As governments around the globe proactively promote digital payments, aiming to bring various tax collections under the digital payment ecosystem—digital transactions are soaring at unprecedented levels.
I’ll let the numbers do the talking.
In FY23, India's Unified Payments Interface (UPI) platform clocked over 84 billion transactions, accounting to about Rs 139.09 trillion [source].
The advancement in the United States is similar. Over the past five years, the number of Americans who prefer going "cashless" has risen remarkably. 41% of Americans said they did not use cash for their purchases in a typical week in 2022, up from 29% in 2018, according to a Pew Research Center survey [source] released last October.
But there is another side to that story
According to Flashpoint, the number of consumer records exposed in breaches globally surpassed 254 million this year. In the U.S. alone, the Maine Attorney General's data indicates that around 9.4 million [source] consumers nationwide were affected by data breaches against financial companies.
This trend of customers' payment information getting compromised is not new. Even before digital payments were mainstream, headlines such as Home Depot's 56 million customer card data breach [source] or the Neiman Marcus incident [source] of 1.1 million credit card data being leaked were far from being rare occurrences.
So, what's the conclusion we can draw from these statistics?
Offline, Off-Guard, and Obsolete
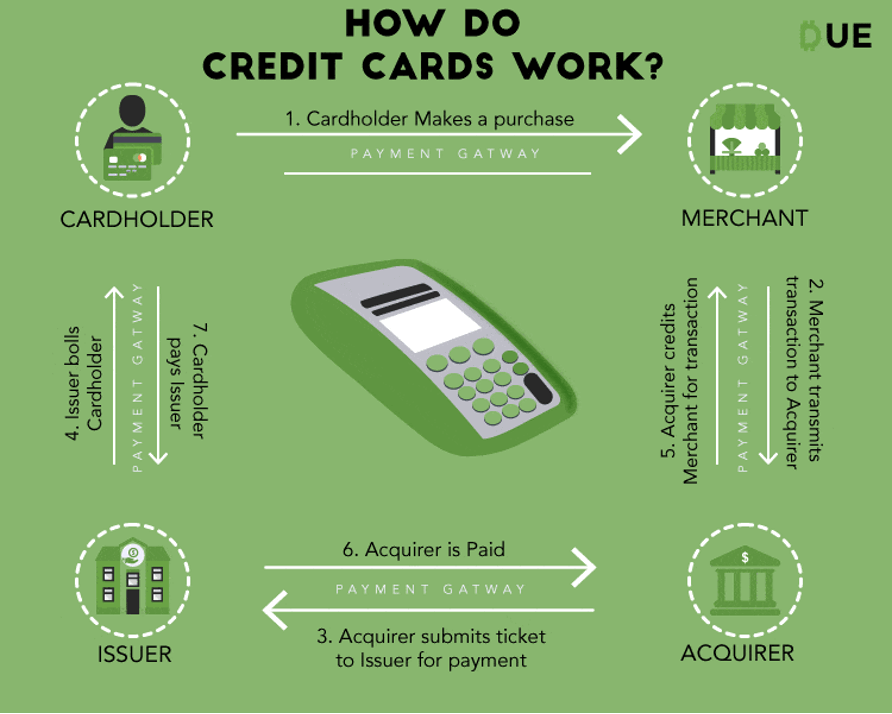
Let's understand what happens when you use your credit card to make a payment.
When you swipe your credit card at a retail store, your data gets stored on a system that usually runs on obsolete OS or old-school Point-of-Sale software. The payment software, which takes care of credit card processing, whether a separate application or integrated into the POS, is typically installed on the same physical device and shares the same computing resources with the POS and other Windows applications.
To carry out transactions, the payment software must interact with the payment terminal, point-of-sale system, and payment processor, leading to a continuous exchange of sensitive data. This constant circulation puts the data at risk of being compromised.
Digital payments, conversely, are often deemed safer than offline payments—thanks to advancements in demographic shifts, payments technology, and the evolving cyber-security landscape.
However, security concerns exist whether you are online, offline, or on a mobile device.
The security protocols put in place by the major credit card companies were initially intended for safeguarding data at rest. That is no longer the world we live in, and these standards no longer adequately guarantee the protection of consumers' information.
The need of the hour is to overhaul obsolete practices and get in line with a cloud-first digital world.
Credit Card Data Tokenization— The Cornerstone of Digital Payment Security
52.3 million cards across VISA, Mastercard and RuPay [source]—that is the number of cards that Indian fintech giant PayTm had tokenized last year to fall in accordance with the Reserve Bank of India’s deadline to purge saved card data.
PhonePe, another payment gateway company, tokenized 14 million debit and credit cards [source] as of September 2022.
So, what’s the fuss about credit card data tokenization?
Credit Card Data Tokenization has emerged as one of the most effective and secure ways to address multiple use cases surrounding identity proofing or payments. The principle is quite straightforward:
The original card data is substituted by a non-sensitive, arbitrarily generated equivalent, known as a token—which holds no mathematical relationship with the actual card data. Moreover, no key can “reverse them” to the actual information.
Data Tokenization of credit cards enhances the security of user data, safeguarding the cardholder against fraudulent activities. It is a fundamental enabler for various digital payment scenarios, encompassing both in-person and online transactions.

