Sensitive data is spread across multiple silos—on-premises, in private clouds, and on public cloud platforms like AWS and Microsoft Azure. However, despite implementing the best encryption mechanisms, security and compliance teams often face a significant challenge: they lack visibility into how and where encryption is applied.
There are several reasons.
A) The Silo Problem: Multiple Environments, Fragmented Security
Hybrid multicloud environments allow organizations to optimize their IT infrastructure for performance and cost but also introduce complexity. Encryption silos arise when different environments—on-premises, private, and public clouds—each manage encryption independently.
As a result, security teams have no unified view of how encryption keys are deployed, what type of encryption is used, or whether encryption policies are followed consistently across all platforms.
This fragmented view poses a severe risk. As the saying goes, "You can't protect what you can't see." If security teams don’t know where encryption is applied or whether it aligns with regulatory standards, they can’t effectively manage data protection.
This is not just a best practice—a cryptographic inventory is a mandate of the PCI-DSS 4.0 standard, which will go into effect in May 2025.
B) Bridging the Gap Between DSPM and CSPM
While many organizations use Data Security Posture Management (DSPM) tools to classify sensitive data and Cloud Security Posture Management (CSPM) solutions to identify configuration security issues, neither provides full visibility from encryption perspective.
DSPM can tell you how sensitive your data is but not how or how well it’s protected. CSPM identifies cloud misconfigurations but doesn’t solve the problem of cryptographic security across hybrid environments.
The Importance of an Encryption Inventory
Security teams must understand where encryption is used and how effectively it is applied. This inventory should provide details such as:
- What data services use encryption?
- What types of encryption keys are being used?
- How are these private key stored, and are they rotated frequently?
Without this information, organizations are flying blind, leaving gaps in their cryptographic posture that attackers could exploit. These gaps become even more concerning with the rise of quantum computing, which threatens to break the encryption algorithms we depend on today.
Fortanix Key Insight: A Centralized Solution for Encryption Visibility
To address this cryptographic visibility challenge, Fortanix introduced Key Insight, the first solution in the market to scan across hybrid multicloud environments. This groundbreaking capability helps organizations discover, assess, and remediate risks tied to their cryptographic posture, giving security teams the insight they need to future-proof data protection.
How Fortanix Key Insight Works
Key Insight automatically identifies all encryption keys and data resources used in on-prem infrastructures, or AWS and Microsoft Azure environments. It doesn’t stop at discovery; it also assesses your cryptographic posture by analyzing your encryption risks and if your posture aligns with established policies. This assessment helps prioritize the next steps to remediate the highest risks, allowing security teams to focus their efforts where it matters most.
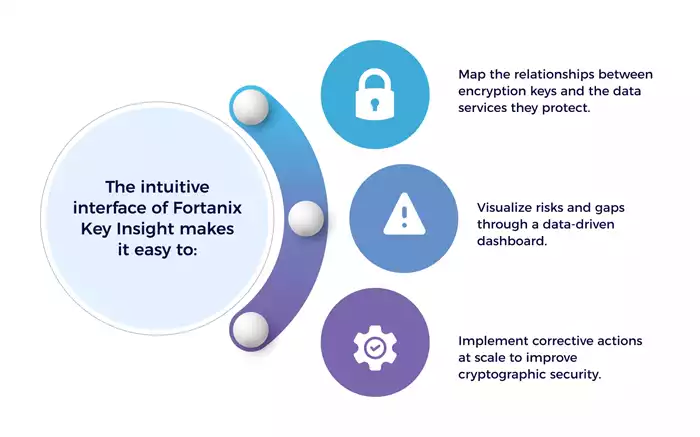
Fortanix Key Insight helps with:
1. Discovery: Automatically identifies all encryption assets and maps the relationships between encryption keys and data services.
2. Assessment: An easy-to-read dashboard provides data-driven details and immediately helps define the biggest data security risks and prioritize remediations.
3. Remediation: Prioritize next steps and implement corrective actions at scale with Fortanix DSM.
Preparing for the Future: Quantum-Resistant Encryption
One of Fortanix Key Insight's valuable use cases is its ability to help organizations prepare for the post-quantum computing era.
Quantum computing is expected to advance to a point where it could break the current encryption algorithms, potentially exposing sensitive data. Key Insight provides an inventory of cryptographic keys, assesses their vulnerability, and helps prioritize which keys and workloads need to transition to quantum-resistant algorithms. This proactive approach helps organizations thwart “harvest now, decrypt later” attacks.
Conclusion
Visibility becomes challenging when encryption silos exist across hybrid multicloud environments. Fortanix Key Insight is the first solution in the industry to address this problem by providing complete visibility into an organization’s encryption posture. With Key Insight, security teams can discover where encryption is applied, assess the strength of their cryptographic defences, and take action to remediate any weaknesses—both now and in preparation for future threats like quantum computing.











