Cloud-Scale Data Security Challenges
Enterprises nowadays seek everything - safe data and applications that can be accessed from anywhere, and from any device. Cloud computing technology is the perfect solution to achieve this flexibility, but there are many deep-rooted cloud computing security challenges to overcome.
The burning question here is what can enterprises do to realize the benefits of cloud technologies while balancing a secure environment for their most sensitive data? Accepting the problems is the first step toward finding practical solutions. The next step is to select suitable technologies and solutions to tackle these cloud security challenges.
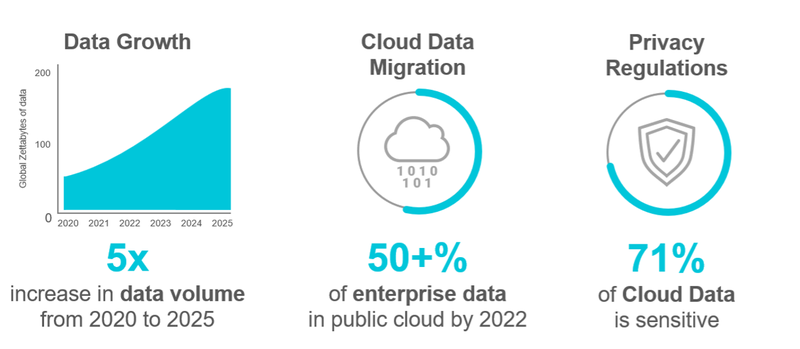
Fig1: Current Data Security Challenges in Multi-cloud environments
Cybersecurity risks and challenges in cloud computing are not overwhelming. Enterprises can benefit from cloud technology with the correct cloud service provider (CSP), next-generation technology, and due diligence.
What is driving Confidential Computing’s exponential growth?
Businesses and government agencies are looking for a new approach to keep their data safe in the cloud these days. Financial services clients, vehicle manufacturers, health insurance providers, and telecommunication service providers all require protection of their sensitive and regulated data, throughout its lifecycle.
Data privacy has become more critical than ever as a result of the worldwide pandemic, which has also driven adoption of public and hybrid cloud services. Strict compliance regulations, as well as a rising number of broader data protection rules, apply to specific industries, and represent an important concern for security and compliance professionals.
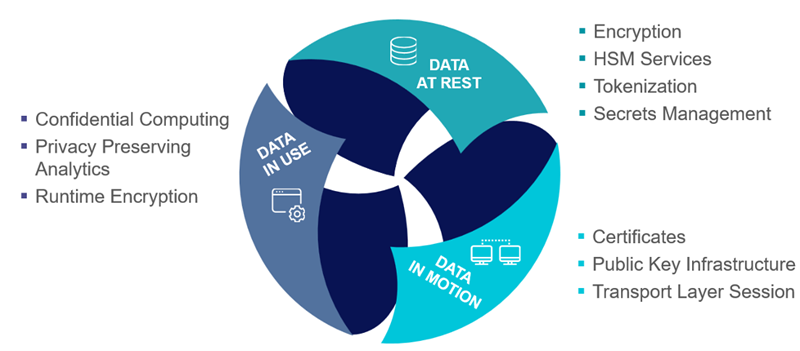
As a result, organizations in these industries must adhere to what IEEE Spectrum refers to as the “three pillars of data security”: data security at rest, in motion, and in use. These principles also apply to cloud computing security.
The first and second have been managed using encryption and tokenization, among other approaches, over the years. However, the last one has proven more challenging to achieve, particularly in the cloud. Data must be in plaintext in order for computation to take place.
As a result, attackers have the opportunity to dump the contents of memory and steal important data. And this is where confidential computing comes in, assuring organizations and leaders that their data in the cloud is safe and secure.
