Runtime Encryption® enables a fundamentally new level of security and privacy allowing organizations with sensitive workloads to operate in untrusted environments such as the public cloud and remote clouds.

Runtime Encryption® Overview
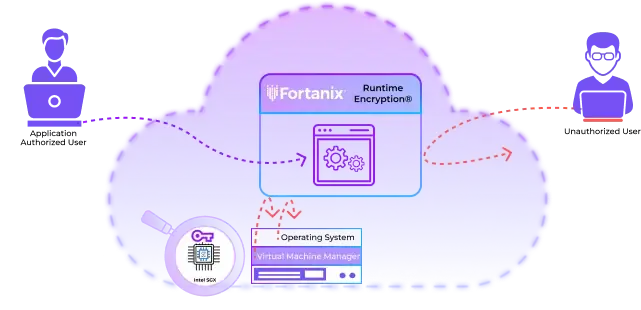
Encryption is an effective data protection control, however it’s use is currently limited to data at rest and data in motion. When, an application starts to run, it’s data in use is vulnerable to a variety of attacks including malicious insiders, root users, credential compromise, OS zero-day, and network intruders.
The holy grail of security has been to offer deterministic security to applications regardless of how the attacks originate. Runtime Encryption® provides deterministic security with runtime memory encryption for applications to protect data in use.
Protect your sensitive apps without modification

Deterministic Security
The Fortanix Runtime Encryption® platform leverages Intel® SGX to enable general purpose computation on encrypted data without ever exposing plaintext application code or data. Runtime Encryption® provides complete cryptographic protection for your applications, running it securely inside a trusted execution environment and protected even from root users and physical access to the server.

Easy To Use
Fortanix Runtime Encryption@ platform includes an EnclaveOS™ that transparently protects applications without requiring modifications. You can rapidly build protected application with no application developer burden or learning curve whether you have an existing application or are developing a new application. You can integrate with seamlessly with development workflows and orchestration tools for your agile environment.

Broad Application Support
Readily create complex yet secure applications such as 3-tier apps or scale-out distributed apps. You can seamlessly protect container-based services for your cloud-native apps. Commonly used apps such as Databases, Web Servers, Build Servers, Directory Servers, and Key Management are available protected out of the box.
Use Cases

Containerized Apps
Containers make applications portable, increase resource efficiency, and improve developer productivity. However, effective isolation is critical to mitigate security risks in a product environment. Fortanix Runtime Encryption® protects containerized applications during runtime from host-level attacks.

Secure data processing (AI, ML, Analytics)
Data scientists performing analysis or training machine learning models often require sensitive data as inputs. However, lack of strong security controls limits the sharing of this type of data. Fortanix Runtime Encryption® provides a security framework to ensure that the sensitive data remains protected even when in use.

Protected Microservices
Building blocks that are commonly used to create multi-tier distributed applications are available protected with Fortanix Runtime Encryption® . These include MySQL Database, NGINX Web Server, Directory Server, and Secrets Management.

Key Management
Encryption is an effective control to protect the data, however with encryption the risk transfers to the encryption keys. Fortanix Data Security Manager , leveraging Runtime Encryption® , delivers unmatched security ensuring only authorized users have access to the keys.









