Cloud Security Posture Management (CSPM) tools continuously assess cloud environments against pre-defined security policies to detect vulnerabilities, misconfiguration, and compliance issues. This is a necessity because cloud environments can change rapidly due to frequent updates, new deployments, and dynamic configurations, which can inadvertently introduce vulnerabilities.
However, this security level can validate your cloud infrastructure's security but does not guarantee that the data is fully secured.
Let us understand how CSPM tools work, why they are insufficient on their own, and why every data security strategy should prioritize protecting the actual data.
How CSPM Tools Work
- Continuous Monitoring
Cloud security posture management tools monitor cloud infrastructure 24/7, scanning configurations, permissions, and assets to detect security gaps that could lead to breaches or non-compliance. - Configuration Analysis
These tools analyze cloud configurations, comparing them against predefined security policies and industry standards. If any misconfigurations are found (e.g., open S3 buckets), they trigger an alert. - Automated Remediation
CSPM tools provide automated remediation options, allowing organizations to fix issues with minimal manual intervention. This could involve applying security patches, closing open ports, or adjusting overly permissive access controls.
Limitations of Cloud Security Posture Management Tools in Securing Data
- Focus on Infrastructure, Not Data
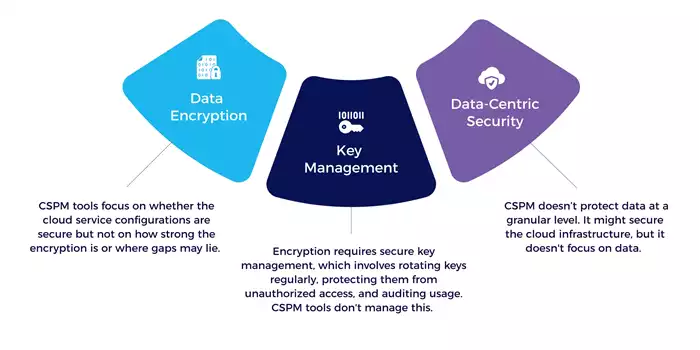
Cloud security posture management (CSPM) tools focus on the configuration and security of the cloud infrastructure — things like open ports, permission settings, and misconfigurations. They prevent unauthorized access but don’t protect the data itself. A secure infrastructure is essential, but data security requires more than well-configured resources. - Lack of Encryption and Key Management
CSPM tools may ensure that certain services like encryption are enabled but don't focus on how well data is encrypted or how encryption keys are managed. Data security is not limited to encrypting data at rest and in transit but also securely managing encryption keys. CSPM tools don’t handle the complexities of key rotation, access control to keys, or monitoring who has access to those keys. - No Insight into Data Sensitivity
CSPM tools cannot assess the sensitivity of data stored in the cloud. Without understanding the nature of the data—whether personal, financial, or confidential—CSPM lacks context for data security strategies. Even if encrypted, critical data can still be vulnerable if encryption methods or key management are not up to best practice standards. - Encryption Gaps
CSPM may flag cloud vulnerabilities but doesn't focus on how well data encryption is implemented. For example, it won’t highlight the risk of using AES-128 instead of stronger AES-256 implementations.What is Missing in CSPM Tools?
How do you solve the limitations of CSPM tools to achieve complete data security?
Beyond continuously assessing the cloud infrastructure, organizations need full visibility into the effectiveness of encryption applied, where all encryption keys are, and how data services use them.
Get Fortanix Key Insight, a data security solution that helps organizations proactively manage data exposure risks due to a lack of visibility and control of their cryptographic posture. Fortanix Key Insight automatically reveals what data has been encrypted, the type of encryption keys, and which workloads use them in AWS and Microsoft Azure cloud environments.
Benefits of the Fortanix Key Insight
- Accelerate security audits: Discover all encryption keys and data services—With read-only access, Key Insight scans the infrastructure, allowing organizations to discover all encryption keys across on-premises and multi-cloud environments. From a centralized dashboard, users get a comprehensive inventory to see where all keys are, and how they map to various data services.
- Data-driven risk prioritization: Key Insight provides immediate insight into your most significant risks, including unencrypted services, keys shared by multiple services, keys without expiry (long-lived), or keys without scheduled rotation. Security teams can use this information for remediation.
- Assess encryption key blast radius: Encryption keys should be limited to a single service to control risk and ensure precise, detailed logging. However, some organizations may not realize they share keys across multiple services. Key Insight instantly reveals which services use a key and identifies those that would be impacted in the event of a key compromise.
- Detect quantum vulnerabilities: thoroughly assessing cryptography usage and whether the algorithms are robust enough for the post-quantum era. Key Insight uncovers where and how encryption keys are deployed across on-premises and multi-cloud environments, helping organizations detect quantum vulnerabilities and prioritize when and where to implement post-quantum cryptography.
Conclusion
Cloud Security Posture Management tool focus solely on cloud infrastructure security, leaving cryptographic data protection unchecked. For complete control and visibility over your data’s security, Fortanix Key Insight is the solution. Contact our team today to schedule a demo and see it in action.











