the runners-up in the last two years at RSA Innovation Sandbox are next-gen encryption companies: Last year it was Fortanix, with its groundbreaking Intel® SGX-based Runtime Encryption® and this year the homomorphic encryption company Duality.
The next-gen encryption isn’t just helping encrypt data-at-rest or data-in-motion, but helps encrypt data-in-use, that is – encrypt the application and the data it’s processing, as it runs.
"It’s intriguing to see how encryption has come full circle. For the first time, encryption can help secure the security applications and provide private and anonymous analytics on sensitive data."
How does it work?
The vital need is to assure that the analyzed sensitive data will never be exposed to any party. Only the analytics results are shared with the relevant parties.
This can only be achieved by running the application logic or ML model (or the entire analytics application) inside trusted execution environment such as Fortanix RTE.
Where is it applicable?
- Encryption of any application logic or ML model querying the collected data from endpoints, servers and network devices — or any dataset for that matter — thus assuring these won’t be the source of data breach.
- Encryption of any enterprise or web application, so that no malicious user can hack it and infiltrate sensitive data or worse – encryption keys.
- Allow to host and run sensitive data on untrusted cloud infrastructure.
Put the birds back in the cage
For the first time, encryption is becoming an enabler of business, rather than the traditional restrictive “sealing” solution. These new types of encryption ARE becoming the new perimeter, only one that’s not porous and frail. They protect and tightly secure the application (e.g. a perimeter of sorts), only doing it deterministically, and without incurring any changes to these applications and infrastructures.
So – how do you bring the birds back to the cage? – Encrypt them!
If you want to learn more, please visit our Runtime Encryption® page.

 Cite this article
Cite this article