According to IDC, 2021 will be the year of multicloud as the pandemic reaffirms the critical need for business agility. Business is all about speed. Every organization today is focused on building an infrastructure that can enable them to innovate at speed and stay ahead of the competition.
And that is the big reason why multicloud adoption is becoming a growing trend. The IDC CloudView Survey highlights that the average number of cloud vendors used by the respondents is an average of 5 for an organization.
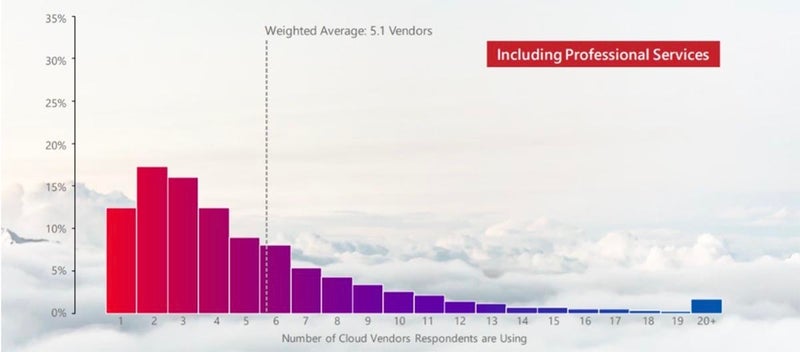
Gartner predicts that by 2021, over 75% of midsize and large organizations will have adopted a multicloud or hybrid IT strategy.
Data Security Challenges of Multicloud Adoption
Even though a multicloud environment allows businesses to distribute the risks and avoid vendor lock-ins, it also comes with some serious security downsides and challenges.
These are some of the areas that CISOs have identified as the most challenging in adopting a multicloud strategy:
It is challenging to apply a unified framework for data control, access, and security policies across multiple clouds.
There are plenty of tools and processes that can play a role in securing data in the cloud, but most organizations rely on encryption and key management as the primary method to protect data.
And in today’s data-driven world, it’s best to rely on a method that focuses on the data itself.
Cloud service providers (CSPs) offer native built-in cloud encryption and key management capabilities which can offer some level of security, control, and visibility for the data being used in applications specific to the CSP.
But with multiple CSPs, setting up uniform encryption policies across clouds for databases and applications needs to be done on each CSP which is manual and time-consuming.
Data usage by application also needs to have secure control and policy management which may be difficult to achieve with the CSPs.
The Healthcare industry is a great example. With stringent privacy regulations like HIPAA, healthcare providers are often required to create specific policies to control data access, but most of the time if the data is spread across different cloud providers applying a uniform framework for data access and control is complex and manual.
Enterprise workflows on different clouds mean a lack of visibility into data flows and security loopholes.
Enterprise users are increasingly using SaaS applications from different vendors, and it is becoming difficult to track the data flows across different cloud providers with each cloud having a different set of security and data governance policies in place.
This often creates security loopholes like malicious insider thefts, misuse of data, shadow IT, advanced threats like DDoS, etc.
And most organizations do not have a sound strategy to plug these security loopholes and challenges with a multicloud environment.
Here are 5 tips to bolster your multicloud data security:
As stated by Gartner, the best method to create a strong security framework for your data across multicloud is by applying consistency in policy creation, management, and configuration.
-
Implement a Unified Key Management System (KMS): All cloud providers offer a key management service (KMS). But when it comes to a multicloud environment it’s best to rely on a single, unified solution to manage data security across multiple cloud platforms including Amazon Web Services (AWS), Google Cloud Platform, and Microsoft Azure. A customer-controlled Key Management System that can extend to a native cloud platform and provide consistent encryption key management policies across CSPs, tenants, and regions is required. This gives organizations the much-needed flexibility by efficiently managing keys, secrets, and tokens across public clouds from a single, unified platform.
-
Separate the cloud keys from the cloud data they protect: It is not secure to store encryption keys in the same location as the encrypted data. If cloud provider insiders or cybercriminals gain access to those keys, they can decrypt data stored in the cloud leading to a data breach and violation of privacy regulations. It’s best for customers, not cloud providers, to have control of their encryption keys and their data by separating the cloud keys from the cloud data they protect.
-
Get a ‘single pane’ view into the data flows: Being able to monitor multicloud key management operations and author cryptographic policies from a centralized console helps with an audit trail to prove compliance with regulations. And if you have integrated your Key Management System with SIEM tools like Syslog, Splunk, or CSP logging, then you can get enhanced protection and deep visibility into the data activity through the audit logs of these external tools.
-
Enforce encryption key access controls based on zero trust: Enterprises need to properly manage user access to the cloud data. Single sign-on is required more than ever. It helps with establishing the identity of a user and sharing information based on which subsystem needs access to the data. Integrating the KMS with a single sign-on is crucial. The KMS should offer role-based access control (RBAC) and further fine-grain access control at the key level. Documenting and implementing which roles can access the KMS, what functions can these roles execute (generation of keys, destruction of keys, rotation of keys, etc.) is most needed. A more granular user and group level access should be defined at a key level.
-
Encrypt your data in rest and transit and also data in use with Confidential Computing: Even if you encrypt data in rest, in storage, and in transit, applications and sensitive data continue to be vulnerable to unauthorized access and tampering at runtime. Confidential computing protects data and applications by running them in secure enclaves that isolate the data and code to prevent unauthorized access, even when the compute infrastructure is compromised. Protecting the data in use is critical to offer complete security across the data lifecycle. There are advanced and integrated key management and data security platforms that enable applications to run within secure enclaves or trusted execution environments and offer encryption for the data and applications in use.
It’s critical for organizations to reinforce their multicloud data security. Cloud-native data security functions have created siloed islands of disparate data security policies that are complex to manage and increased the risk of data breaches.
A more consistent approach needs to be adopted by relying on uniform management of your multicloud data encryption keys.

 Cite this article
Cite this article








