The Challenge
To enhance data loss prevention and comply with privacy regulations, businesses are constantly looking to strengthen their security posture. Many organizations now require that only authorized users with specific privileges can access data in plaintext within designated files or folders on a given filesystem. Aside from elevating security against cyber criminals, this approach also enables a clear division of responsibilities between data owners and system administrators, preventing malicious intents and careless human errors.
Encrypting individual filesystems comes with a significant challenge—management of the encryption keys. With each filesystem having its own encryption key, key sprawl is a reality and can easily get out of hand. Moreover, not properly managing and storing those keys increases cyber vulnerabilities and exacerbates the data security challenges organizations face.

Fortanix Solution
Fortanix Filesystem Encryption enables organizations to go beyond full disk encryption and protect individual filesystems mounted on a specified host. The Fortanix Enterprise Key Management solutions enable centralized lifecycle management for encryption keys across hybrid multicloud. Encryption keys are under complete customer control and secured by FIPS 140-2 level 3 certified HSMs, available as SaaS. Fine-grain policy-driven access controls restrict access to plain text data solely to authorized users and processes.
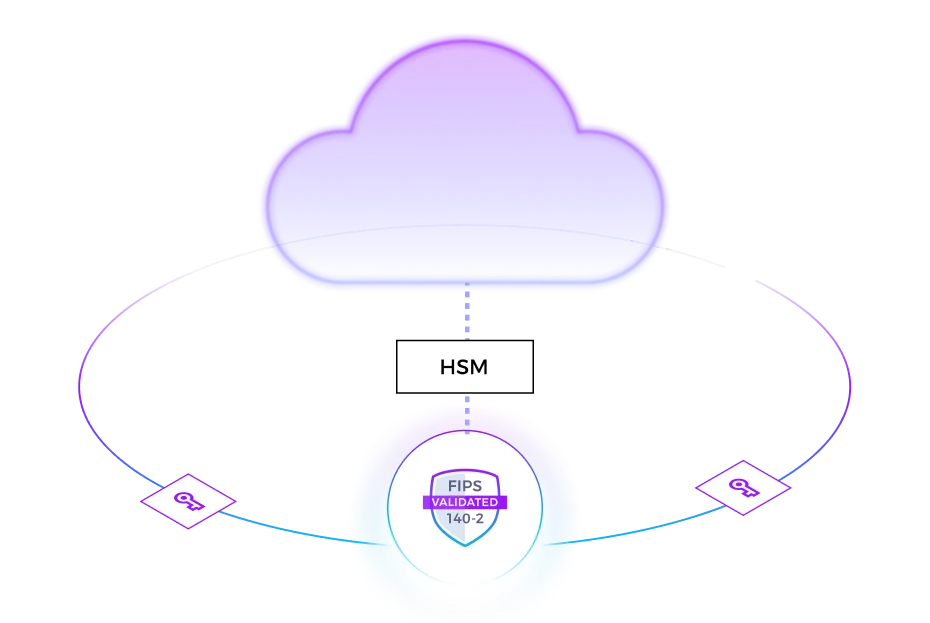
Benefits

Seamlessly set up and manage agents, based on Open Policy Agent specification with no kernel dependencies, to encrypt individual filesystems mounted on host machines. Scale across physical or virtual servers, compatible with Windows, Linux, and Unix platforms, without disrupting workflow.

Enjoy peace of mind with file-level encryption that continuously protects against unauthorized access in physical, virtual, and cloud environments. Apply granular encryption policies to ensure only authorized users and processes can access sensitive data in plain text.

Centralize lifecycle management of all encryption keys and apply policies from single pane of glass. Store keys in natively integrated FIPS-140-2 Level 3 HSM, available as SaaS or on-premises. Prevent involuntary or malicious key deletion with Quorum Approvals.
Key Differentiators
Immediately identify the most important risks, and drill down into the details.

Unified Data Security Platform
With a centralized solution, organizations gain complete visibility into what keys are in use and how human or machine identities use them. A thorough inventory of how your sensitive data is used and protected is fundamental to any security strategy.

Highly Secure
Identify how well your data is protected and how it aligns with current security policies. With an intuitive dashboard, Fortanix helps identify and prioritize where and when to apply new quantum-proof algorithms.

Scalable Performance
Fortanix enables organizations to own and control the lifecycle of all encryption keys. Crypto-agility accelerates the deployment of quantum-proof algorithm standards. Fortanix supports the latest NSA-recommended quantum-resistant algorithms and rapidly implements the latest NIST standards into its SaaS platform.
Resources
Here are some of latest news, blogs, resources, events, and more