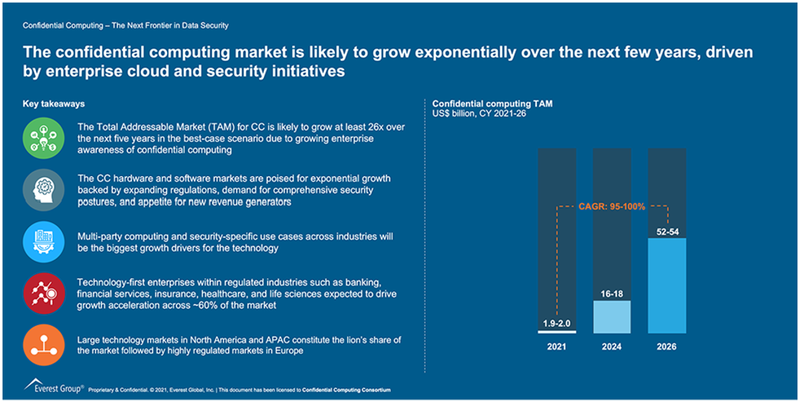
Fig2: Expected Evolution of Confidential Computing Market
Enablers for Confidential Computing
Confidential Computing is a rapidly emerging and generally available technology that protects data and applications in public cloud servers by isolating them fully within an encrypted memory space, called a Trusted Execution Environment (TEE).
Amazon AWS, Microsoft, Google Cloud, and other cloud providers, as well as the top CPU and server manufacturers, already support it.
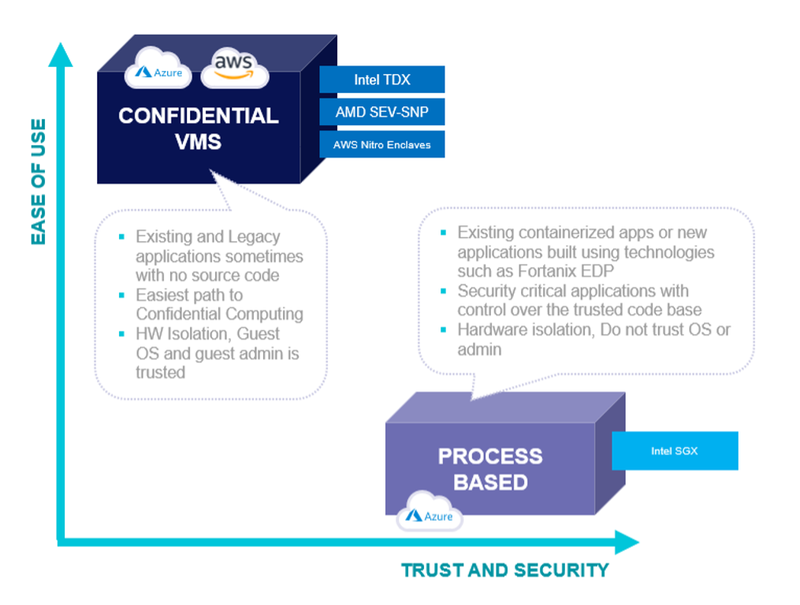
Fig3: Confidential computing relies on foundation technologies from Intel, AMD, and Amazon
Several significant IT companies, including Google, IBM, Huawei, Arm, Intel, Microsoft, Oracle, Red Hat, NVIDIA, Fortanix, and VMware, are members of the confidential computing consortium and have invested heavily in Confidential Computing, bringing new and creative solutions to the enterprise.
