Why do companies like Apple and Google push mobile app makers and websites to adopt basic encryption or be penalized in web searches and the Apple App Store?
Because without encryption, data can — and will be vulnerable to data loss and security breaches.
Companies such as Apple go beyond selling products and services. They sell you trust—trust in a device’s ability to keep your data private. These businesses unfeignedly believe that encryption is one of the most efficient ways to secure your data—even from the tech companies themselves.
The ‘Key’ to Successful Encryption
Cryptographic operations, such as data encryption, decryption, and user authentication, are built on the holy grail of robust Enterprise Key Management (EKM). Even a single compromised cryptographic key can derail a company's data security efforts.
What is An Enterprise Key Management System?
An Enterprise Key Management System (EKMS) manages cryptographic keys across an organization's IT environment. It handles the full lifecycle of keys, including their generation, distribution, storage, rotation, and revocation, ensuring they are securely managed and protected.
EKMS provides centralized control and visibility over all cryptographic keys. This helps organizations enforce security policies, meet regulatory compliance requirements, and protect sensitive data from unauthorized access. With EKMS, organizations can also automate key management processes, which reduces the risk of human error. Automation improves the overall security of encryption practices across various systems and applications within the enterprise.
The Crypto Sprawl
Why is there a need for Enterprise Key Management Solutions?
A recent survey states that 71% of organizations are unsure about how many keys & digital certificates do they have. Much of it can be attributed to the vast key sprawl that most data-driven company face.
You got SSH keys, Symmetric keys, PAM, Code Signing Certificates that your developers are working at, with something like a secret management tool, and then the common ones like SSL/ TLS certificates. Then there are the ghost keys or orphan keys.
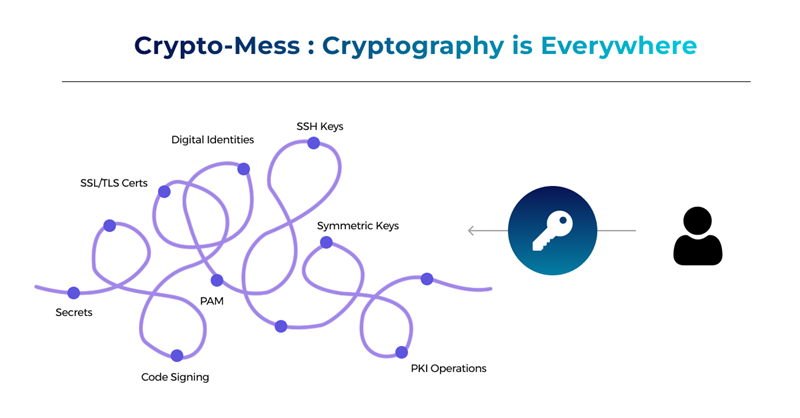
So how do you take all these keys and manage them across devices, environments, VMs, and containers? Adding to the complexity is the fact that your encrypted data is spread across multiple CSPs—each with its own set of keys.
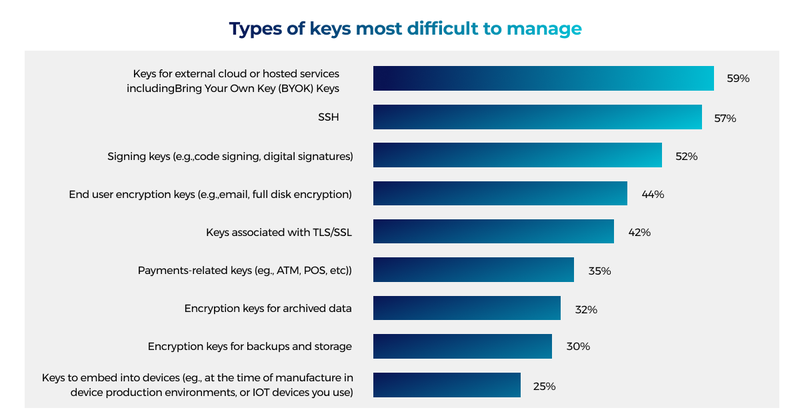
Then there are diverse cryptographic assets with different levels of management complexities. According to a recent survey, businesses ranked keys for external cloud or hosted services as the most difficult to manage—followed by SSH and Signing keys. All in all, there is a pressing requirement for a centralized enterprise-level encryption key management system.
Limitations of Current Key Management Systems
Irrespective of its criticality, even the most high-value keys are distributed across disparate systems and geographies, generated and consumed on different devices—and have differing schedules for rotation and replacement.
