In today’s world, data breaches and privacy concerns are significant threats to organizations that handle sensitive data. When it comes to databases, encryption is a crucial measure to safeguard your data, especially for confidential or personally identifiable information (PII). However, choosing the right encryption strategy can be complex, depending on your data type, licensing, storage constraints, and more.
This guide will walk you through the decision-making process for selecting the most appropriate encryption method for your database, using the flowchart above. The process helps you decide between Transparent Data Encryption (TDE) and File System Encryption (FSE) based on various technical and operational factors.
Understanding the Key Concepts
Before we dive into the flowchart, let’s briefly define the encryption methods you will encounter in the decision-making process.
1. Transparent Data Encryption (TDE)
TDE is a form of encryption that automatically encrypts your database files without affecting the applications or users. It encrypts the entire database at rest, and when the database is accessed, the decryption process occurs on the fly. TDE is ideal when you want minimal performance impact on your operations.
2. File System Encryption (FSE)
FSE encrypts the specific folder and files at the disk level where your data resides, not just the database. It’s a broader encryption mechanism, which may cover everything on the disk. This method is useful when the database does not support TDE, or the enterprise does not have any TDE licenses but still has a need to meet the encryption requirements to adhere security standards/policies.
Steps for Choosing the Right Encryption for Your Database
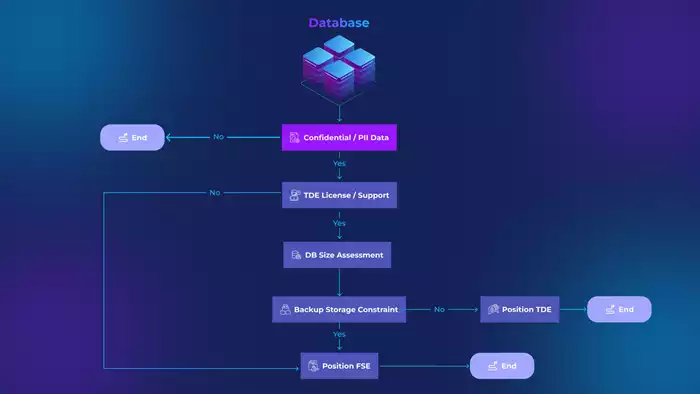
Step 1: Identify if Your Data is Confidential or Contains PII
The first step in determining your encryption strategy is to assess whether the database contains confidential or personally identifiable information (PII). This is the foundation for whether encryption is needed at all.
- If No: If the database does not contain sensitive data, encryption may not be required, and the process ends here. You can safely store and manage your data without additional encryption overhead.
- If Yes: If your database holds confidential information or PII, proceed to the next step.
Step 2: Check for TDE License and Support
If encryption is necessary, the next step is to determine whether your database system supports TDE and if you have the appropriate licensing.
- If No: If TDE is not supported (such as Postgres Community Edition, etc.) or you don’t have the necessary licenses, TDE cannot be used. The flow ends here, and you’ll need to investigate other encryption methods such as FSE or consider upgrading your licensing.
- If Yes: If your database supports TDE and you have the required licenses, move to the next step.
Step 3: Perform a Database Size Assessment
Database size plays a critical role in deciding the encryption method. Large databases may introduce certain performance challenges and storage requirements when encrypted, especially with TDE.
Step 4: Analyze Backup Storage Constraints
After assessing the database size, evaluate the storage constraints. This step involves understanding whether your infrastructure can handle the overhead of encryption on backups.
- If No: If storage is not a constraint and you can manage the encrypted backups easily, TDE is the better encryption approach, since TDE would allow for efficient encryption at rest without significantly altering your storage strategy. End the decision-making process here.
- If Yes: If storage is constrained, such as limited space for encrypted backups, proceed to File System Encryption (FSE) as a more comprehensive encryption solution. FSE can handle broader encryption needs, even covering compressed data backups efficiently. FSE is the better option in this scenario.
Conclusion: Choosing TDE vs. FSE
The decision flowchart simplifies the often-complex task of selecting the right encryption for your database. Here’s a quick recap:
- TDE is the preferred option when your system supports TDE, and storage constraints are not a major issue.
- FSE becomes the go-to option when TDE licensing is unavailable, or storage constraints require a more efficient or generalized encryption approach.
Each organization’s requirements will differ, but following this flowchart ensures that your choice aligns with operational capabilities, compliance needs, and technical constraints.
Additional Considerations
It’s also essential to remember that encryption, while critical, is just one part of a broader data security strategy. Implementing strong access controls, regular auditing, and comprehensive backup strategies should complement your encryption efforts.
By carefully assessing the type of data, database support, and infrastructure capabilities, you can confidently select the encryption method that best fits your organization’s security posture.
This step-by-step guide is a useful approach for IT and database administrators who need a clear pathway to choose between encryption methods while considering operational factors like storage, licensing, and data sensitivity.











