Huge Data Loss at VW
On the 27th of December 2024, the Chaos Computer Club (CCC) [source] has disclosed a massive data loss at Volkswagen (VW). CCC published this information in the online video We Know Where Your Car is [source]. The data loss included loads of Personally Identifiable Information (PII) data including:
- 600,000 user data (user-id, name, email address and sometimes: date of birth, mobile number and address)
- 9.5 TB telemetry data including GPS coordinates of 800,000 cars. The majority of these with a precision of 10cm.
CCC analyzed the GPS coordinates and was able to link them to people who work for e.g. the German Federal Counsil, Military Counter-Intelligence Service, Federal Intelligence Service.
Further, they could identify who had visited lawyers or news agencies, which undermines the source protection of individuals. CCC tracked which golf club was visited by bank board members, which specific catering agency was responsible for preparing food for government officials and who visited brothels.

Figure 1: Company collecting telemetry data of vehicles
The data was collected from the VW owned car brands VW, Audi, SEAT and Škoda all over the world starting in December 2022 with SEAT, the other brands followed later. This is a serious violation of several data protection regulations and especially the European General Data Protection Regulation (GDPR).
Fortunately, the data was exploited by a white hat hacker who did not misuse the data. Realizing what she had harvested, she handed over the data to CCC, who disclosed the findings to VW so that they could close their security gaps immediately. The affected individuals and organization can only hope that there was no black hat hacker exploiting the same security gap earlier and does not misuse this data.
Though it is not known why VW has collected this vast amount of data, there is room to assume the data was harvested in good will, e.g. to improve their battery management and to provide helpful information for their users through the VW Fleet Interface [source].
How was the Hack Conducted
VW uses the same vehicle platform for their electric components across their own car brands and provides the same connectivity services to their customers. This is why the hacker was able to retrieve information for all these VW brands. The precise procedure of the attack was not revealed, but it was probably conducted like the following:
- The hacker searched for subdomains of organizations, e.g using Subfinder.
- The hacker looked for directories within the found subdomains by using typical directory names using e.g. Gobuster.
- The hacker found a Spring directory of a web application containing heapdumps.
- By analyzing the heapdumps, the hacker found API endpoints, AWS credentials and IdP credentials. This information resided inside the heapdumps as plain text.
- Using this information, the hacker was able to download all the unencrypted telemetry data from cloud services and to impersonate users and retrieve the data of these users.
What did VW do Wrong?
Following the disclosure, CCC was able to detect these VW wrongdoings of protecting their specific data:
- VW collected far too much data, which they probably do not need.
- The GPS data was not shortened, as described in their general terms and conditions.
- The Spring configuration of the web application was misconfigured.
- Some directories were not password protected.
- Some passwords had been rotated but the old ones were not invalidated.
- The data was not encrypted.
To the last point, as CCC states at the end of their presentation, the most fatal mistake was to NOT follow the principle of Privacy by Design [source], which demands protection of data.
This is typically achieved by encryption of data. Encrypting your data is your last line of defence. If you encrypt your data properly, they are still protected, even in the case of a breach.
Coincidently, I had pointed out exactly that in my blog You Forgot to Lock Your Chest just a few weeks before CCC has disclosed this VW data breach.
Probable Consequences for VW
Based on this disclosure, VW can probably be accused of gross misconduct by violating:
- VW’s own general terms and conditions.
- Article 32 GDPR [source], as it demands encryption of PII data.
- Article 9 GDPR [source], which prohibits the collection of special PII data, like political views or religious belief. This data could be derived from the GPS data, as they reveal parking in proximity to party offices or churches.
- Privacy regulations of countries outside of the EU, as VW cars are operated all over the world.
So, what are the consequences for VW due to this data loss? In this blog, I just focus on the EU-wide concerns as the GDPR are probably the strictest privacy protection regulations in the world. Here in the EU, VW is likely to face:
- The need to inform all persons (at least 600,000) that are affected by the data breach as demanded in article 34 GDPR [source].
- Enormous fines for losing PII data, as defined in Article 83 GDPR [source]. This article states that the fine can be “up to 2% of its entire global turnover of the preceding fiscal year”. In the fiscal year, VW had a global turnover of 322.3 billion Euros [source]. To quickly do the math, this could add up to 6.4 billion Euros.
- Big reputation loss, which may lead to less sales, as prospects may refrain from buying VW car.
- Class action lawsuits by affected persons. The outcome of those is unclear.
How Could the Data Loss have been Prevented?
The previous chapter “What Did VW Do Wrong?” reveals many things that VW could have done to prevent the attack. However, the most important approach that VW has missed to implement is the Privacy by Design. If VW had enforced a stringent encryption of the data and a proper access management to the encryption key, this data breach would not have happened. Of course, we do not know the architecture of the VW software, but it can be assumed that a design like the one depicted in Figure 2 would have prevented the attack.