Surprisingly, many businesses still rely on something as minimal as spreadsheets to handle the who, what, where, and when of these keys. Yes, spreadsheets! Let that sink in!
Then they face the persistent challenge of scaling these solutions from on-prem to complex cloud environments. If that wasn’t enough, they need highly skilled staff to work on these sensitive but very repetitive task.
Lastly, there is the looming fear of whether the KMS will integrate with the deployment models and architecture of their applications or products.
What businesses need is a centralized key management system that can deliver:
- A single place to define EKM policy
- A single place to manage all keys
- Standard protocols for EKM services
- Platform and Application-independent
- Scalable to service millions of clients
- Available even when network fails
- Extremely secure
Why Should You Care?
Increased Flexibility: For businesses with multiple CSPs across varied geographies, enterprise encryption key management solutions can be a single centralized repository where key management and specific security policies and requirements can be customized.
Enhanced Data Control: Historically, businesses did not own the encryption keys for their cloud data—it remained with the CSPs. This practice hands over a worrisome level of control of their sensitive data to a third-party. This is especially concerning for highly regulated industries such as healthcare and finance. Having an enterprise level key management system in place mitigates that dependency.
Compliance: As we said earlier, most regulated industries rely heavily on encryption and in turn, on key management. An enterprise key management system enables organizations to implement the necessary processes and controls around their keys and simplifies internal and external audits. Thus, helping them remain compliant with various industry specific, national and/ or international standards including PCI-DSS, GDPR, SOX, HIPAA and many others.
Cost Reduction: Having a KMS in place helps you save costs on various front by
- Minimal redundant manual processes
- Minimize human mistakes and inaccuracies
- Centralizes operations to optimize the use of skills and resources
- Process automation
- Scalability to accommodate growth
- Reduce time spent on compliance and audits
Minimized Impact of a Data Breach: Enterprise Key Management tools mitigate breach risks by rendering the data useless and unreadable. The key remains inaccessible to hackers and other unauthorized entities.
And considering the average cost of a breach, this aversion translates into huge cost savings, preventing companies from enduring the potential compliance fines and lost business that a breach can create.
Risk Reduction:
- Role-Based Access controls
- Secure key distribution to protect ‘in transit’ keys
- High quality key generation to avert the use of weak keys
- Physical protection of keys against theft and misuse
- High availability with guaranteed SLAs
- Automated key rotation to ensure key material is not compromised through overuse
- Key revocation and deletion to allow compromised keys to be taken out of service
- Usage and audit logs
Parting Thoughts
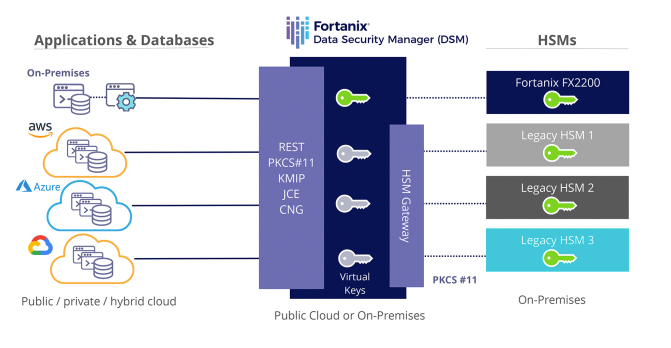
The Enterprise Key Management Solution by Fortanix Data Security Manager facilitates unified management of keys, encryption, tokenization, and secrets management across multi-cloud and hybrid infrastructures.
Key Management Service (KMS) with HSM grade security allows organizations to securely generate, store, and use crypto keys, certificates, and secrets. It provides control and visibility into your key management operations using a centralized web-based UI with enterprise level access controls and single sign-on support.
Fortanix also supports multi-geo deployment and is built to scale horizontally and vertically, with automated load balancing, fault tolerance, disaster recovery, and high availability. Business critical apps can integrate using traditional crypto interfaces or restful APIs. All of it secured with Intel SGX—built for cloud scale and resiliency.
Is your business planning to invest in enterprise level encryption key management system? Do you wish to understand what works best for your cloud security? Looking to speak to an expert? Our specialists would love to hear you out and assist you.
Looking for other cloud security solutions but have budget constraints? Not sure where to start? Why not start with our explorer pack? Industry leading data security capabilities, free of cost.

 Cite this article
Cite this article









