Fortanix Confidential Computing Manager integrates with Microsoft Azure Kubernetes Services (AKS) platform to create, manage, and secure confidential containers on Microsoft Azure confidential computing infrastructure. In our previous blog Secure Your Containers with Confidential Computing, we talked about the underlying technology and benefits of using trusted execution environments (TEEs) (also known as secure enclaves) to reduce the risk of running sensitive applications in cloud-based containers.
In this blog, we will discuss how developers can make application containers confidential with Fortanix and deploy these containers within the AKS platform, with new support for confidential containers.
We are pleased to see Fortanix integrating with Microsoft Azure Kubernetes Service to convert and manage confidential containers. This new capability makes it simple and fast for developers to quickly secure data in use for sensitive containerized applications.
—Vikas Bhatia, Head of Product, Azure Confidential Computing, Microsoft
At Fortanix, we have been building the foundation for confidential computing with our Runtime Encryption® technology for more than 4 years. Fortanix Confidential Computing Manager and Enclave Development Platform (EDP) are used in production to power confidential computing use cases such as privacy-preserving analytics, secrets managements, tokenization, federated learning in various industry verticals such as healthcare, finance, and defense.
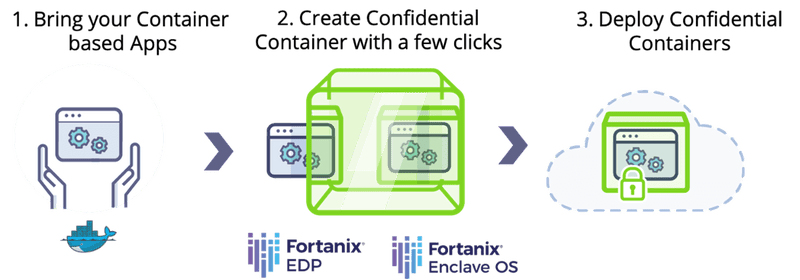
Managed Kubernetes services like AKS allow developers to focus on developing their applications’ logic and offload all other infrastructure requirements such as scaling, upgrade, and visibility to the platform by simply writing configuration files.
Combining managed Kubernetes services with technology such as service mesh can attach additional infrastructure logic for request routing, alerting, and service discovery as a side-car proxy to the applications.
Similarly, with confidential containers, developers get additional confidentiality and security right out of the box for their applications.
UCSF's Center for Digital Health Innovation is pleased to be collaborating with Fortanix, Intel, and Microsoft Azure to establish a confidential computing platform with privacy-preserving analytics to accelerate the development and validation of clinical algorithms.
The platform will provide a “zero trust” environment to protect both the intellectual property of an algorithm and the privacy of healthcare data. Using Fortanix Confidential Computing Manager for orchestration of Intel’s SGX secure enclaves on Azure confidential computing infrastructure with Azure Kubernetes Service (AKS), and CDHI’s proprietary BeeKeeperAI data access, transformation, and orchestration workflows, the platform will reduce the time and cost of developing clinical algorithms.
—Michael S. Blum, MD FACC, Associate Vice Chancellor for Informatics and Chief Digital Transformation Officer, Executive Director, Center for Digital Health Innovation, Professor of Medicine, Cardiology at the University of California San Francisco
When developers run an application that processes sensitive data in the public cloud as a confidential container on a managed Kubernetes cluster inside a service mesh, data enjoys additional protection; not only is sensitive data protected when it traverses the network traffic (data in motion) and when it is stored on disk (data at rest) but also in memory while the application is running (data in use) – all without changing a single line of code.
Fortanix confidential containers enable developers to pick and choose applications that require confidential computing with the switch of a button, by simply setting an attribute in the configuration. Existing deployments can otherwise remain unchanged with other applications running unaffected outside a secure enclave.
Developers can identify confidential containers and can establish secure communication among them by using identity certificates issued by the Fortanix Confidential Computing Manager and establish trust by being rooted in Intel® SGX remote attestation.
Fortanix confidential containers use Intel® SGX as the underlying hardware-based security technology with each container running inside a secure enclave. This approach is different from confidential Virtual Machines (VMs) where entire VMs are run inside secure enclaves, which consumes more resources.
Confidential containers provide developers with the flexibility of running the bare minimum application code inside the secure enclave boundary and remotely verifying the integrity and identity of their application through remote attestation.
As a result , the Trusted Computing Base (TCB) in Fortanix confidential containers is generally an order of magnitude smaller than a typical confidential VM. By deploying each individual containerized application in its own secure enclave, developers can achieve a much greater level of isolation between applications, compared to confidential VMs where the applications inside the VM would be exposed to the operating system and to each other.
With Fortanix, developers can easily change their containerized applications such as databases, web proxies, secret vaults, or any application containers to confidential containers with a single click, in a matter of seconds, without any need to modify or recompile the application.
Get started with a Fortanix Confidential Computing Manager free trial account that will enable you to create confidential containers through an intuitive UI or REST APIs to create confidential containers. You can find a Fortanix Quick Start guide here that will walk you through the process and additional documentation on the Fortanix integration with Microsoft Azure Kubernetes Service.

 Cite this article
Cite this article