Offline: Upon making in-store purchases using a smartphone to conduct payments through platforms like Samsung Pay and Apple Pay, or even certain Issuer Pay (a service established by banks with their in-house digital wallets), what gets sent from your device to the merchant is a token—instead of your actual card information.
Online: Similarly, for recurring online payments, what gets stored on the merchant’s website are the tokens and not the actual card information. So, even in case of a breach, what the intruder gets his hands on are the tokens that carry no actual value and cannot be reversed to get credit card credentials.
Credit Card Payment Data Tokenization Benefits the Payments Industry in Multiple Ways
Enhanced Data Protection and Security
As businesses wade through legacy application modernization, and remote work becomes more mainstream, the risk and impact of a data breach is steadily rising. Data Tokenization helps merchants and banks secure data at rest, in motion, and during processing.
When merchants and banks store tokens instead of real user data in their POS machines, mobile wallets, and eCommerce platforms—their security stands tall even in case of a breach.
Abiding by Regulatory Compliance
Any entity that holds, handles, or transfers user credit card information is obligated to adhere to the guidelines outlined in the Payment Card Industry Data Security Standard (PCI DSS).
Data Tokenization offers an economical method of aligning with regulatory requirements. It effectively eliminates four compliance clauses from PCI for merchants, thereby diminishing their operational expenses.
PCI Requirement 1 –Install and maintain a firewall configuration to protect cardholder data
PCI Requirement 3 –Protect stored cardholder data
PCI Requirement 4 –Encrypt transmission of cardholder data across open, public networks
PCI Requirement 9 –Restrict physical access to cardholder data
Easy Card Management
In the case of recurring payments, customers are relieved from manually inputting sensitive details for each transaction. Tokens produced from your Mastercard are exclusive to a particular card with a specific merchant. This approach eliminates the danger associated with storing card specifics on the internet and ensures the uncompromised convenience of storing your token details on the merchant site.
Fortanix Data Tokenization/Format Preserving Encryption
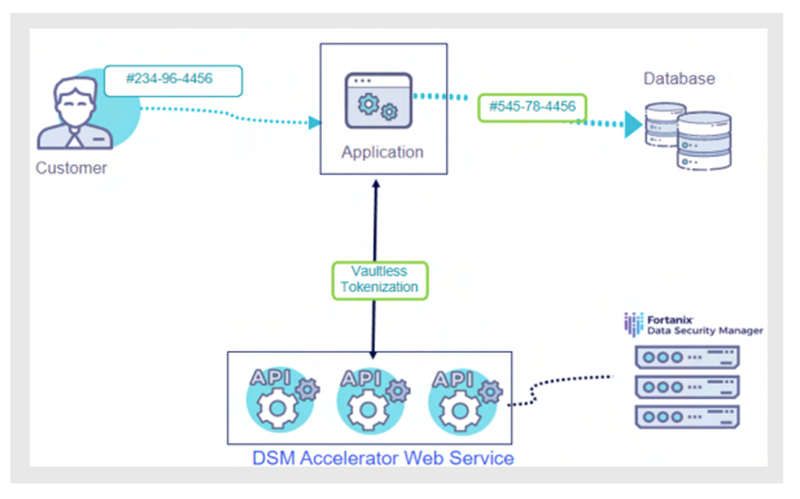
Fortanix DSM provisions a secure, scalable data tokenization solution for enterprises looking to protect their sensitive data and comply with privacy and security regulations— delivered via a unified data security platform. Figure 1 shows data tokenization of a social security number using vaultless data tokenization with DSM Accelerator.
The application integrates with the DSM Accelerator through REST API to perform vault less data tokenization. The data tokenization keys are cached for a set TTL (Time to Live) duration by the DSM Accelerator.
The main benefits of data tokenization using Fortanix include the following:
- Granular Data Access Control: The combination of Format-Preserving Encryption (FPE) and Role-Based Access Control (RBAC) strengthens the protection of sensitive data. With Fortanix as a centralized platform, authorized identities such as applications and users get a unified workflow to authenticate, query, and tokenize data, regardless of the application or user's location.
- Safe Data Sharing: Fortanix offers vaultless data tokenization that is more secure and simpler to manage. The platform provides FIPS 140-2 Level 3 compliant HSMs (Hardware Security Modules) to protect the keys for tokenized data—eliminating the need for a centralized token database. In addition, organizations can safely expose select data sets to third parties or developers for data analytics or with support staff to verify end-customer identities.
- Simplified Regulatory Compliance: Application developers can access the Fortanix platform from any location to dynamically mask sensitive data like credit cards or social security numbers to achieve PCI-DSS compliance and add a layer of security. Similarly, developers can apply HIPAA (Health Insurance Portability and Accountability Act) regulations by substituting electronically protected health information (ePHI) and non-public personal information (NPPI) with a tokenized value.
If you want to learn more about our Data Tokenization capabilities. Download this whitepaper.
Is your business planning to invest in a Data Tokenization Solution? Do wish to understand what works best for your Data security? Looking to speak to an expert? Our specialists would love to hear you out and assist you.
Looking for cloud security solutions but have budget constraints? Not sure where to start? Why not start with our explorer pack? Industry leading data security capabilities, free of cost.
Related Read: CISO Melbourne Summit - Enhance Data Security Solutions with Fortanix

 Cite this article
Cite this article