Some Critical Industry Relevant Confidential Computing Use Cases
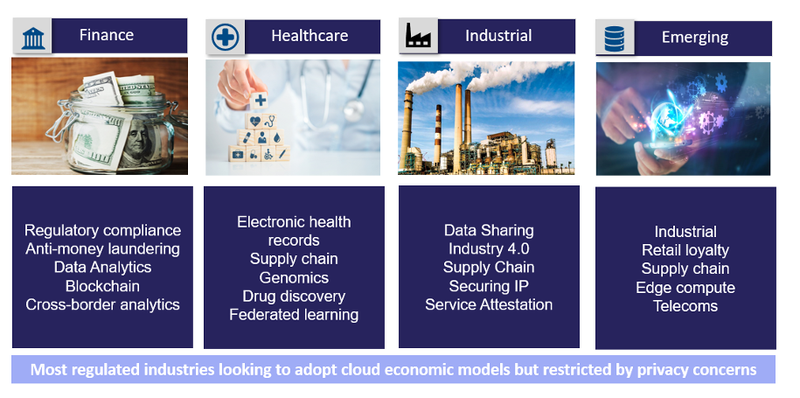
Fig4: Confidential Computing Use-Cases
Confidential computing primarily tries to give businesses more assurance that their data in the cloud is secure and private. It encourages businesses to use public cloud services for more sensitive data and computational tasks, safe in the knowledge that their data and applications are protected.
Because many edge and IoT devices must safeguard in-use data, confidential computing can be employed outside of the cloud as well.
Many cybersecurity specialists believe that this technology is the way of the future. In the near-term, the software landscape of new technology will be shaped by cloud computing paired with confidential computing, which provides data security benefits in use.
Confidential computing may become the de facto technology for computational security as a result of the necessity to safeguard and manage sensitive data throughout its lifecycle, as well as increasing legislation, and the expansion of cyber risks.
What makes Fortanix the market leader in Confidential Computing?
Fortanix® is the data-first multi-cloud security company. As the industry’s first and largest provider of confidential computing solutions, Fortanix decouples data security from infrastructure.
Fortanix solutions empower organizations with centralized controls to secure data spread across clouds, applications, SaaS, databases, and data centers. Over a hundred enterprises worldwide, especially in privacy-sensitive industries like healthcare, fintech, financial services, government, and retail, trust Fortanix for cloud security and privacy.
Recently Fortanix announced that it had crossed a significant landmark by booking its 100th Confidential Computing production customer (Press Release). Fortanix has played a prominent role in taking Confidential Computing out of the lab and into the sunlight. Fortanix offers the most complete solution for confidential computing – providing customers the fastest and easiest path to protect their applications and data while in use.
Fortanix is a founding member of the Confidential Computing Consortium of the Linux Foundation. The Confidential Computing Consortium (CCC) brings together hardware vendors, cloud providers, and software developers to accelerate the adoption of Trusted Execution Environment (TEE) technologies and standards.
Although cyber-attacks will keep on standing out as truly newsworthy, organizations can safeguard information all through its life cycle - rest, in motion, and in use.
It Isn’t a question of ‘If,’ It’s a question of ‘When.’
When businesses started their cloud excursions several years ago, early adopters didn’t rush things. For the most part, it was simply a matter of moving a few simple workloads to the public cloud.
However, we’re now in the second chapter of the cloud, and we’re trying to migrate the remaining workloads. This entails transferring sensitive data to the cloud while attempting to prevent the ransomware and other threats that plagued the cloud’s first chapter.
Additionally, confidential computing creates new commercial options. Without having to worry about the risks created by processing their data on third-party infrastructure, businesses can choose a cloud service provider that best matches their needs thereby also monitoring costs of their cloud setup.
Organizations can also collaborate with other businesses to develop innovative solutions without revealing intellectual property or other sensitive information in the process.
Running workloads in secure TEEs allows for entirely new security requirements to be implemented, preventing breaches, viruses, malicious insiders, and hackers.
By applying this to cloud infrastructures, businesses may utilize the cloud almost like on-premises resources if they operate everything using Confidential Computing – because no one, including the cloud providers, has access to your data or code, removing the need for trust.
This could become the key use case for Confidential Computing in the next years, affecting how businesses set up their IT architecture and we will definitely see more businesses shifting toward this exciting technology now that it is available, at scale, within public cloud infrastructure.

 Cite this article
Cite this article








