Organizations use Data Security Posture Management (DSPM) and Cloud Security Posture Management (CSPM) to protect data. But what sets these two solutions apart, and how do you determine which is best for your needs?
Are they sufficient to ensure comprehensive data security, or is there more to consider? This blog post will explore the fundamental differences between DSPM and CSPM, identify gaps, and provide insights on how to address them.
What is DSPM?
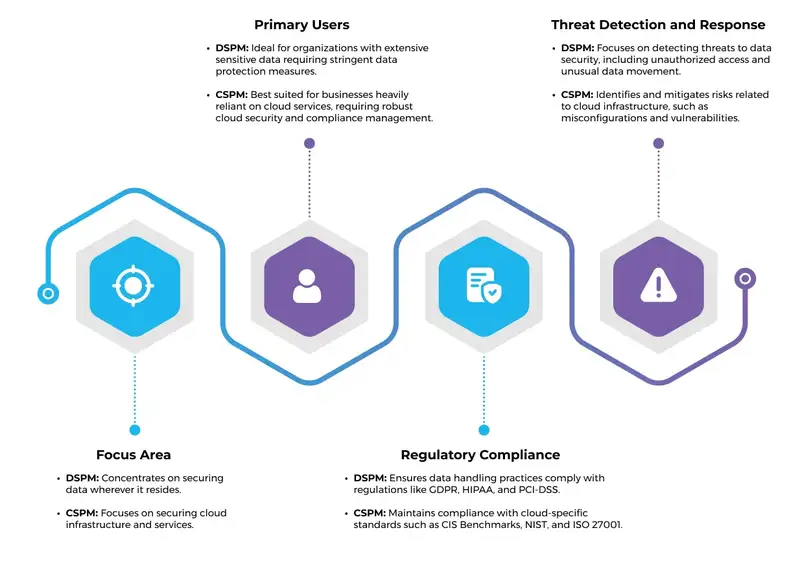
Data Security Posture Management (DSPM)'s primary goal is to ensure that all data remains secure, regardless of where it resides. Data Security Posture Management (DSPM) focuses on data identification and classification.
It does not evaluate the encryption standards applied to the sensitive data. We will discuss more on this later. For now, let's see what typical features DSPM solutions offer:
- Data Discovery and Classification: Identify and categorize data based on sensitivity and type.
- Data Encryption: Ensure data is encrypted in transit and at rest.
- Access Control: Manage who has access to data and monitor any permission changes.
- Threat Detection: Identify potential threats to data security, such as unauthorized access or unusual data movement.
- Compliance Monitoring: Ensure data handling practices meet regulatory requirements like GDPR, HIPAA, and PCI-DSS.
Key Benefits of DSPM
- Data Visibility: Know where your data resides.
- Proactive Threat Management: Detect and mitigate threats to your cryptographic security posture before they can cause harm.
- Regulatory Compliance: Maintain compliance with industry regulations, avoiding hefty fines and legal repercussions.
What is CSPM?
Cloud Security Posture Management (CSPM) secures the cloud infrastructure. CSPM solutions continuously assess the security posture of cloud environments and provide recommendations for improving it.
Key features include:
- Configuration Monitoring: Check cloud resources for misconfigurations that could lead to vulnerabilities.
- Compliance Auditing: Automatically audit cloud environments against industry standards and best practices.
- Risk Assessment: Identify and prioritize risks based on potential impact.
- Incident Response: Tools for quick response and remediation of security incidents.
- Cost Management: Monitor cloud resource usage to help manage costs effectively.
Key Benefits of CSPM
- Continuous Monitoring: Real-time assessment of your cloud environment to identify and fix vulnerabilities.
- Automated Compliance: Keep your cloud infrastructure compliant with regulatory standards.
- Improved Cloud Governance: Gain better control over cloud resources.
DSPM vs. CSPM: A Detailed Comparison
DSPM and CSPM Is Not Enough
DSPM and CSPM serve essential roles in the security landscape but are designed for different purposes. If your primary concern is protecting sensitive data across various environments, DSPM is the way to go.
On the other hand, if your focus is on securing cloud infrastructure and ensuring compliance with cloud-specific standards, CSPM is the better choice.
However, DSPM and CSPM are limited to data security because they do not evaluate the encryption standards applied to sensitive data.
Organizations must periodically check the strength of their encryption mechanisms to address the evolving landscape of cyber threats and vulnerabilities. Cybercriminals continuously develop new attack methods that can potentially bypass outdated encryption protocols.
Organizations need to know how well their data is encrypted and if there are any discrepancies with their policies or data security best practices. Regular evaluations ensure that encryption methods remain robust, compliant with the latest standards, and capable of safeguarding sensitive data against emerging threats.
The Fortanix Solution
Fortanix Key Insight addresses the challenges of data security and key management. It identifies keys and maps them to data services across a hybrid multicloud environment, providing users with immediate awareness of critical data security and compliance gaps. This enables organizations to improve their cryptographic security posture and use resources efficiently.
Check out the Key Insight product in brief and test your environment with a free trial.

 Cite this article
Cite this article