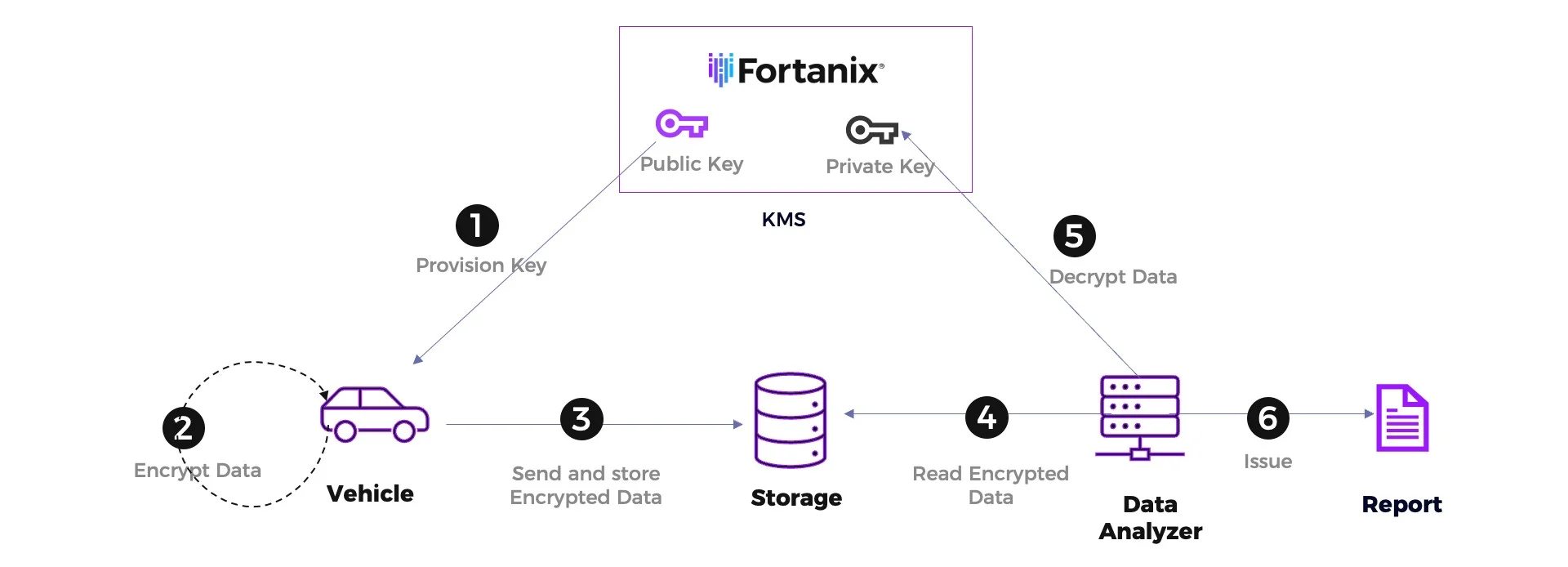
Figure 2: Secure telemetry data design
This diagram shows an asymmetric encryption scheme to protect the data. Ideally, you would go for a hybrid encryption, but for the sake of simplicity, the technical details about the symmetric encryption are left out in this diagram.
The asymmetric key pair, consisting of a private and a public key, are generated and managed within a Key Management System (KMS), like Data Security Manager (DSM), which utilized a FIPS 140-2 Level 3 compliant Hardware Security Module (HSM) for best protection of the key. The process steps are as follows:
- KMS provisions the public key to the vehicle. Initially this is done during the production of the vehicle. Later in the field, this could be done as an Over-the-Air (OTA) update as well. A public key is not security relevant and may be shared publicly.
- The vehicle encrypts the collected telemetry data with the public key.
- The vehicle sends the encrypted data to a storage system of the manufacturer.
- At the time a data analyser wants to analyse the data, it reads the encrypted telemetry data from the storage.
- The data analyser asks the KMS to decrypt the data with the private key, which is protected within the secure boundaries of the HSM.
- The data analyser runs the analysis on the plain data and issues a report. After the analysis, the plain data are deleted.
Following this process, the telemetry data are only available in plain with in the data analyser. Consequently, we already have a data at rest and data in motion protection in place. The access to the private key can further be secured by implementing role based access control (RBAC) and dual control with a quorum policy to achieve a zero trust architecture.
To enhance the security even further, it is possible to enhance the solution with a data in use protection by utilizing runtime encryption to this solution. This would change step 5 and 6 from the previous list. Hereby, the data is never available in clear text. The sensitive data is executed in a secure enclave, as it is provided by Fortanix Confidential Computing Manager (CCM).
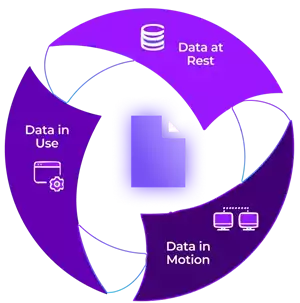
Figure 3: Protection of data at rest, in motion and in use
Conclusion on VW Data Loss
It is blatant that VW has made several mistakes with the collection and protection of their PII data. However, if they had enforced a stringent Privacy by Design approach, as demanded by GDPR, this data loss would not have happened.
Therefore, Fortanix highly recommends encrypting all PII data wherever possible and also provides the required solutions to implement that.
For more information, please contact Fortanix.

 Cite this article
Cite this article