The Problem
Code signing using digital certificates is the most effective way to attest that the software is not malicious. Keeping code-signing certificates secure is therefore critical for business continuity. Organizations must safeguard the cryptographic keys used to secure the certificates across networks. For example, end-users trust code-signing certificates, certified by the Root Certificates in their Trust Store. However, a compromised private key can sign trusted software until the certificate is revoked. Revoking is not always possible or practical.
Managing these keys and certificates creates operational complexity, especially with software development practices like using CI/CD pipelines, where software updates happen continuously, sometimes as frequently as multiple times per hour. Developers need centralized and simple access to keys for code signing, as using multiple, proprietary key management solutions results in key sprawl, making it difficult to track and secure them.

Fortanix Solution
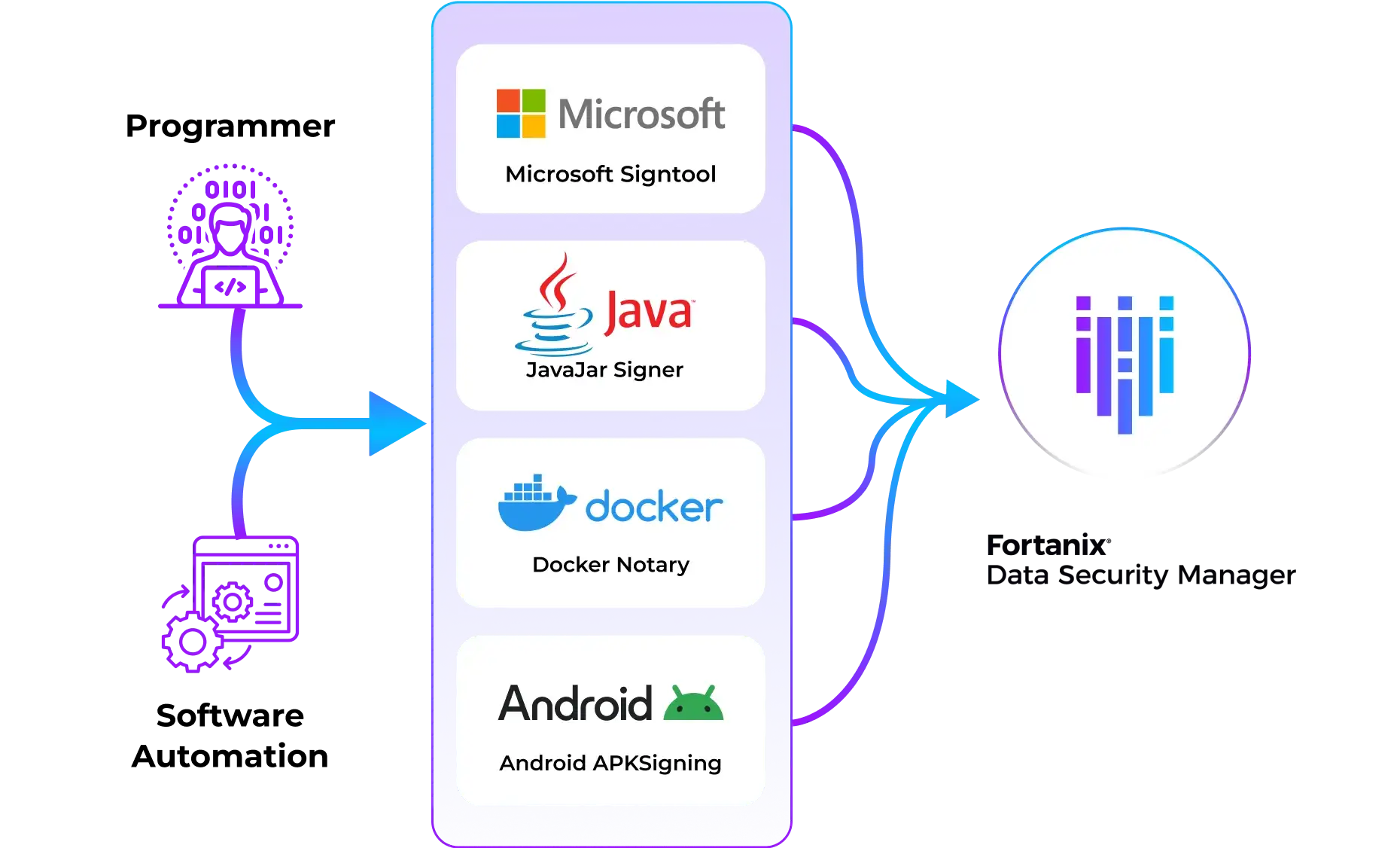
Fortanix Data Security Manager (DSM) is a unified platform that delivers comprehensive security and support to manage cryptographic keys and certificates for many leading code signing tools, including the Microsoft SignTool, Java JarSigner, Docker Notary, and others.
Secured by FIPS 140-2 Level 3 certified HSMs, the solution supports all types of asymmetric keys, signing, and hashing algorithms used for code signing, including post-quantum encryption algorithms. Role-based access control (RBAC) for users, applications, and groups provides authorization and separation of duties. Using plugins in DSM SaaS, large enterprises can verify the metadata associated with the signed data and control the use of keys.
Benefits

Quorum approval provides an extra layer of control and protection and prevents a single user from taking high-impacting administrative actions such as disabling or deleting critical keys. Such actions may require approval from multiple administrators to take effect. Compromised Code signing keys can affect operational processes in high-impact environments such as hospitals where medical IoT devices are critical for life-or-death situations and revoking certificates is impossible.
Integrate code signing processes with existing developer tools and workflows using DSM’s REST APIs, or using legacy API client libraries (e.g. CNG, JCE, PKCS#11). DevOps can let their app signing tools access keys and certificates from any location without delays and disruptions. DevOps organizations can enforce granular control options for various signing keys used throughout the development cycle. For example, they can assign different keys and certificates for testing (CI), and for deployment (CD), with distinct authorization requirements.

Tamper-proof logs help organizations audit and track the usage of their keys and certificates, the strength of cryptography, and all code-signing activities. They can verify that only authorized developers or toolchains have used the code signing keys.
The Fortanix Difference

Unified platform for Data Security
A centralized SaaS solution to simplify and strengthen data security across hybrid and multicloud environments.

DevOps ready
Fortanix DSM easily integrates into automation workflows with REST API support.

Highly Secure
Granular access control, including quorum approval, for keys and certificates which stay safe in FIPS 140-2 Level 3 HSMs.
Resources
Here are some of latest news, blogs, resources, events, and more


















