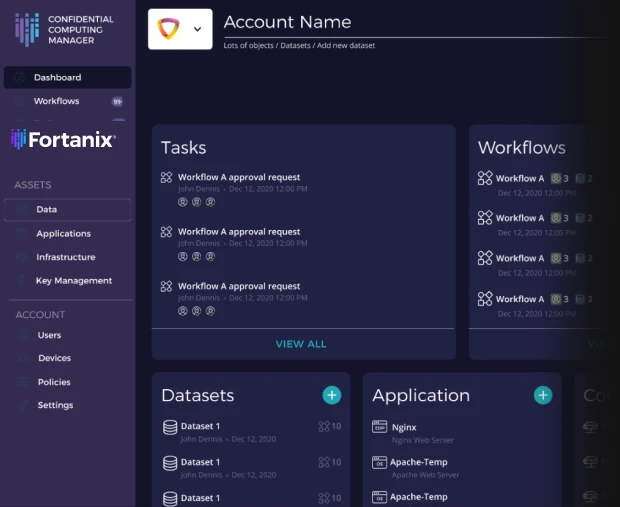
Protect Sensitive Applications and Workflows
Protect data and applications in an isolated runtime environment, encrypting data as it’s actively being used across your ecosystem.
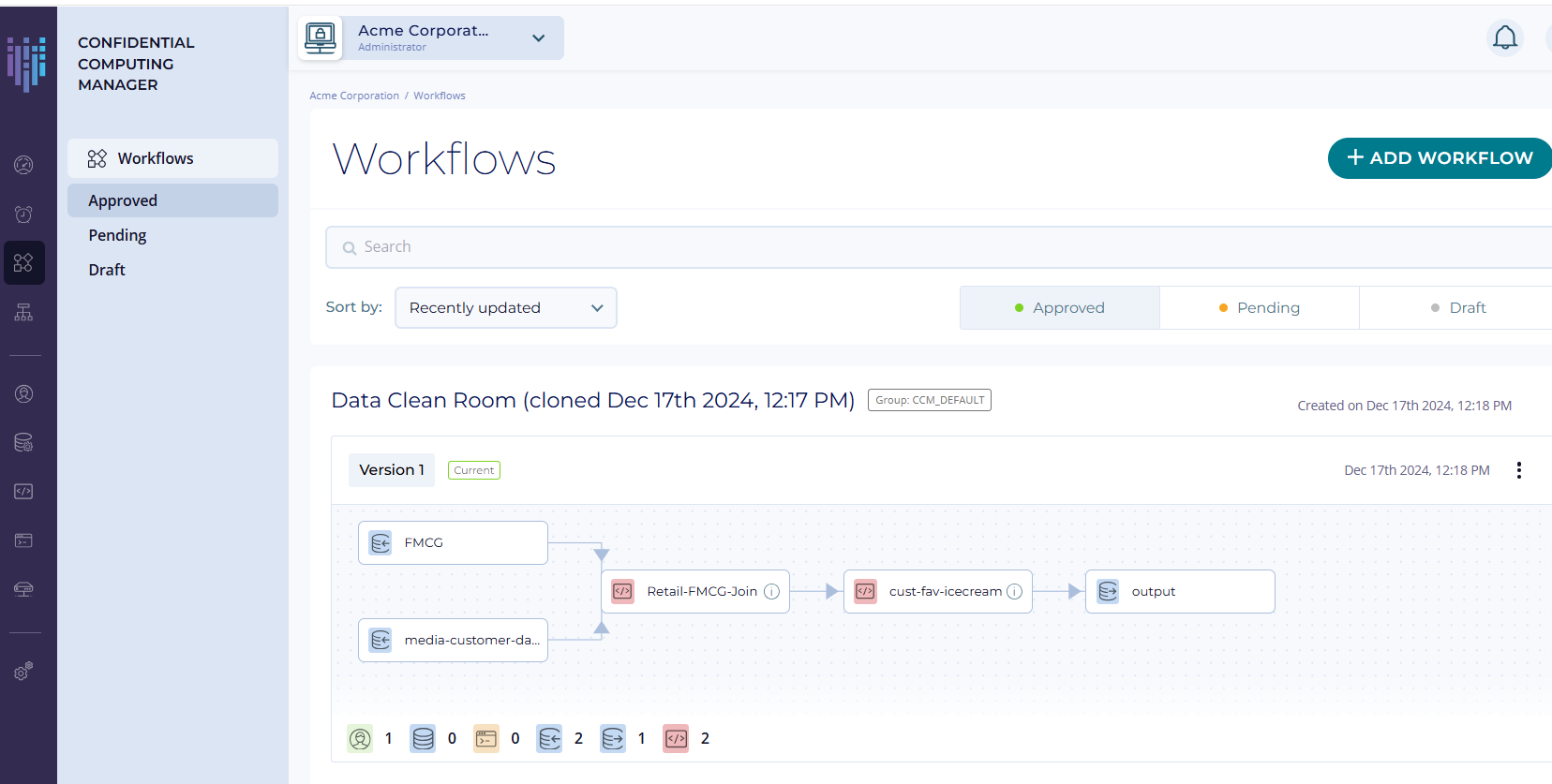
Securely Search Large, Complex Datasets
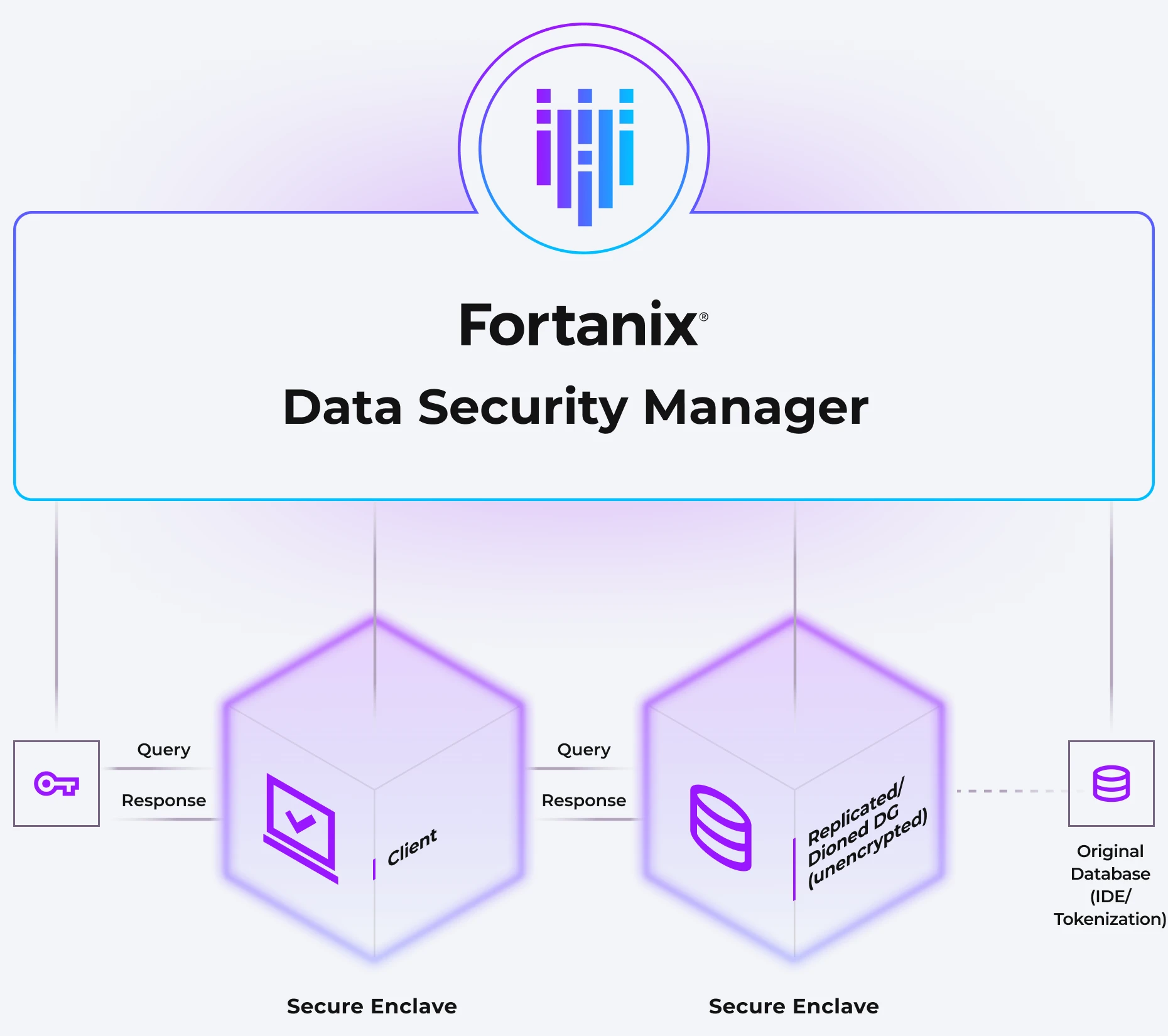
Use the power of confidential computing to replicate legacy and cloud datasets in a secure enclave, protecting data in-use while the database is decrypted. In contrast to homomorphic encryption, this method produces faster results without sacrificing security.
Enable Safe and Confidential AI
Safely use AI to grow and innovate and keep your sensitive data secure with confidential computing. your organization to the risk brought on by public, consumer-facing LLMs. Create a secure, on-demand work environment – infrastructure, software and workflow orchestration – that maintains the privacy compliance required by your organization.
Take Back Your Time With a Managed Platform

Without Fortanix

Simplicity

Complete low-code enclave lifecycle management on Fortanix.

Engineers must integrate multiple infrastructure components, manually configuring and verifying applications to run in enclaves.

Application support

Enable a combination of legacy, enclave-native, and pre-packaged applications to run in a secure enclave.

Developers must rewrite each application they want to run in a secure enclave using open-source SDKs, taking months and distracting them from core initiatives.

Security

Comply with regulations by enforcing all of your security policies, including identity verification, data access control and attestation to ensure the integrity and confidentiality of data, code and applications. Easily verify compliance with audit logs and attestation report.

Developers must build and maintain an in-house security solution at a large cost to the organization, including manually configuring all of the moving parts that confidential computing requires.